ZeroCrypt Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | November 2, 2016 |
| Last Seen: | January 10, 2019 |
| OS(es) Affected: | Windows |
The ZeroCrypt Ransomware is an encryption ransomware Trojan that identifies the encrypted files with the extension '.ZN2016'. Once the ZeroCrypt Ransomware encrypts a file, it is no longer accessible. The ZeroCrypt Ransomware demands that the victim pays a ransom in exchange for the decryption key that is necessary to recover the encrypted data. The ZeroCrypt Ransomware drops its ransom note in text files named 'the ZeroCrypt_RECOVER_INFO.txt,' which are copied into each directory where the ZeroCrypt Ransomware has encrypted the victim's files. PC security analysts strongly advise computer users to avoid paying the ZeroCrypt Ransomware ransom if their files become compromised.
Table of Contents
How the ZeroCrypt Ransomware may Spread
There are many ways in which the ZeroCrypt Ransomware may be spread. The most common two ways of distributing the ZeroCrypt Ransomware and similar threats is through the use of corrupted links and corrupted files. The most common way of tricking inexperienced computer users into downloading corrupted files or clicking on corrupted links is through the use of corrupted email messages. These spam email messages may contain misleading information designed to trick computer users into clicking an embedded link or downloading an attached file. When the file is opened or the link accessed, the ZeroCrypt Ransomware is downloaded and executed on the targeted computer. As soon as the ZeroCrypt Ransomware is downloaded, it will begin to carry out its attack.
The ZeroCrypt Ransomware Used a Strong Encryption Method
The ZeroCrypt Ransomware may inject corrupted scripts into Windows memory processes such as svchost.exe or explorer.exe to hide its activities in its background. The ZeroCrypt Ransomware makes modifications to the Windows Registry that allow it to run in the background and carry out its activities. Using a strong encryption algorithm, the ZeroCrypt Ransomware will begin encrypting the victim's files, generating a decryption key that also is encrypted and delivered to the ZeroCrypt Ransomware's Command and Control server. Every time the ZeroCrypt Ransomware encrypts a file, it changes its extension, making it obvious which files are no longer accessible. Essentially, the ZeroCrypt Ransomware takes the victim's computer hostage until the victim pays the ransom.
The ZeroCrypt Ransomware’s Ransom Note and Payment
The ZeroCrypt Ransomware demands its ransom by dropping text files on the victim's computer. The ZeroCrypt Ransomware's ransom note is quite rude, asking for the ridiculously high amount of 10 BitCoins (approximately $7200 USD at the current exchange rate!). Most ransomware Trojans demand a payment amount between 0.5 and 1.5 BitCoins, which is already high. Asking for 10 BitCoins, with the threat of raising the amount to 100 BitCoins is simply unrealistic.
Dealing with the ZeroCrypt Ransomware
PC security analysts strongly advise against paying the people responsible for the ZeroCrypt Ransomware. Apart from the fact that the ZeroCrypt Ransomware ransom amount is extremely high, paying the ZeroCrypt Ransomware ransom allows con artists to profit from threat attacks and continue to create additional threats. PC security researchers do not favor aiding these people in any way. The additional problem is that research has shown that the people responsible for threats like the ZeroCrypt Ransomware will frequently ignore their victims or demand even increasing ransoms from the victim, preying on their desperation to recover the files.
Preventing the ZeroCrypt Ransomware Attacks
Because of the nature of the ZeroCrypt Ransomware infection, the best measure is to take precautions to ensure that computers are protected from threats like the ZeroCrypt Ransomware adequately. PC security researchers recommend having effective file backup methods that involve unmapped drives or external memory devices not connected to the main computer directly (to minimize the risk of threats like the ZeroCrypt Ransomware encrypting a backup copy as well). If there are backups of all files, computer users can recover from an attack from threats like the ZeroCrypt Ransomware quickly by simply restoring the affected files from the backups after wiping the affected drive or using a reliable security program that is fully up-to-date to remove the ZeroCrypt Ransomware infection itself. Computer users should handle email attachments with caution, to prevent these threats from being installed.
SpyHunter Detects & Remove ZeroCrypt Ransomware
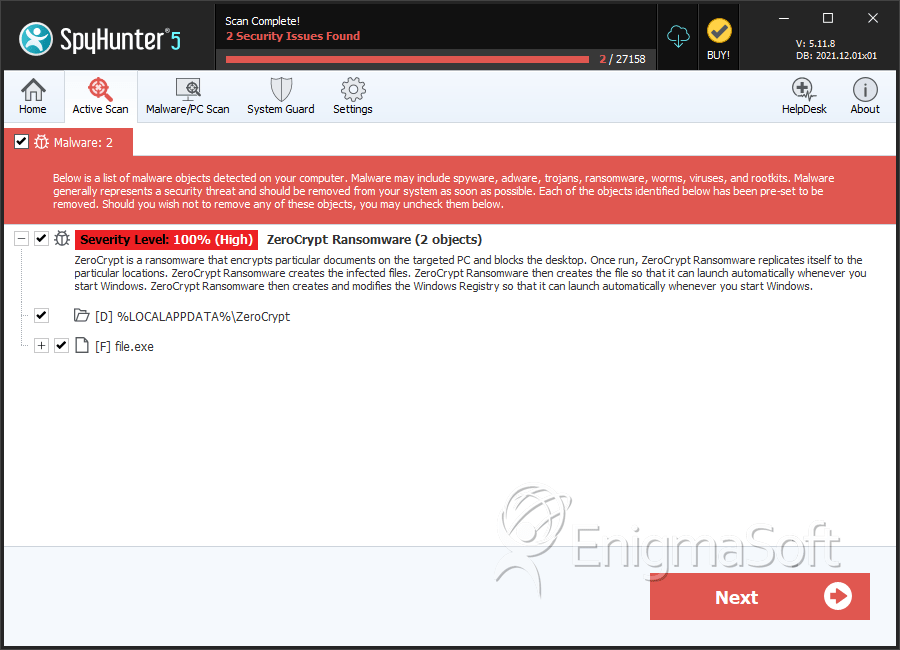
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | acc74bb26ce84cd41b5400ed45092b49 | 0 |
Directories
ZeroCrypt Ransomware may create the following directory or directories:
| %LOCALAPPDATA%\ZeroCrypt |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.