Taka Ransomware
The Taka Ransomware is a ransomware Trojan that may be in its development stage currently. Taka is the Japanese word for Eagle. The Taka Ransomware has caught the attention of PC security analysts because of its contact and payment method that is somewhat unconventional. Other than that, the Taka Ransomware seems to take the same approach that has been observed before in countless other ransomware Trojans.
Table of Contents
The Eagle that Lands on Your Computer
The Taka Ransomware infection is typical of these kinds of attacks. The Taka Ransomware is installed without the victim's knowledge. Once the Taka Ransomware is installed, it uses a strong AES encryption algorithm to encrypt the files on the victim's computer. The Taka Ransomware uses RSA to encrypt the AES key, meaning that the victim will no longer have access to the decryption key necessary to decrypt the files. The encrypted files will become inaccessible to the victim; they will be held hostage. Ransomware like the Taka Ransomware demands the payment of a ransom from the victim in exchange for the decryption key that would allow the recovery of the encrypted files. The Taka Ransomware identifies files that it has encrypted using the extension '.xxx,' which is added to the end of all encrypted files' names.
How the Taka Ransomware may be Installed on the Victim’s Computer
The most common way of distributing the Taka Ransomware is through corrupted spam email attachments. Once the victim opens the corrupted file attachment that contains the Taka Ransomware, this threat will download its corrupted executable file from one of several links. The Taka Ransomware can connect to several domains to download its corrupted files; it is highly likely that the con artists responsible for the Taka Ransomware have compromised these domains so that they will host its corrupted executable file. In every case that has been observed by PC security analysts, the corrupted executable file associated with the Taka Ransomware attack is named 'update.exe,' a fairly innocuous name that makes it easy for it to blend in with other content on the compromised server or the victim's download queue.
Once the Taka Ransomware has been downloaded, the corrupted executable file is copied to the directory %PROGRAMFILES(x86)% and is renamed using a six-character name made up of random characters, still with the .exe extension. As soon as the Taka Ransomware is installed, the Taka Ransomware will start encrypting the victim's files. The Taka Ransomware creates its ransom note on the victim's Desktop. This ransom note, named 'help_dcfile.txt' is a simple text note that instructs the victims on how to pay and what has happened to their files. This is a typical approach used by most ransomware Trojans. The Taka Ransomware also will create a task in the Windows Task Scheduler named 'enc' which triggers every time Windows starts up, prompting the corrupted file containing the Taka Ransomware to run and encrypt the victim's files. This means that, unless the Taka Ransomware is properly removed, there is a risk that the victim's files will continue to be encrypted even after the victim has taken steps to recover.
The Payment and Contact Method Used by the Taka Ransomware is Unusual
One of the main reasons why the Taka Ransomware has caught the attention of PC security researchers is that the Taka Ransomware uses an unusual contact method and ransom note. The Taka Ransomware claims that the victim must make a payment to a specific BitCoin address: '1HfaCTfwsVXDitg9SgV8cR8ujYs7ZcKkto.' Once the payment is made, the victim is then instructed to copy the transaction ID of that BitCoin payment and paste it into a form provided by the Taka Ransomware. Only after the victim sends this information will the author of the Taka Ransomware provide the user with both the decryption key and a link to a decryption utility in the form of a public email account. The curious thing about this method is that it does add an extra hurdle for PC security researchers to gain access to the decryption utility. However, this is not a particularly formidable obstacle. It also requires lots of trust on the part of the victim, who already does not have a lot of reasons to trust the con artists responsible for the Taka Ransomware attack! The Bitcoin address used in the Taka Ransomware attacks have not received any payments as of the writing of this report.
SpyHunter Detects & Remove Taka Ransomware
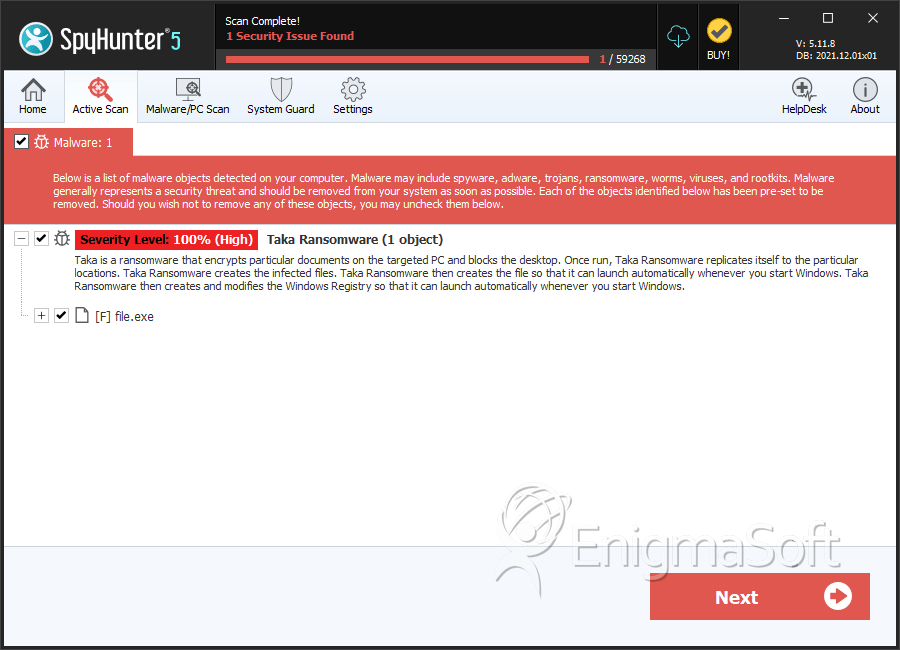
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | f33f662d124288da3d4bee72b81695f9 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.