Schwerer Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | April 20, 2017 |
| Last Seen: | January 9, 2019 |
| OS(es) Affected: | Windows |
The Schwerer Ransomware is a ransomware Trojan that is designed to enter a computer, encrypt the victim's files, and then asks for the payment of a ransom of $150 USD in BitCoin from the victim. The Schwerer Ransomware takes the victim's files hostage in exchange for ransom. The Schwerer Ransomware will encrypt files on all local disks, as well as on files shared on the network of the infected PC. The Schwerer Ransomware is very similar to numerous ransomware Trojans active currently, the CryptoWire and its variants particularly since they are all written using the AutoIt coding language. Although its name seems German, PC security researchers have noted that the Schwerer Ransomware uses an English-language ransom note and seems to be designed to attack English speakers.
Table of Contents
Computer Users Infected by the Schwerer Ransomware Have a Free Way Out
The Schwerer Ransomware receives its name because the program window in which it delivers its ransom note is named 'Schwerer.' Once the Schwerer Ransomware ransom note appears, it means that the victim's files have already been encrypted and it is too late to halt the Schwerer Ransomware attack. A reliable security program, however, can intercept the Schwerer Ransomware infection before it manages to compromise the victim's files. The Schwerer Ransomware runs in the background, encrypting the victim's files without alerting the victim until it is too late to stop the attack. The Schwerer Ransomware targets a wide variety of file types, attempting to encrypt the files generated by the user such as presentations, text documents, videos, photos, spreadsheets, databases, eBooks, and files generated by commonly used software such as Adobe Photoshop or AutoCAD. The Schwerer Ransomware, after encrypting the victim's files, delivers its ransom note in a program window titled Schwerer. The Schwerer Ransomware ransom note contains the following message:
'All your computer file were encrypted with AES, only we can restore your files.
How to restore files :
Files encrypted : [NUMBER OF LOCKED FILES]
1. Send email to 897698@mail2tor.com containing your personal identifier (it is below)
2. We will send you a Bitcoin address, you must send 150€ to it within 3 days.
IF YOU DO NOT UNDERSTAND BITCOIN EMAIL WILL CONTAIN INFORMATIONS
3. Once full amount is sent you email us again. (make sure to contain key)
A. We will send you key and you will paste into textbox below, that will restore files.
Your Identifier: [43 RANDOM CHARACTERS]
Restore key: [TEXT BOX]
[Restore files]'
Dealing with a Schwerer Ransomware Infection
Although in the case of most ransomware Trojans it may be impossible to recover the files once they have been encrypted, computer users affected with the Schwerer Ransomware can call themselves lucky thanks to the fact that Jiri Kropac has created a decryptor and released it online. However, it is likely that this decryption utility is only a temporary solution, since updates to the Schwerer Ransomware Trojan may nullify this decryptor and use a stronger method to make the victim's files inaccessible completely. Furthermore, you should ensure that you are protected against other ransomware Trojans besides the Schwerer Ransomware since they are becoming ever more popular. The best protection against ransomware Trojans is to have file backups.
Taking Preventive Measures against the Schwerer Ransomware and Other Ransomware Trojans
The best protection against all ransomware Trojans is to have file backups on an external device or the cloud ( not synchronized to prevent the backups themselves from becoming encrypted too). If computer users can recover their files from a backup copy quickly, then the people responsible for the ransomware Trojan lose any power they have over the victim. Apart from having file backups, computer users should learn how to handle spam email messages and unsolicited email attachments since these are the main way in which these threats are spread. A security program that is fully up to date also can prevent the Schwerer Ransomware and other ransomware from encrypting the victim's files.
SpyHunter Detects & Remove Schwerer Ransomware
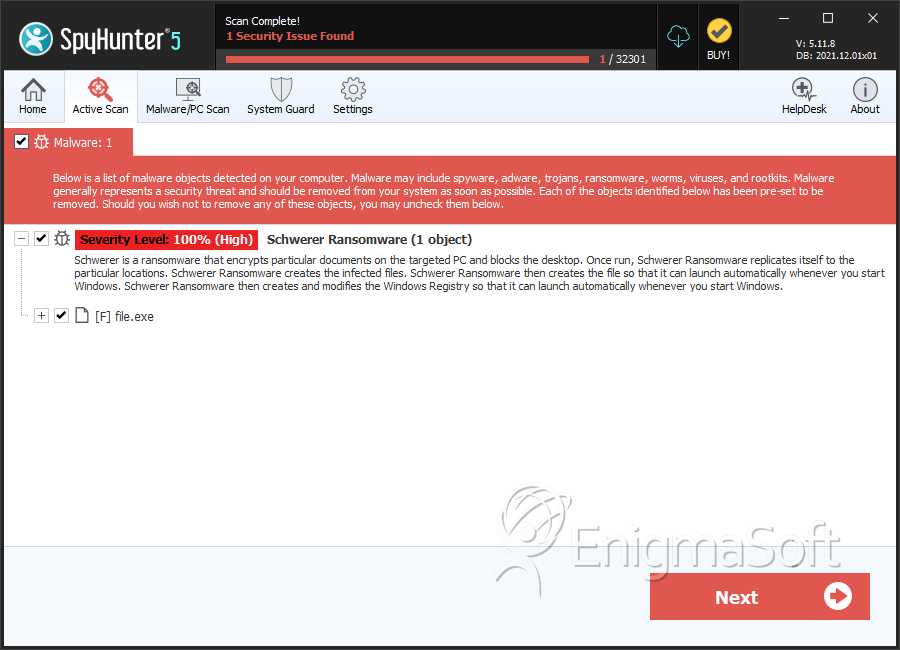
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 3400d0f64623b161fd211c0044557af8 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.