Pony Botnet
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 624 |
| First Seen: | July 9, 2013 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The Pony botnet is a very large botnet that was uncovered recently, in the Summer of 2013. The Pony botnet is similar to some of the most common botnets active today. The Pony botnet controller includes a control panel and advanced features that allow the criminals controlling the Pony botnet to gather data, keep records and statistics and control the botnet effectively from a single location. There's a sharp rise of attacks involving the Pony botnet and malware designed to integrate infected computer systems into this dangerous botnet. Currently, the Pony botnet is in version 1.9 and has the capacity to steal hundreds of thousands of passwords and sensitive data per day.
Table of Contents
The Attacks Involving the Pony Botnet
The Pony botnet has been involved in a large number of attacks. The most affected Web browser is Firefox, with Google Chrome in second place and Internet Explorer in third. The Pony botnet can also steal information from email clients and FTP clients, with the most affected email client being Outlook. However, the main purpose of the Pony botnet is to steal sensitive information such as website login credentials and passwords for email and social networks. This information can then be used to send out massive quantities of spam email messages or steal money from victims. Among the most affected websites are Facebook, Yahoo and Google, with hundreds of thousands of stolen email accounts and thousands of stolen FTP credentials.
Avoid Becoming a Victim of the Pony Botnet
A botnet is essentially a large network of computer systems infected with malware that allows criminals to control them all simultaneously. This control allows criminals to carry out massive Distributed Denial of Service attacks or send out billions of spam email messages. To become part of a botnet, a computer will usually have to be infected with a dangerous Trojan infection that allows criminals to gain remote access to the infected computer. To prevent these kinds of attacks, it is important to protect your computer with a reliable anti-malware program which should be always kept up to date.
SpyHunter Detects & Remove Pony Botnet
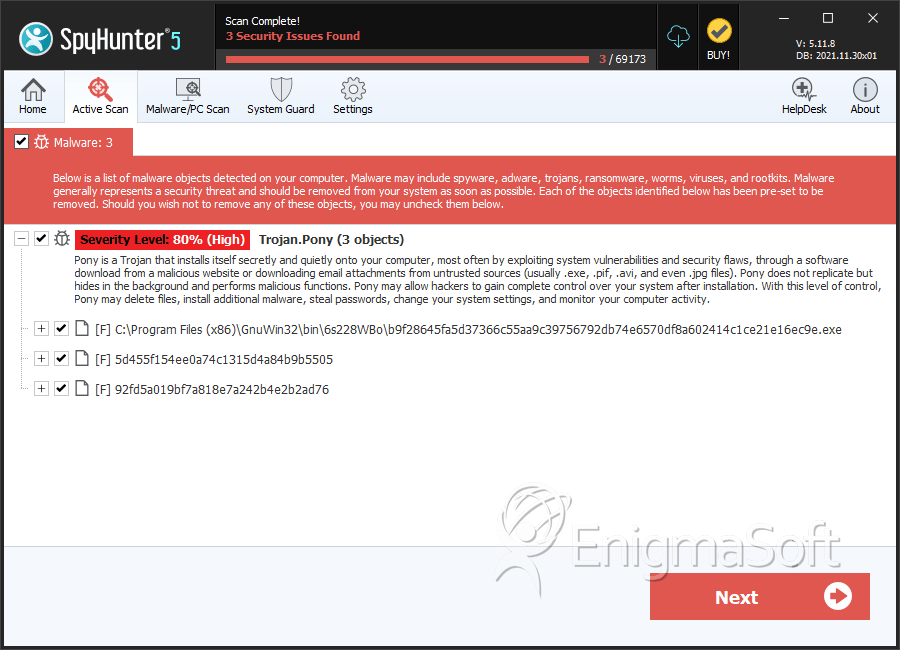
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | b9f28645fa5d37366c55aa9c39756792db74e6570df8a602414c1ce21e16ec9e.exe | de1c9462d43c8a6a17a101f4a4840bd6 | 2 |
| 2. | 5d455f154ee0a74c1315d4a84b9b5505 | 5d455f154ee0a74c1315d4a84b9b5505 | 1 |
| 3. | 92fd5a019bf7a818e7a242b4e2b2ad76 | 92fd5a019bf7a818e7a242b4e2b2ad76 | 0 |
