Bedep
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 6,605 |
| Threat Level: | 60 % (Medium) |
| Infected Computers: | 4,722 |
| First Seen: | January 22, 2015 |
| Last Seen: | September 11, 2023 |
| OS(es) Affected: | Windows |
Bedep is one of the threat infections that is being used to take advantage of a zero-day vulnerability in Adobe Flash uncovered recently. A variant of Bedep is being used to infect computer users and profit at the expense of computer users. One alarming fact about these attacks is that the zero-day Flash vulnerability was implemented into the attacks less than a week after it was discovered. In the world of PC security, time is of the essence. Third parties being able to leverage a zero-day vulnerability so fast after its discovery, well before Adobe can release a patch fixing the vulnerability, is an alarming prospect and has made many people rethink current strategies used in cyber-security.
Table of Contents
The Harm Caused by Bedep and Threats Associated with these Attacks
Bedep attacks may involve corrupted advertisements inserted into advertising networks using various fraudulent practices. The Angler Exploit Kit had incorporated the Flash vulnerability shortly after its discovery and was using it to distribute Bedep. After the Black Hole Exploit Kit was mostly defeated in 2014, the Angler Exploit Kit has been on the rise, probably making it the likeliest successor to the infamous BlackHole. Bedep has also been associated with the Hanjuan Exploit Kit, which is used to connect affected PCs to the botnet in order to use them to carry out other attacks.
What is the Main Purpose of Bedep Attacks
The main purpose of Bedep attacks is to connect infected computers into a botnet. A botnet is a collection of infected computers that may be controlled by third parties in order to carry out coordinated attacks. Holding the power of hundreds or even thousands of infected computers, people may carry out a wide variety of threatening tasks using the victims' PCs, often without the computer users' knowledge. The following are some examples of tasks that may be carried out with a botnet:
- Botnets may be used to carry out DDoS (Distributed Denial of Service) attacks on specific websites. This means that the botnet may flood a Web page with requests in order to make it slow down drastically or shut down entirely.
- Botnets may be used to send out millions of spam email messages every day, often distributing other threats to unsuspecting victims.
- The power of a botnet may be leveraged to distribute or hide illegal activities, such as hiding pornography on unsuspecting computer users' PCs, laundering money, or using the computers in the botnet to anonymize a connection in order to hide from security researchers.
Bedep attacks may begin when a website that has been infected contains corrupted advertisements. These may be inserted using advertisement fraud routines or other threats that are used to compromise a specific website. These advertisements may be used to force computer users to visit attack websites containing exploit kits or to deliver Bedep directly. There are several reasons why Bedep has managed to maintain a low profile. In many cases, it has been unnoticed because Bedep uses advanced encryption. Bedep may also disguise its files as legitimate files to prevent detection.
Bedep and Zero-Day Security Flaws
The high number of recent zero-day vulnerabilities in cross-platform components such as Flash or Java has increased worries about current computer security models being possibly updated. Cybercrooks have gotten more efficient at leveraging these vulnerabilities, as can be observed by the quick adoption of these flaws to distribute Bedep in only a few days. This has made many computer security researchers consider that prevention in all areas may the key strategy in dealing with these threats in the future. Computer users can prevent attacks by ensuring that they are well protected with the best security software and an awareness of how these types of attacks work.
