VanToMRAT
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 14,621 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 58 |
| First Seen: | October 26, 2016 |
| Last Seen: | July 24, 2023 |
| OS(es) Affected: | Windows |
VanToMRAT is a threatening tool used to manage infected machines remotely. The VanToMRAT software is a Remote Access Tool (RAT) that is promoted to potential buyers at Rekings.com, which is a market for Trojans, keyloggers and RATs on the Internet. Customers at Rekings.com can download VanToMRAT for free, and if they like what it offers, they can receive updates and improvements by purchasing a license. The author of VanToMRAT aimed the software at botnet operators that need a reliable central hub and hackers that could use remote PCs as proxies for their operations. VanToMRAT is said to be stable and stealthy—two qualities that are imperative to threat actors looking to cause trouble on the Internet without being detected.
Security experts note that VanToMRAT packs more than simple file extraction, connection rerouting, and information gathering capabilities. VanToMRAT is an advanced remote access Trojan that can be deployed to users via spam emails loaded with a macro-enabled document and JavaScript-enabled ZIP archives. It is possible to install VanToMRAT to targeted computers by using Trojan Droppers like Poshkod and Fedripto as well. Compromised computers can be managed by a server hub installed on the attacker's PC.
The VanToMRAT server hosts are programmed to send metrics like IP address, Windows version, the country of origin, a screenshot of the desktop and a list of running programs to the server hub, as long as the PC is running. The VanToMRAT program might be listed in the Windows task manager as a service and execute control code without the user's notice. Analysts note that VanToMRAT can access video and audio feed from the camera and microphone connected to the infected machine and send the multimedia feed to a third- party. The manager of VanToMRAT can access the file system of infected computers and perform file operations like editing existing data, delete and move objects. More advanced features of VanToMRAT include:
- Copy content from the clipboard
- Detect geographical location of the device by using Google Maps
- Download and run executable
- Edit keys in the Registry
- Enter commands via CMD
- Log keystrokes
- Perform DDoS attacks
- Run scripts
- Collect passwords from the browser
The maker of VanToMRAT included a specialized toolset titled 'Fun' that allows the operator to do annoying tricks with the infected PC. A remote manager can use VanToMRAT to:
- Logoff the user forcibly
- Open/Close CD-ROM
- Restart and shutdown the PC remotely
- Reverse the mouse movement
- Show/hide the clock
- Show/hide the taskbar icons and the taskbar itself
- Turn on/off the monitor
Experts alert that VanToMRAT can be used to execute DDoS attacks on servers and perform illicit actions. Removing the VanToMRAT software should be a priority for infected users. VanToMRAT might use a rootkit to hide its files and users are not likely to recognize suspicious program without proper education. You should consider using a credible anti-malware suite to terminate connections used by VanToMRAT and the threat running on the machine.
Table of Contents
SpyHunter Detects & Remove VanToMRAT
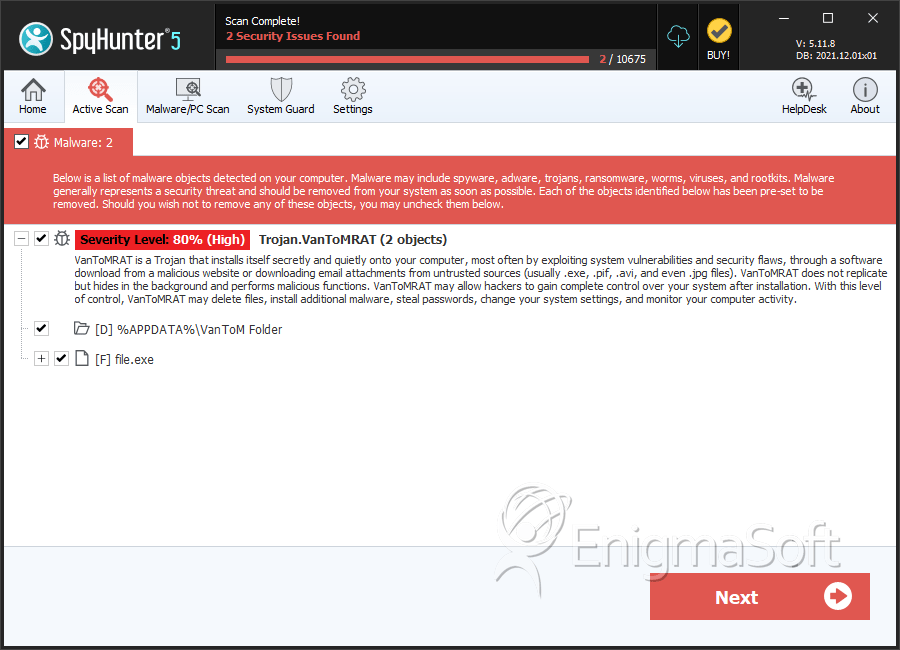
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 6f445df41fda54eac339a9fa3c38f211 | 0 |
Directories
VanToMRAT may create the following directory or directories:
| %APPDATA%\VanToM Folder |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.