Trojan.Katusha
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 19,610 |
| Threat Level: | 90 % (High) |
| Infected Computers: | 3,620 |
| First Seen: | July 24, 2009 |
| Last Seen: | October 21, 2025 |
| OS(es) Affected: | Windows |
The Trojan.Katusha Trojan is a malware infection that is typically spread through external memory devices. Trojan.Katusha is designed to steal confidential information and to relay it to a remote server. While Trojan.Katusha is a threat to your privacy, Trojan.Katusha is not particularly difficult to remove. Furthermore, ESG security researchers have identified a Windows update that may result in a false positive detection of Trojan.Katusha. First discovered in spring of 2010, Trojan.Katusha is still relatively isolated and has not infected many computers around the world. This malware threat is designed to infect 32 bit Windows platforms and, like most Trojans, does not have the capacity to spread on its own. Rather, Trojan.Katusha is usually disguised as a benign or useful application which the user himself downloads and installs onto his computer. Although Trojan.Katusha may be linked to a rootkit infection, Trojan.Katusha itself does not have the capacity to reinstall itself automatically once Trojan.Katusha has been removed with a reliable anti-virus application. Trojan.Katusha has also been linked with various fake security programs and anti-viruses, with clones which include the detection string "FakeAV."
Table of Contents
Effects of Trojan.Katusha and How to Protect Your PC
As was mentioned before Trojan.Katusha enters a computer system with the help of another application or through social engineering, that is, taking advantage of human nature in order to deceive its victims. Once installed, Trojan.Katusha will copy itself onto various system folders and in the program files folder on your windows system. It will then connect to a remote server and download various files onto the victim's temporary files folder. Trojan.Katusha makes changes to the Windows Registry to execute automatically whenever the infected computer is booted. These changes allow Trojan.Katusha to connect to a remote server and transmit any information Trojan.Katusha may have gathered on its victim's computer system. In some versions of Windows, it may be possible to use System Restore to go back to a point before the infection. ESG security researchers also recommend disabling automatic back-ups until you eliminate Trojan.Katusha, since you may inadvertently copy Trojan.Katusha along with your data. To prevent Trojan.Katusha from starting up automatically, ESG security researchers recommend starting up Windows in Safe Mode by simply pressing the F8 key during start up.
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| Symantec | Trojan.FakeAV!gen29 |
| Sunbelt | VirTool.Win32.Obfuscator.hg!b (v) |
| Sophos | Mal/FakeAV-CX |
| Panda | W32/Autoit.KT |
| NOD32 | a variant of Win32/Kryptik.EWP |
| Microsoft | TrojanDownloader:Win32/Renos.LX |
| McAfee | Downloader-CEW.b |
| eTrust-Vet | Win32/FakeCodec.C!generic |
| AVG | Downloader.Generic9.CBGS |
| Authentium | W32/FakeAlert.GZ.gen!Eldorado |
| AhnLab-V3 | Win-Trojan/Agent.176128.IO |
| Panda | Suspicious file |
| Ikarus | Virus.Packed.Win32.Katusha |
| F-Secure | Suspicious:W32/Malware!Gemini |
| Sophos | Mal/FakeAV-DH |
SpyHunter Detects & Remove Trojan.Katusha
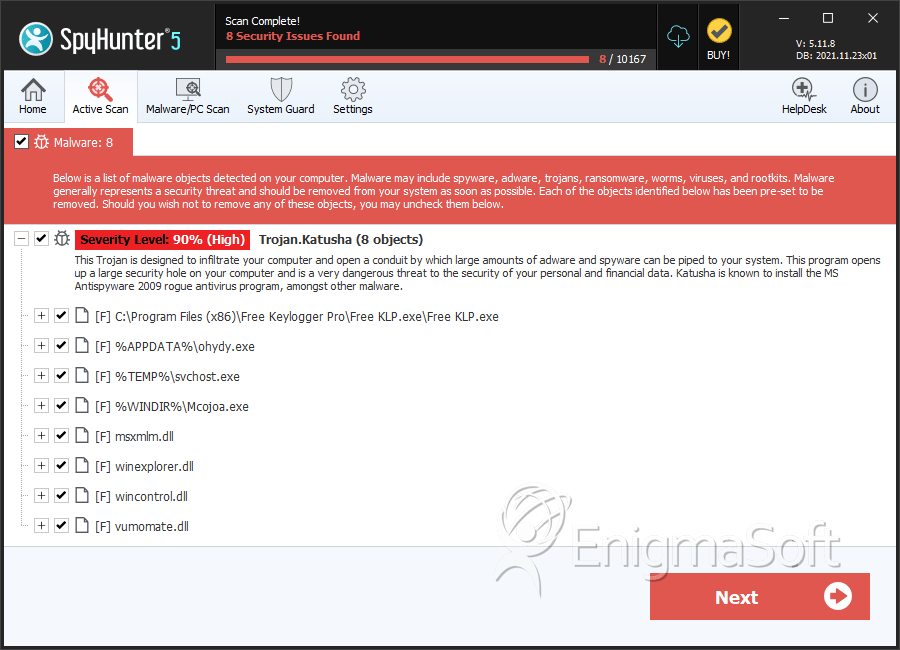
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Free KLP.exe | d3df5712baf1dea02bf952b59b042564 | 3,230 |
| 2. | ohydy.exe | d4345f2d7b03cc07a19c5969155e7d70 | 269 |
| 3. | Mcojoa.exe | 5244a690c6ba42c2b095fbf1b9395466 | 6 |
| 4. | svchost.exe | 4b5f7ab329dc82eef7a16a08d9a02852 | 3 |
| 5. | msxmlm.dll | 2f1fc0cb4cacdf8730214150714254cf | 0 |
| 6. | vumomate.dll | cdb8888c985ea027d410edd309545097 | 0 |
| 7. | wincontrol.dll | 367abd10b7dd3c6deba207cb0fcd9011 | 0 |
| 8. | winexplorer.dll | 665c5d99f075d458d5c42e812cff0c72 | 0 |
| 9. | win32extension.dll | 1b9f0d1fa4204cfee051f5ff30b47de2 | 0 |
| 10. | system.exe | aeae34fe29a9b15c0d3eaba7b3521e4a | 0 |
| 11. | notepad.dll | 45cddba5ef413e10576745fa4b1faf49 | 0 |
| 12. | 79F.tmp | 4ba1a1b00e5b4f48509629edf04e6cce | 0 |
| 13. | dwtrig20microsoft.exe | 3dc5d5c9498558f98d3ba036fc637836 | 0 |
