AV Protection 2011 and other FakeScanti Variants Modify HOSTS Files to Redirect to Other Fake AVs
The FakeScanti family continues to evolve. Thanks to the BlackHole exploit kit, hackers can exploit flaws in legitimate software and spread any malware they want with ease. One exploit being executed by FakeScanti variants like AV Protection 2011 is the ability to modify an infected system's HOSTS file.
Our technical research team has taken a special notice to the FakeScanti family due to it receiving continuous exploit updates. These new updates to FakeScanti have allowed it to uncover various flaws in popular software, which may open up new fields of viable targets for orchestrated malware attacks.
The FakeScanti trojan itself was already classified as being associated with several fake anti-virus programs such as System Fix, Security Sphere 2012 and many others. These fake AV programs all embody virtually the same type of graphical interface and failed ability to detect or remove legitimate computer viruses and other malware.
What Does FakeScanti Do Now?
One of the most interesting findings of how FakeScanti and its associated malware is now acting, is its new capability of being able to modify an infected system's HOSTS file. The HOSTS file of a PC allows a system to connect hostsnames to IP addresses so when the user attempts to visit a site added to the HOSTS file such as Google or Facebook, they are redirected to another unrelated site. In the case of FakeScanti's recent evolution, the site that users are redirected to is based in Germany and serves up other variants of the same family of fake AV programs.
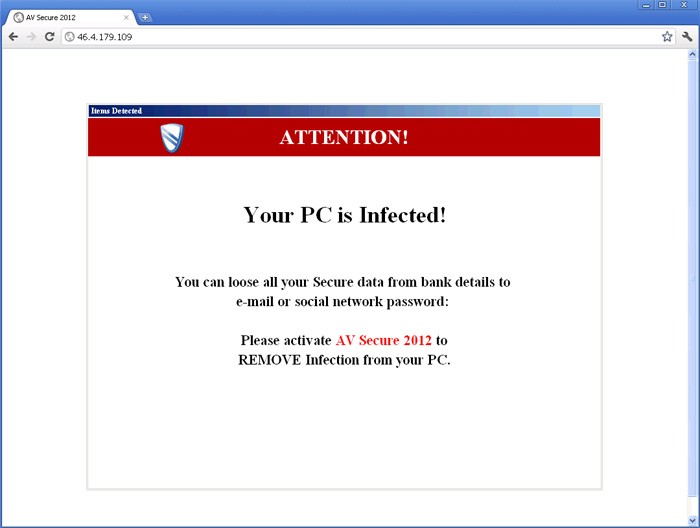
The image below (Figure 1.) represents one of the German-based sites that a system infected with a FakeScanti fake AV variant is susceptible to loading due to an edit of the HOSTS file. Notice how the site asks the user to 'please activate AV Secure 2012', which is more than likely asking you to purchase a variation of the rogue anti-virus program AV Security 2012 that we detected in early November 2011.
Figure 1. A live site redirection from a HOSTS file edited by a FakeScanti Trojan fake AV program variant
Why Do Hackers Edit HOSTS Files?
We see nothing new under the sun when it comes to the hijacking of a HOSTS file. This has been a long running technique among malicious hackers dating back several years. What is new is the fact that rogue anti-virus programs are now conducive to exhibiting this very behavior. We can now say with a certainty that new families of rogue AV programs contain the ability to edit HOSTS files which may lead further destruction through the download of additional malware.
In the past, editing a HOSTS file by malware was an easy way to lead computer users to phishing sites when they attempt to visit a legitimate page. The FakeScanti scam seems to be initiated through malicious links usually included in a spam email, a malicious link posted on a large social site such as Facebook or through search term poisoning using clever SEO (Search Engine Optimization) techniques.
What you can do to protect yourself is use caution when opening suspicious emails or clicking on links that are initially unrecognizable. It is also essential that you utilize an updated anti-virus or anti-spyware program in the event that you accidently download malware.