Trojan:Win32/Grymegat.B
Trojan:Win32/Grymegat.B is a Trojan that is not able to circulate by itself. Trojan:Win32/Grymegat.B may fulfill a number of actions selected by a cybercriminal on a targeted PC. When installed on the vulnerable computer system, Trojan:Win32/Grymegat.B makes system changes by downloading malevolent files and modifying the Windows Registry. Trojan:Win32/Grymegat.B makes modifications to the registry entries so that its copy can be initiated automatically whenever Windows is started. Trojan:Win32/Grymegat.B makes modifications to system security settings by disabling the LUA (Least Privileged User Account), otherwise known as the 'administrator in Admin Approval Mode' user type, by changing registry entries. Disabling the LUA permits all programs to start by default with all administrative privileges, without the computer user being encourages for explicit permission. Trojan:Win32/Grymegat.B contacts a remote host to notify about a new infection to its creator, to download and run arbitrary files (incorporating updates or other malware infections), to get configuration or other information, to receive commands from remote cybercrimianls and to upload data received from the affected PC.
Table of Contents
SpyHunter Detects & Remove Trojan:Win32/Grymegat.B
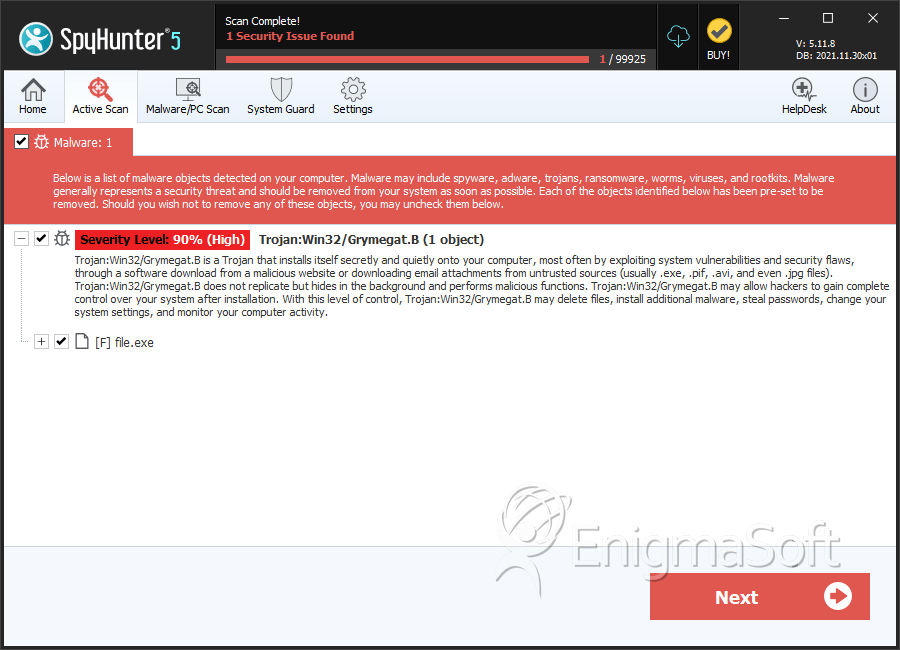
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. |
C:\Documents and Settings\ |
||
| 2. |
C:\Documents and Settings\ |
||
| 3. |
C:\Documents and Settings\ |
||
| 4. | file.exe | 03b4bbd4b7e6f0403dc6d215d6bdc6b7 | 0 |
| 5. | file.exe | 58098e72ad3fa4372115cbc15dbcd1ba | 0 |
| 6. | file.exe | 0d971da1fd0295eae02638bc5278b94d | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.