VindowsLocker Ransomware
The VindowsLocker Ransomware is an encryption ransomware Trojan that is used to carry attacks on computer users. The VindowsLocker Ransomware tactic consists in extorting victims by encrypting their files. The VindowsLocker Ransomware demands the payment of a ransom to return access to the affected files. The VindowsLocker Ransomware is one of the many variants of the Hidden Tear family of ransomware Trojans.
Table of Contents
The VindowsLocker Ransomware is a Hiden Tear-Based Threat
The VindowsLocker Ransomware receives its name because it identified the files that have been encrypted through the use of the extension '.vindows.' The VindowsLocker Ransomware is based on Hidden Tear, an open source ransomware engine that was released to the public as an 'educational ransomware engine.' Unfortunately, con artists took advantage of this freely available ransomware engine quickly to carry out attacks around the world. There are countless variants of this ransomware Trojan family, with the VindowsLocker Ransomware being one of the latest at the time of writing. One of the dangers of the public release of this code is that it allowed anyone to create ransomware variants virtually, putting this weapon in the hands of people that would otherwise not have had the technical ability or resources to deploy it. One reason to suggest that the people responsible for the VindowsLocker Ransomware are not particularly savvy is that the VindowsLocker Ransomware is being packed in an executable file named vindows.exe, which does not have a digital certificate, triggering the User Account Protocol (UAC) warning on the victim's computer.
How the VindowsLocker Ransomware may be Used to Attack Computer Users
The VindowsLocker Ransomware uses a custom AES-256 encryption algorithm in its attack. The VindowsLocker Ransomware will use this encryption algorithm to encrypt a wide variety of files on the victim's computer, targeting text documents, spreadsheets, PDF files, eBooks, databases, presentations, video files, audio, images, and other commonly used file extensions. The VindowsLocker Ransomware will look for files in the default user library on the victim's computer, in the following paths:
%UserProfile%\Desktop
%UserProfile%\Downloads
%UserProfile%\Documents
%UserProfile%\Pictures
%UserProfile%\Music
%UserProfile%\Videos
The VindowsLocker Ransomware will then encrypt the files it finds using its strong encryption algorithm. Once a file has been encrypted by the VindowsLocker Ransomware it cannot be opened without the decryption key (which the con artists will hold until a ransom is paid). The files that have been encrypted by the VindowsLocker Ransomware can be identified easily because of the extension '.vindows,' which is added to the end of the file name. The VindowsLocker Ransomware's ransom note includes a stock photo of a technical support professional and a message written in very poor English. The VindowsLocker Ransomware's ransom note is delivered in the form of an HTA application that displays a pop-up message. This HTA file is dropped on the victim's desktop. When the victims open the file, it displays the following message:
'this not microsoft vindows support
we have locked your files with the zeus wirus
do one thing and call level 5 microsoft support technician at 1-844-609-3192
you will files back for a one time charge of $349.99'
PC security researchers strongly advise computer users against calling this phone number of paying the ransom. There is absolutely no connection between the VindowsLocker Ransomware, this message or Microsoft. While many of these attacks use ransom notes written in poorly written English, this one is especially egregious. The VindowsLocker Ransomware is not associated in any way with the infamous Zeus, a known banking Trojan.
Dealing with the VindowsLocker Ransomware
Despite its amateurish ransom note and poor implementation, the VindowsLocker Ransomware's encryption engine is still effective. This is why the best method for dealing with the VindowsLocker Ransomware is prevention. Computer users should take steps to backup their files to become protected against attacks like the VindowsLocker Ransomware.
SpyHunter Detects & Remove VindowsLocker Ransomware
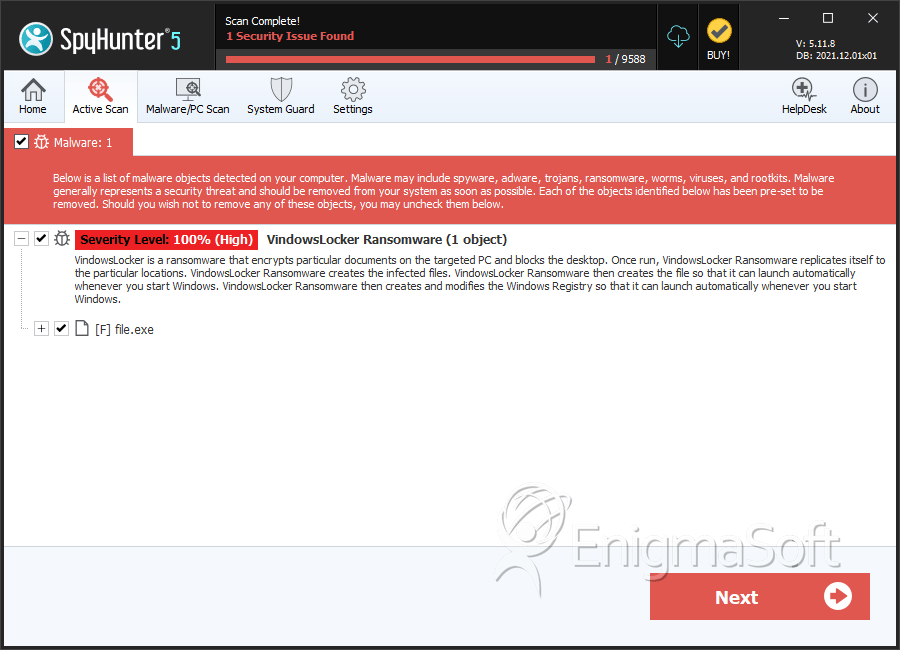
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 682f91e3ce769a6865ecd9f2b236e83a | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.