Trojan.Coinminer
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 1,746 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 126,850 |
| First Seen: | February 16, 2018 |
| Last Seen: | December 24, 2025 |
| OS(es) Affected: | Windows |
Table of Contents
SpyHunter Detects & Remove Trojan.Coinminer
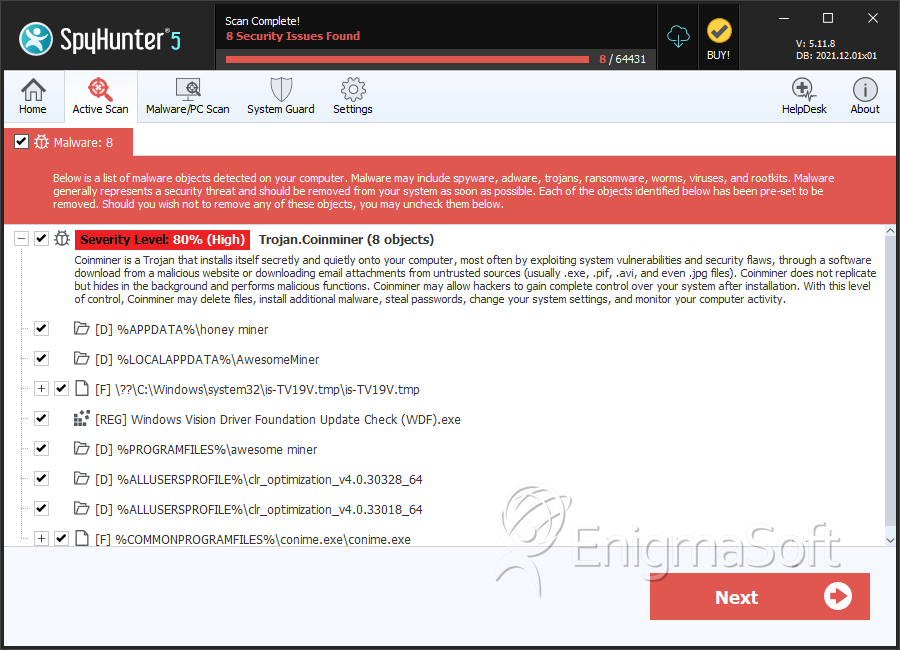
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | is-TV19V.tmp | 1bf48abe5f3f1f61a4bf7ebd5adaa75b | 1,793 |
| 2. | conime.exe | c50bb65871b46075aeb0d035671ffbbf | 880 |
| 3. | juched.exe | 443cfef1b32029f6461c6f1078930714 | 365 |
| 4. | kbdusa.exe | 71bde539d6d95347337ccd34ac60f335 | 172 |
| 5. | dplayx.exe | c4edddcafdded4042549ebeedc87281d | 63 |
| 6. | rpcnsh.exe | 54eb5b4813124a80eadc49c0e1f6e874 | 62 |
| 7. | msvc.exe | 0447d246d87a2498f24d9b1910099aa8 | 61 |
| 8. | conhost.exe | 7b994eaf4457a89935deb269d5c25a94 | 45 |
| 9. | winlogui.exe | 034faf2273577d9f9bbbbf5fe568fd51 | 16 |
| 10. | FIHF.exe | f9e52bad1d1c89ceb5fcf89a9b6dc38e | 10 |
| 11. | ctfmon.exe | 6e9dfc6d15a5c3bee4a08db1b441aba7 | 6 |
| 12. | appextb.exe | 010f027e58ba31a56035a4efd1338839 | 6 |
| 13. | d3dcompiler_41.exe | 4651788d85634163b50c28e65ed7a3cd | 6 |
| 14. | igfxpers.exe | ea5e45ae2b6ca1d396105cec2649c1b3 | 5 |
Registry Details
Directories
Trojan.Coinminer may create the following directory or directories:
| %ALLUSERSPROFILE%\Application Data\adwxcssgvy |
| %ALLUSERSPROFILE%\Application Data\clr_optimization_v4.0.30328_64 |
| %ALLUSERSPROFILE%\Application Data\clr_optimization_v4.0.33018_64 |
| %ALLUSERSPROFILE%\Logss |
| %ALLUSERSPROFILE%\SteganosNotifierServiceWenter |
| %ALLUSERSPROFILE%\adwxcssgvy |
| %ALLUSERSPROFILE%\clr_optimization_v4.0.30328_64 |
| %ALLUSERSPROFILE%\clr_optimization_v4.0.33018_64 |
| %APPDATA%\ExplorerInternets |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\7ZipArchiver |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\IntelCorporalion |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\Macro |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\Microsoft |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\Orion |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\SmartServiceScreenWenter |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\WmiPrvSE |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\adobe |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\adobee |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\gtopapkamaixz |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\kingusuanlaola |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\kingusunlaola |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\kingusunlola |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\minecrofnm |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\minepapkamxsz |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\netrosh |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\randpapkamainof |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\randwpapkamain |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\rneadwpapkamain |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\rneadwpapkaxzai |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\rqnadpapkamain |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\rqnadpapkamaixz |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\stegnmxsdbe |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\steuagnagtmsndbe |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\steuagntmsndbe |
| %APPDATA%\Microsoft\SystemCertificates\My\CTLs\stolpapkaxzmasi |
| %APPDATA%\honey miner |
| %HOMEDRIVE%\$RECYCLE.BIN.EXE |
| %HOMEDRIVE%\$RECYCLE.EXE.JPG |
| %HOMEDRIVE%\kernels |
| %LOCALAPPDATA%\AwesomeMiner |
| %LOCALAPPDATA%\svc10.17134 |
| %PROGRAMFILES%\awesome miner |
| %PROGRAMFILES(x86)%\awesome miner |
