Win32/Criakl.C
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 42 |
| First Seen: | January 5, 2015 |
| Last Seen: | June 9, 2023 |
| OS(es) Affected: | Windows |
Win32/Criakl.C Image
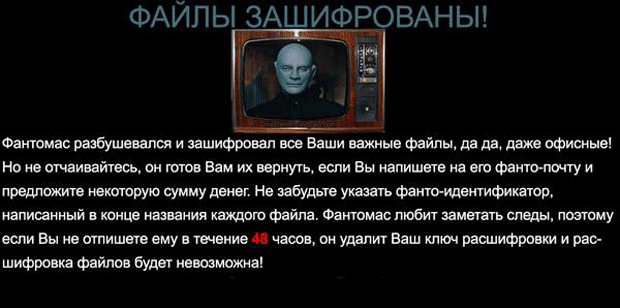
Win32/Criakl.C is a very dangerous Trojan, which performs ransomware attacks. This threat also goes by the names TR/Dropper.Gen, Trojan.Win32.Ransom, Trojan-Ransom.Win32.Cryakl and RDN/Ransom!eg. Win32/Criakl.C is a severe threat to the system because Win32/Criakl.C makes the user's computer completely unusable by encrypting the files on the hard drive. Thus, the person is deprived of any access to them. In order to remove the encryption, the cyber crooks demand money and give a short period for the transaction to happen. In fact, this is a scheme for getting money - you are required to pay a ransom so that you can use your PC again. If you have fallen victim to Win32/Criakl.C, you should not consider paying anything to the crooks. If you do, not only will you put at stake your entire bankroll, but you will also finance their illicit activities. Win32/Criakl.C is very resilient, and only experts may be able to remove Win32/Criakl.C manually. If you are not such, the most sensible thing will be to use a powerful anti-malware program, which will delete this threat for you.
Table of Contents
How can You Get Infected with Win32/Criakl.C?
Win32/Criakl.C was detected at the end of 2014 and computer security experts are still investigating the distribution methods and all features of this ransomware. What is certain is that the Trojan relies on many deceptive methods so that it can infiltrate your computer system unnoticed and deliver its harmful payload. Specialists report that sometimes the threat disguises itself as a legitimate application in order to evoke trust and mislead the unsuspecting user into downloading it. For example, Win32/Criakl.C has used an executable file with the name winrar.exe.
Other popular methods for the dispersion of this Trojan include e-mail spam with fake data such as financial information, taxes or debts due to be paid. The cyber crooks are very creative and usually use such information that would worry or scare innocent users, and they may act before assessing the legitimacy of the e-mail sender. The threat itself is contained in the attachments, and if they are downloaded, this will serve as permission for the installation of the ransomware.
Often, threats such as Win32/Criakl.C may be found in suspicious content like torrent files or cracked versions of paid programs or games. This is why you should avoid downloading anything from unreliable sources and preferably use the product's original Web page. Corrupt links over the Internet may transfer you to pages that perform fake on-line scans and claim that your PC is infected, and you need to download a certain security program. In reality, your computer most likely is completely secure, and this is just a trap so that you download the threat.
What Happens after Win32/Criakl.C Has Been Loaded in Your System?
Win32/Criakl.C performs a series of actions in order to achieve the goal Win32/Criakl.C was designed for. First, Win32/Criakl.C will add itself to the list of programs, which are automatically started when your Windows boots. The ransomware quickly creates new files that spread all over the system. These files include "d.bat", "desktop.bmp" and a file with the identification number of the Trojan. After the initial adjustments are done, Win32/Criakl.C will encrypt your important personal files - pictures, text documents and media files. They will be locked so that you cannot open any of them. A lot of your programs may also have their functionality disrupted. A threatening message, written in Russian, will appear on the desktop. It will state that you have only 48 hours to pay a ransom or else you will lose these files forever. The intention is to scare the users and makethem quickly pay, however this would be a mistake. Nothing guarantees that if you do what the crookers require, you will have your access back. One of the things that may give you a clue that this is all a tactic is the payment methods required. They are specially chosen to make it impossible to trace the receiver of the money.
How to Eradicate Win32/Criakl.C for Good without Paying Anything to the Criminals?
If your system is contaminated, the authors of Win32/Criakl.C may load additional harmful content. In order to remove the infiltration and save your files, you must take immediate actions. However, removing Win32/Criakl.C on your own may be impossible for a green hand in computers. Simple actions as system restore will have no effect as the ransomware's files are rooted deep into the OS. The conventional security programs cannot help either because the threat is specially designed to sidestep them. What you need is a dependable anti-malware application with good history of removing such threats. Although Win32/Criakl.C is very sophisticated, Win32/Criakl.C will be eradicated in no time by the anti-malware program and such events will be prevented in the future. Experts advise always to have a copy of your important data on a secure source as a USB drive, external hard disk or cloud for additional security.
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | p1os9e6mvu.exe | 572f82d2b1ffeb26681328e7c78a9528 | |
| 2. |
C:\Users\ |

