Vista Anti-Virus 2011
Vista Anti-Virus 2011 Image
Vista Anti-Virus 2011 is not a pre-installed program for Windows Vista, and Vista Anti-Virus 2011 is not anti-virus software. Vista Anti-Virus 2011 is a scam, which preys on unsuspecting PC users by trying to scare them into paying for a nonexistent software license. Vista Anti-Virus 2011 is incapable of doing any of the things that Vista Anti-Virus 2011 claims to be able to do, and contrary to what the con-artists behind this fake security program want you to think, Vista Anti-Virus 2011 is not affiliated with Microsoft. If Vista Anti-Virus 2011 has infected your computer, you do not have to pay for the malware – and should not pay for Vista Anti-Virus 2011 – for any reason.
Vista Anti-Virus 2011 is just one of the names taken by a single malicious program. This malware chooses a name and a 'skin' based on which version of Windows it finds on your computer. So, Vista Anti-Virus 2011 only occurs on PCs running Windows Vista. The second part of the name, "Anti-Virus 2011" is one of at least eleven different endings that the malware can choose to use, and it is taken at random from a list. If you use Windows XP or Windows 7, this fake anti-virus application will choose a name for itself that begins with "XP" or "Win 7," (along with a randomly-selected ending) and it will use an interface that looks right for that operating system. The universal name for the malware behind Vista Anti-Virus 2011 and all of these other phony security applications is , or the 'multi-rogue.' It's one infection with at least thirty-three faces.
Table of Contents
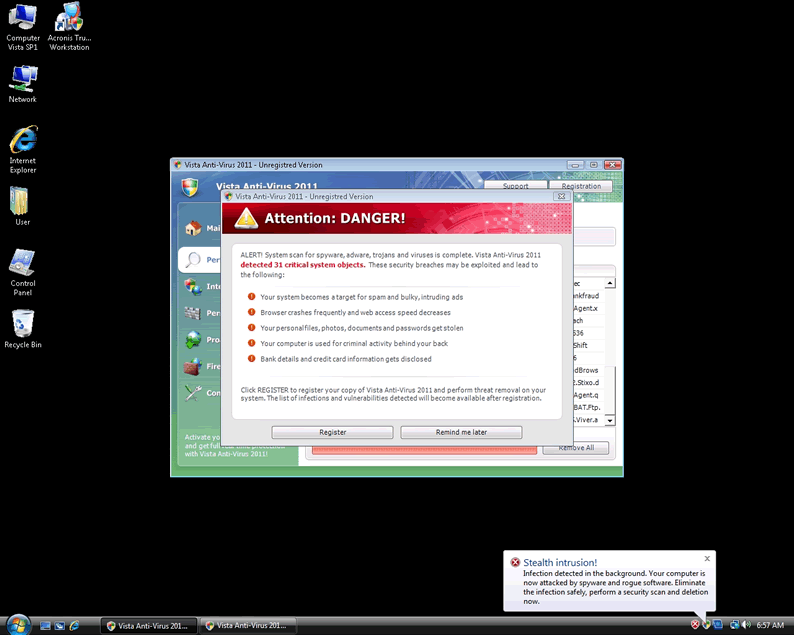
What Does Vista Anti-Virus 2011 Look Like?
Vista Anti-Virus 2011 has changed slightly over time, as the malware behind Vista Anti-Virus 2011 has evolved, but practically everything about it has remained the same, including its symptoms. Some of the signs of infection with Vista Anti-Virus 2011 are:
- An interface that says Vista Anti-Virus 2011, and which uses a modified Windows Security Center logo and Vista-type styling, appears every time Windows starts. This interface plays a scan progress animation, pretending to do a scan, and then it returns a long, bogus list of results. Vista Anti-Virus 2011 will then tell you that in order to remove all of these "threats," you have to purchase a license for Vista Anti-Virus 2011.
- While Windows runs, security alerts very frequently appear, usually making vague claims about your PC security. These alerts are pre-written and pre-programmed, so they are the same every time, across all infected computers. The headers include "System hijack," "System danger," "Privacy threat," "Stealth intrusion," and "Vista Anti-Virus 2011 Firewall Alert." The prompts in these alerts will lead you to the same payment site linked to by the fake virus scanner.
- When you try to run any program other than your web browser, either Vista Anti-Virus 2011 opens instead, or you see an error message from Vista Anti-Virus 2011 instead. This includes Regedit and Task Manager, making Vista Anti-Virus 2011 even more difficult to remove. Only Vista Anti-Virus 2011 and your installed browsers will open.
- Your web browser will be hijacked, and you will not be able to view websites normally. When you try to navigate to a page, you will either be redirected or see a phony alert window in your browser that claims that the page in question is malicious. You will be unable to access any website that offers computer or malware help, and you will constantly find yourself redirected to a payment site for Vista Anti-Virus 2011.
How Does Vista Anti-Virus 2011 Spread?
Vista Anti-Virus 2011 can infect a computer in a few different ways. Infection via Trojan is the most common mode of infection, with the Trojan that drops the files for Vista Anti-Virus 2011 hidden in a fake video codec or bundled with a free file download. Vista Anti-Virus 2011 is also known to infect PCs through drive-by downloads, when you view a malicious website, and just by viewing it, you allow the site to download malware to your system. Furthermore, there are reports of these drive-by downloads of Vista Anti-Virus 2011 being supported by what is known as blackhat Search Engine Optimization, which is when online search results are tampered with or exploited in order to cause one of the results links to point to something other than what it is supposed to. (For example, you might search for salad recipes, and click on a link that was supposed to be a recipe for a Caesar salad, but wind up on a malicious ad page instead.) No matter how Vista Anti-Virus 2011 finds a way in, when Vista Anti-Virus 2011 is installing itself, it may try to pass itself off as a Windows update, through its appearance and alerts.
The malware that is Vista Anti-Virus 2011 (and so many other fake security programs) is not new; reports of problems with this malware go back to at least Spring 2010. However, with time, the malware has changed the way that it names itself on the affected PC, and at present, the main executable file for Vista Anti-Virus 2011 is named at random on each computer it infects, using a string of three letters. Vista Anti-Virus 2011 may even try to make itself appear to be a product from the gaming company Valve. Also, Vista Anti-Virus 2011 will make a large number of changes to the Registry, to disable normal Windows security functions and to give itself control over the system. In order to do much of what it does, Vista Anti-Virus 2011 requires a rootkit, and so Vista Anti-Virus 2011 often comes bundled with a rootkit. No matter what variation on Vista Anti-Virus 2011 you may find on your PC, it is a fraud. Vista Anti-Virus 2011 is part of a huge Internet-based scam, which has been traced back to Russia.
Some examples of Vista Anti-Virus 2011 family member are
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %AppData%\hee.exe |