| %TEMP%\tratata |
| %appdata%\Idle |
Analysis Report
General information
| Family Name: | Trojan.Coinminer |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
8b349747ef5215e4b15abe50859d2416
SHA1:
bebbee4f1512c8daefc01e8dd91dbc19d3ffb4ea
File Size:
4.20 MB, 4196864 bytes
|
|
MD5:
3ef27ad24031fa1bcb514da582829026
SHA1:
b3f3c86d39e32e9b1e368092b61cf7eac6604d55
SHA256:
26F0613EEF3294F117E2F2DB0B9A82B7294126C282208999FFBBB7F8E195E187
File Size:
9.25 MB, 9252864 bytes
|
|
MD5:
33412ba25cc086bf566237a378c6e6e3
SHA1:
e4d3f661063801bb9191f45b782fee8ab50955dc
SHA256:
E4CA4556CAFB7BE3C705F5586ECFC99E1467667A738FD59D156E6EB8D1574713
File Size:
8.05 MB, 8052736 bytes
|
|
MD5:
74539ed33537e79efd3e5ae3bc5468ff
SHA1:
0b0b234c191d9f63d6fd19b7db15aef61df5fa4a
SHA256:
8AC67F4C28DB5E0A4FD11AD7612D13B3439FF3D63FD895DFED7EF443752A0421
File Size:
9.31 MB, 9309696 bytes
|
|
MD5:
9dbe8109b2ee6e24e00100707b8b34d4
SHA1:
0890344d85cb3cb053b2ea21b5f4326a2bf4caa7
SHA256:
C8C174502E92D361132F2FCFD2072D7791799C24477FF95790D2F5D73BED0286
File Size:
1.88 MB, 1877504 bytes
|
Show More
|
MD5:
6fc4d4a66646e8a3ca1a66a721979a85
SHA1:
099055f1e08cf8b537ae8c0e621a6bb0ab559735
SHA256:
90176C56D1294FEE8620FD62208C4DB8567A54CD09789F07EA5E51E157D1CA4A
File Size:
2.82 MB, 2824704 bytes
|
|
MD5:
fbc993cdae076902905f35921e1ed5e3
SHA1:
dab3ef7a9caf0fc7674e9486efb75fe7de59194e
SHA256:
ABB8A72C8A5F0A16C0C8688DB68714219212A440BF208AD8B7323528648516E9
File Size:
649.22 KB, 649216 bytes
|
|
MD5:
559b4cfb906fec35471e9718bb63aaed
SHA1:
e94501961461af98463b1f6920b4b0052c0a4975
SHA256:
E64205045110A2FD06F5E5D7D96D63ED8578C2A243E5C3949933172BBEAA2072
File Size:
8.19 KB, 8192 bytes
|
|
MD5:
65afa3b4cfed6dfcbc7b8e5ff7eb63eb
SHA1:
bb9db41577e63ce3e41feb85f850d3cae4955bb1
SHA256:
10A4557263DE146664C42D1319591E8A909CFF20E9849F9BDE99E5B12F2DF23F
File Size:
10.24 KB, 10240 bytes
|
|
MD5:
b16e799c54bc726753f72302df6f035e
SHA1:
3779612a7bd0cbbdd0721991b9e78ee9d19d3b41
SHA256:
547C1D0A5217C5CB8104EE90D51F75894C199BA7B0C4807426675FB7983E2406
File Size:
752.13 KB, 752128 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have resources
- File doesn't have security information
- File has exports table
- File has TLS information
- File is .NET application
- File is 32-bit executable
- File is 64-bit executable
Show More
- File is console application (IMAGE_SUBSYSTEM_WINDOWS_CUI)
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Assembly Version |
|
| Comments | Background service update and maintenance utility |
| Company Name |
|
| File Description |
|
| File Version |
|
| Internal Name |
|
| Legal Copyright |
|
| Original Filename |
|
| Product Name |
|
| Product Version |
|
File Traits
- .NET
- .vmp0
- 2+ executable sections
- dll
- fptable
- GetConsoleWindow
- HighEntropy
- No Version Info
- ntdll
- VirtualQueryEx
Show More
- vmp section variant
- x64
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 1,836 |
|---|---|
| Potentially Malicious Blocks: | 136 |
| Whitelisted Blocks: | 1,049 |
| Unknown Blocks: | 651 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Files Modified
Files Modified
This section lists files that were created, modified, moved and/or deleted by samples in this family. File system activity can provide valuable insight into how malware functions on the operating system.| File | Attributes |
|---|---|
| c:\users\user\appdata\roaming\docker\stats.log | Read Attributes,Synchronize,Read Control,Write Attributes,Write extended,Append data |
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKLM\software\securityhealthservice::userlogpath | C:\Users\Swvcrddi\AppData\Roaming\Docker\stats.log | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Syscall Use |
Show More
93 additional items are not displayed above. |
| User Data Access |
|
| Anti Debug |
|
| Service Control |
|