Zyka Ransomware
The Zyka Ransomware is a ransomware Trojan that enters a computer automatically and then takes the victim's files hostage. To do this, the Zyka Ransomware will encrypt the victim's files using an AES encryption algorithm. The Zyka Ransomware identifies the files it locks with the extension '.lock,' which is added to the end of each affected file's name. The Zyka Ransomware displays its ransom demand in a pop-up window on the infected computer.
Table of Contents
Instead of Infecting You, the Zyka Ransomware Infects Your Files
After encrypting the victim's files, the Zyka Ransomware displays a large pop-up window with instructions pertaining to the Zyka Ransomware attack. The instructions claim that the victim's files were encrypted using the AES encryption and that it is necessary to pay a ransom to recover the infected files. Unfortunately, it may be impossible to recover files infected by the Zyka Ransomware without the decryption key, which the con artists hold in their possession. Currently, victims are instructed to pay a ransom of $170 USD in Bitcoins. The Zyka Ransomware threatens to delete the victim's files completely if the Zyka Ransomware ransom is not paid before 72 hours. However, PC security researchers strongly advise computer users to avoid paying the Zyka Ransomware ransom. Even though it may not be possible to restore the files encrypted by the Zyka Ransomware currently, paying the Zyka Ransomware's ransom may result in hoaxes since the con artists may ignore the victim's payment or even ask for more money from the victim. More importantly, paying the Zyka Ransomware ransom allows the Zyka Ransomware's creators to continue creating threats and profit from victims.
What is the Purpose of Attacks Like the Zyka Ransomware
Nowadays, there are countless ransomware Trojans that are active in the wild. In the last year, encryption ransomware Trojans like the Zyka Ransomware have become common increasingly. The main purpose of the Zyka Ransomware is to encrypt victims' files and demand ransom payments. This is a tactic that it shares with countless other ransomware variants. These attacks are often nearly identical to one another, only differing in small presentation details and the type of encryption used in the attack. In most cases, attacks like the one executed by the Zyka Ransomware may be distributed through emails. Victims will receive spam email messages containing corrupted file attachments that download and install the Zyka Ransomware, often through the use of macro scripts contained in DOCX or PDF documents. This is, however, not the only way in which threats like the Zyka Ransomware can be distributed. The Zyka Ransomware also can be distributed through attack websites, fake file downloads on file-sharing networks and torrent networks, and by hacking into the victims' computers directly. Since the Zyka Ransomware attack can be so devastating to computer users that are unprotected, it is essential that computer users take steps to ensure that their computers are protected from infections like the Zyka Ransomware adequately.
The following is the full text of the Zyka Ransomware pop-up ransom note:
'You are the victim of the Zyka
Your important files encryption produced on this computer: photos, videos, documents etc. Here is a complete list of encrypted files, and you can personally verify this.
Encryption was produced using a unique public key AES that generated for this computer. To decrypt your files you need to obtain the private key.
The single copy of the private key, which will allow you to decrypt the files, located on a secret server on the Internet, the server will destroy the key after 72 hours.
After that nobody and never will be able to restore files.
To obtain the private key for this computer which will automatically decrypt files, you need to pay 170 USD /170 EUR to the bitcoin wallet below.
1GmGBH9ra2dqA8CgRg8a8Rngx4qHb2hLDW
If you do not have bitcoins you can buy them from localbitcoins.com
Thank you!/
Computer users are advised to backup all important files using the cloud or an external memory device. A reliable security program that is fully up-to-date also should be used to prevent the Zyka Ransomware from being installed and intercept the attack in case the Zyka Ransomware manages to enter the victim's computer.
SpyHunter Detects & Remove Zyka Ransomware
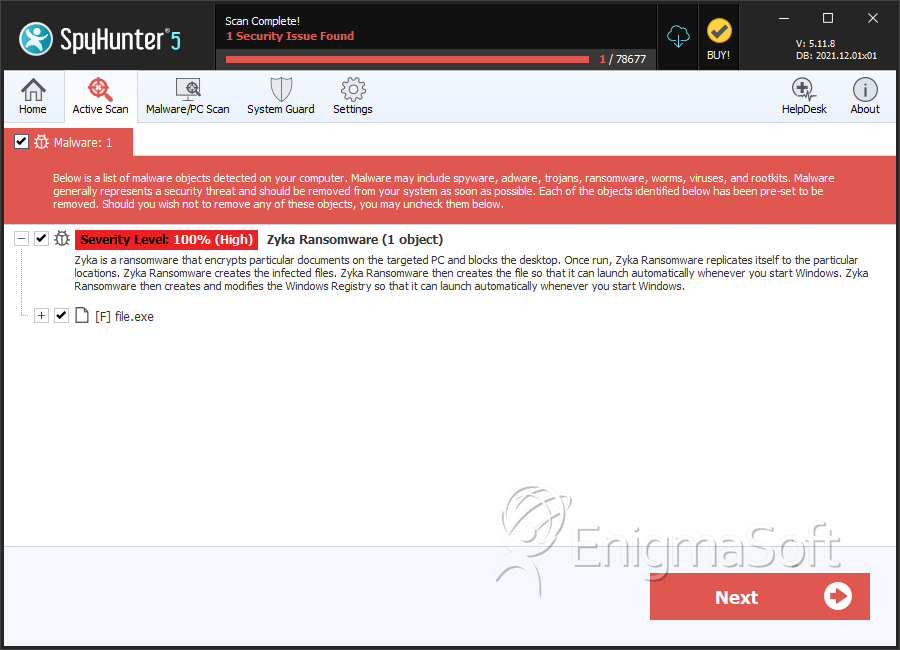
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 66d013f8ba679eecd743116d3299a855 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.