Simple_Encoder Ransomware
The Simple_Encoder Ransomware is an encryption ransomware Trojan that has attacked victims around the world in recent months. The Simple_Encoder Ransomware is a relative newcomer in relation to the numerous other ransomware threats that are currently in existence. The Simple_Encoder Ransomware is also known as Tilde Ransomware because it appends a tile (the '~' symbol) to every file that was encrypted in the attack. Apart from this distinctive feature, its ransom note and the file it uses to deliver the ransom note to the victim also can recognize the Simple_Encoder Ransomware.
Table of Contents
A Brief Description of the Simple_Encoder Ransomware Attack
The Simple_Encoder Ransomware follows the pattern of attack observed in numerous other encryption ransomware threats. The Simple_Encoder Ransomware may be delivered using a corrupted email attachment or embedded link. As soon as the Simple_Encoder Ransomware enters a computer, it begins using its encryption algorithm to encrypt the victim's files. After encrypting the victim's files, the Simple_Encoder Ransomware drops ransom notes in each directory where it has encrypted content. The Simple_Encoder Ransomware's ransom notes are named '_RECOVER_INSTRUCTIONS.ini.' The Simple_Encoder Ransomware targets the following file types on the victim's computer, making all of these files essentially useless:
.mid, .key, .crt, .csr, .pem, .DOC, .odt, .ott, .sxw, .stw, .PPT, .XLS, .pdf, .RTF, .uot, .CSV, .txt, .xml, .max, .DOT, .docx, .docm, .dotx, .dotm, .hwp, .ods, .ots, .sxc, .stc, .dif, .xlc, .xlm, .xlt, .xlw, .slk, .xlsb, .xlsm, .xlsx, .xltm, .xltx, .wks, .odp, .otp, .sxi, .sti, .pps, .pot, .sxd, .std, .pptm, .pptx, .potm, .potx, .uop, .odg, .otg, .sxm, .mml, .docb, .ppam, .ppsx, .ppsm, .sldx, .sldm, .ms11 (Security copy), .lay, .lay6, .asc, .SQLITE3, .SQLITEDB, .sql, .mdb, .dbf, .odb, .frm, .MYD, .MYI, .ibd, .mdf, .ldf, .php, .cpp, .pas, .asm, .vbs, .dip, .dch, .sch, .brd, .asp, .java, .jar, .class, .bat, .cmd, .psd, .NEF, .tiff, .tif, .jpg, .jpeg, .cgm, .raw, .gif, .png, .bmp, .svg, .djvu, .djv, .zip, .rar, .tgz, .tar, .bak, .tbk, .tar.bz2, .PAQ, .ARC, .aes, .gpg, .vmx, .vmdk, .vdi, .qcow2, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mkv, .flv, .wma, .mp3.
The ransom note associated with the Simple_Encoder Ransomware contain the following message:
'All your system is encrypted.
All your files (documents, photos, videos) were encrypted.
It's impossible to get access to your files without necessary decrypt key.
All your attempts to solve problem yourself will be unsuccessful!
We suggest you to read some articles about this type of encryption:
https://en.wikipedia.org/wiki/RSA_(cryptosystem)
https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Now you have two options to solve the problem:
1. Format your hard disk. This way you'll lose all your files.
2. Pay 0.8 Bitcoin and get key of decryption. At the end of this ad
you'll see your personal ID and our contact information.
Now you should send us email with your personal ID. This email
will be as confirmation you are ready to pay for decryption key.
After payment we'll send you key of decryption with instructions
how to decrypt the system.
Please, don't send us emails with threats. We don't read it and don't reply!
We guarantee we'll send you the decryption key after your payment
so you'll get access to all your files.
Our e-mail address: one1uno243@yandex.com
YOUR PERSONAL IDENTIFIER: [redacted]'
Preventing a Simple_Encoder Ransomware Attack
Making sure that your files are backed up regularly can prevent these attacks. Having backups of all important files will make you invulnerable to this threat attack. If you can recover your files from the backup immediately, then the con artists responsible for the Simple_Encoder Ransomware have no more leverage when trying to extort you. This is one of the reasons why it is currently so important that backing up content become a widespread habit for computer users. When the majority of computer users have protected themselves adequately, then the creators of the Simple_Encoder Ransomware and similar threats will no longer have an incentive to continue to develop and distribute such content.
SpyHunter Detects & Remove Simple_Encoder Ransomware
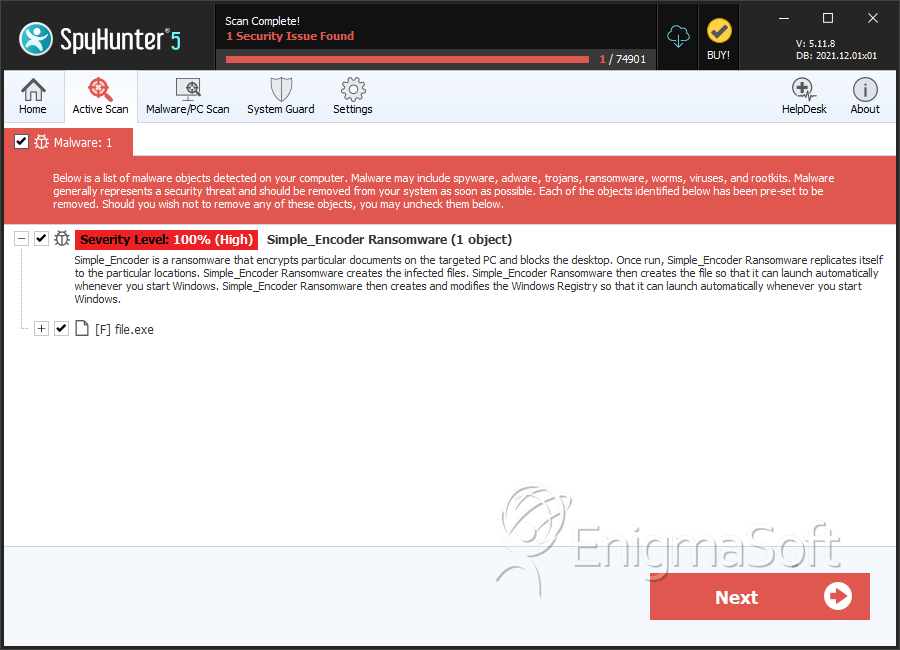
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 3d83ed39ffc379a1608a7a341fc01e33 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.