Win 7 Home Security 2011
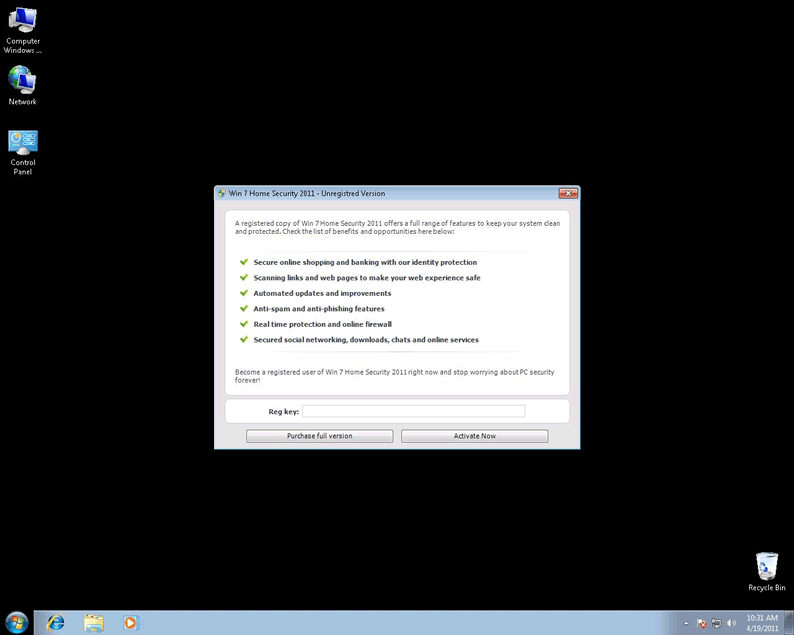
Win 7 Home Security 2011 Image
If Win 7 Home Security 2011 is on your computer, then your computer has malware. Although Win 7 Home Security 2011 uses the name of a Windows product and some bland-sounding generic words in order to make itself sound like a real security program, Win 7 Home Security 2011 is nothing but a fraud. Win 7 Home Security 2011 is incapable of doing anything beneficial or useful for you or for your PC security, because its whole purpose is to scare you into thinking that you have to pay for a nonexistent software license in order to remove imaginary threats.
Among malware, Win 7 Home Security 2011 is sort of a special case – along with the other members of its malware "family." Instead of being a clone of some earlier malware, or closely related to existing malware, Win 7 Home Security 2011 and its relatives are literally identical. Win 7 Home Security 2011 clones include
What looks like a family of more than thirty fake security applications is, in this case, just one malicious program that takes on a different name and skin depending on the computer that it infects. Generically, this malware is known as the Multi Rogue, or . The multi-rogue malware behind Win 7 Home Security 2011 names itself based on the version of Windows it finds on your computer, followed by a phrase taken at random from a list. Therefore, you will only find Win 7 Home Security 2011 on computers that are running Windows 7.
Table of Contents
Signs that Win 7 Home Security 2011 Has Infected Your PC
Because Win 7 Home Security 2011 is identical to the other malware in its family, Win 7 Home Security 2011 causes the same symptoms, which are:
- A fake Win 7 Home Security 2011 user interface shows up every time Windows starts, and the interface shows a scan progress animation to simulate a scan of your computer. The interface uses the Windows logo and may even mimic the appearance of the Windows 7 Action Center. Then, despite the fact that Win 7 Home Security 2011 can't detect threats, Win 7 Home Security 2011 will alert you that Win 7 Home Security 2011 has found numerous infections on your PC that you must remove urgently. When you try to remove these so-called "threats," Win 7 Home Security 2011 will tell you that the only way you can do that is if you purchase a "registered" or "licensed" copy of the Win 7 Home Security 2011 software.
- Win 7 Home Security 2011 runs constantly in the background, generating constant pop-up security alerts. These alerts have scary-sounding headlines and really off-the-wall content, and the things they warn you of are both extremely vague and completely untrue. The alerts have buttons and prompts to try to get you to go to the purchase site for Win 7 Home Security 2011.
- While Win 7 Home Security 2011 is on your computer, you will be unable to access other programs, except your web browser. Your web browser will be hijacked, so that the only website you can view will be a purchase page for Win 7 Home Security 2011.
- Win 7 Home Security 2011 disables the Control Panel, Task Manager, and Regedit. Win 7 Home Security 2011 may even run while Windows is in Safe Mode!
Some of Win 7 Home Security 2011's malicious capabilities come from a rootkit that almost always comes with the fake security program malware. The rootkit can make Win 7 Home Security 2011 very difficult to remove, but please remember that paying for Win 7 Home Security 2011 will not change the way the malware behaves. Win 7 Home Security 2011 can be removed, with the proper technical expertise or legitimate anti-virus software.
How an Infection with Win 7 Home Security 2011 Begins
Win 7 Home Security 2011 relies on a Trojan dropper in order to infect computers. The Trojan can be hidden in any seemingly ordinary file, which can be disguised as a fake security program update, attached to a spam email, or pushed to your PC as a drive-by-download from a malicious website. Once the Trojan has downloaded to your computer, it drops the files for Win 7 Home Security 2011 and sets up the malware. This process may even mimic the appearance of a Windows update process, so that you will not be suspicious about what is going on with your computer.
The multi-rogue that sometimes manifests itself as Win 7 Home Security 2011 has been around since early 2010, but in 2011, there has been an increase in the infection rate. Fake security software scams like that of Win 7 Home Security 2011 are hugely profitable for the people who design and run them, and so these scams are everywhere online. It's always easier to prevent Win 7 Home Security 2011 from infecting your computer than to try to remove Win 7 Home Security 2011 later.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\Local\[RANDOM CHARACTERS].exe (look for 3-letter names) | |
| 2. | %AppData%\Roaming\Microsoft\Windows\Templates\t3e0ilfioi3684m2nt3ps2b6lru | |
| 3. | %AllUsersProfile%\t3e0ilfioi3684m2nt3ps2b6lru | |
| 4. | %Temp%\t3e0ilfioi3684m2nt3ps2b6lru | |
| 5. | %AppData%\Local\t3e0ilfioi3684m2nt3ps2b6lru |

