Trojan:Win32/Loktrom.B
Trojan:Win32/Loktrom.B is a ransomware Trojan that attacks computers in various countries. Trojan:Win32/Loktrom.B blocks the victimized PC and covers the screen with a false full-screen notification by hiding all other windows, and makes your PC unusable. The misleading message allegedly comes from a legal authority which declares to be related to Windows and Microsoft Security Essentials. The bogus warning message of ransomware claims that illegitimate activity has been detected on your PC, which means that you have violated certain laws. The frightening warning message distributed by Trojan:Win32/Loktrom.B asks a victim to pay a fine to unlock the PC and avoid imprisonment. Trojan:Win32/Loktrom.B may make repeated modifications to the corrupted machine that make it hard for the computer owner to download, install, run, or update anti-virus applications. Trojan:Win32/Loktrom.B may be installed on the targeted computer by other security threats, or it may access the workstation via a drive-by downloads. When run, Trojan:Win32/Loktrom.B modifies the Windows Registry to make sure its copy launches whenever you boot up Windows. Trojan:Win32/Loktrom.B can also set the value as a random string in the registry entry.
Table of Contents
SpyHunter Detects & Remove Trojan:Win32/Loktrom.B
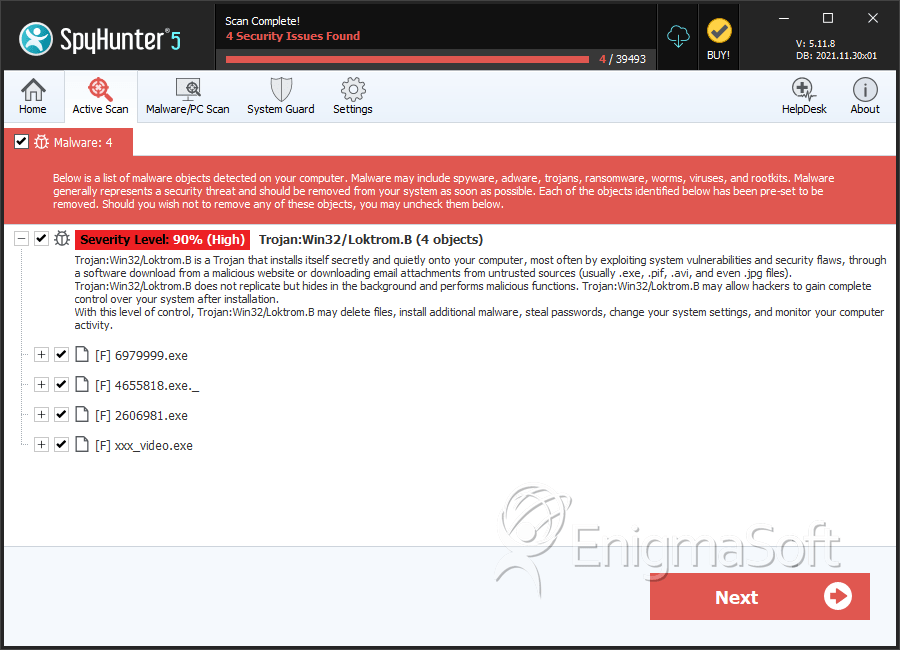
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 6979999.exe | 87ff01ce77ab71cc4953c6cbca3ef96b | 0 |
| 2. | 4655818.exe._ | 930935904e8d2914953b0e3b63be2656 | 0 |
| 3. | 2606981.exe | d09c386f3bb13aacf185afbbc87f5802 | 0 |
| 4. | xxx_video.exe | 7469d2bce990dc340841698795a6174b | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.