SpyHunter Detects & Remove Bedep
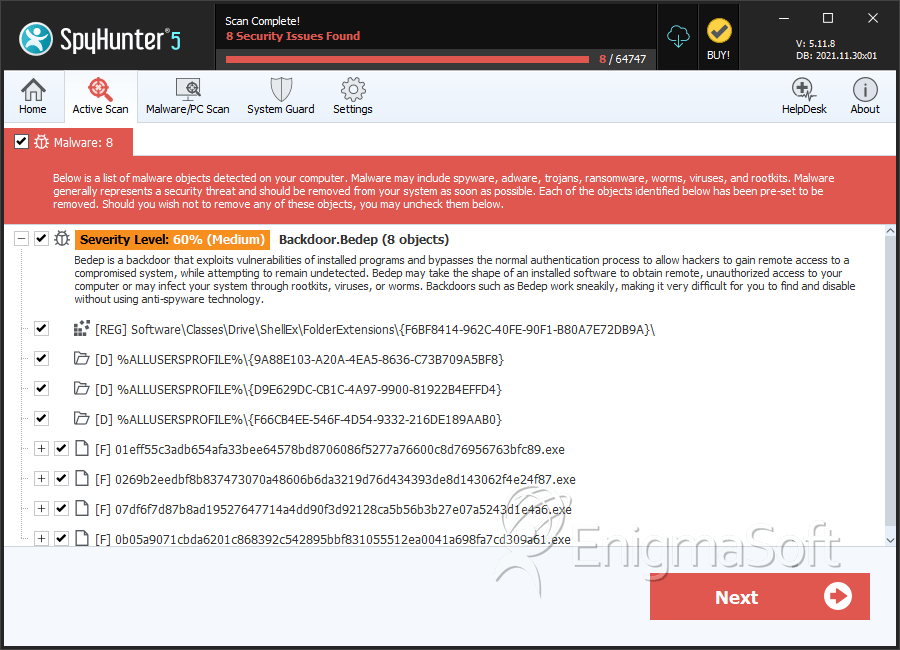
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 01eff55c3adb654afa33bee64578bd8706086f5277a76600c8d76956763bfc89.exe | d0aa4d1a826fd98303c488bdedde9c2a | 0 |
| 2. | 0269b2eedbf8b837473070a48606b6da3219d76d434393de8d143062f4e24f87.exe | 04ae37a5f36f34345e8d9eebbae75f13 | 0 |
| 3. | 07df6f7d87b8ad19527647714a4dd90f3d92128ca5b56b3b27e07a5243d1e4a6.exe | a942e048ddde617452aa208326a6f5e6 | 0 |
| 4. | 0b05a9071cbda6201c868392c542895bbf831055512ea0041a698fa7cd309a61.exe | 33e277c0a7ce79f145b30cd16ca1d097 | 0 |
| 5. | 121ba5f7b57d9c34ac0e810ba3d8bc260bf9203bd0d9b91a516b7d83e615b001.exe | aa24ac5e9ba18419d675dc5b3fb91e1c | 0 |
| 6. | 4cf3a689b6282a7b3b47309040f9d39a5b9189d59ac8a1d2d37936dfa5715f23.exe | 886599dcc08fcc8947237f4c755ee7ae | 0 |
| 7. | 51cfbc5a961745b635e48f252bd4b644cf47d0190c90d976c08c6251f3ee5add.exe | d0a9a1b70f2725acc38c473a2d3805f0 | 0 |
| 8. | 5cfc7667857c03e5bb43b4ea5436c86299adaab771f01695617a86caf4b64246.exe | e54e7d2323a16d7bc481cc19927d945f | 0 |
| 9. | 5fbf20d50b8bde8915016cb414392e885574592c7e673c6be1654796168414b2.exe | c6bdc9e1f594ca4f8134da9cb94f988b | 0 |
| 10. | 81326b5ea965383cebcea6ee6a4afd3faf912d4563f413b3a89948020142dca8.exe | 05de59e50b456f7b01237aa3e4c6340d | 0 |
| 11. | 8a8daa131de48f14f7ad9fece9ec734e167a9f35389e7f097d036ed6cafdcd4c.exe | 458ba0984ae8f6a7176f33442eaaadb7 | 0 |
| 12. | 93053d4261d0d9e0a832a48484d19af8205d4d686b15e4f2900256d9d82f4fd9.exe | a5235035ed1f18def64ee9b90a62f85c | 0 |
| 13. | 95525ee68803bc5cc3ee542a592cccf0053247c023c61bbd2775313658f827f0.exe | d288a4885a236b4fa7cbd3ca3a925dc3 | 0 |
| 14. | 9902b7243adce607399eff377d531a651625bfd01b5c324959f162847f1edf33.exe | c5ef964291627e83639bc475d7da44dc | 0 |
| 15. | 9b0d9aadc62c192b6fcff910caada118738c41f16f74e718a8c0171707250074.exe | a927a3d2ad3cbeb2e62262e8d3b3b47d | 0 |
| 16. | 9bf71590e07813df52989ea7eab146dffd9dce9ffe93aab40e3a8bacd40fc579.exe | 802c3cd2758654b7a73bea84659104d1 | 0 |
| 17. | 9eb5d30dbeed42f3bc6af0996e73d16ac81dc451c0a882091c3da9544eeaedfc.exe | 69d0047127c540ff68dbc8cec45b39b1 | 0 |
| 18. | 9ed94e4071e5dc740ba7b3e6da2a27bfc4236352eb5f3acea31ef2fcc459cae3.exe | 7e483b157e5ec3e80d2666cd03e989cb | 0 |
| 19. | b2e18acd6ba6937da5c49d18e868ea99f45e15557c773e7f45929fe6f6a4c98b.exe | 3983908ec5639ba900c4f0a31f7b35d7 | 0 |
| 20. | b31a370383308efab127cc0b5bb2a8161c5de232d8c48a9cfce2049568747aab.exe | d432041e281148d5fb3306c5a15f6f36 | 0 |
| 21. | be9ba85eef3c8f113a08aa127093020f901fe833d0540727bfd8fa390937c43f.exe | 98d7056200f1c43c9e9d0c2cd1e1b25c | 0 |
| 22. | cf57b3a289ad32d4ee6550d539a0bd8f2a031c0596fdc9240f8c26db02529e99.exe | ef2640a2bfa57a7ef281f815e9f98a2e | 0 |
| 23. | d662f3e7fe3ffb9f1ad8135eef93b01bdceff8ae693cffb8c2c4101a339dcdb8.exe | b4ce1ef1de0ea5354ec4c6cb3fd31f54 | 0 |
| 24. | ebc794719c35f3a714c1d34250b01786ab6d449103493337e2fdce81e2100aea.exe | d0a98fc66191f1c56add9f9accd97aa9 | 0 |
| 25. | f6242dd236ef360220ee5ef6b47c3a4c05f122fa681313e7c5e7734bcbf8b624.exe | 5df249e246f889b1d10a737728135cb3 | 0 |
| 26. | fbc36c1cd8b9e8885f894daba620bb97bd1bf3af527396edb7723e2f9f5f8a68.exe | e5d4caec558af692d7930d60f34f68ee | 0 |
| 27. | fe2e645776280d03def4afa7070952a34c234acd7e8d529bcd2e27511f5a312d.exe | 12a91cb80a5c38cf1d3dfd24fbc09430 | 0 |
Registry Details
Directories
Bedep may create the following directory or directories:
| %ALLUSERSPROFILE%\{9A88E103-A20A-4EA5-8636-C73B709A5BF8} |
| %ALLUSERSPROFILE%\{D9E629DC-CB1C-4A97-9900-81922B4EFFD4} |
| %ALLUSERSPROFILE%\{F66CB4EE-546F-4D54-9332-216DE189AAB0} |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.