OzoneRAT
OzoneRAT is a Remote Administration Tool (RAT). These programs have important legitimate uses. For example, they allow a technical support service to repair machines in another geographical location, or employers to monitor their employee's activity. Unfortunately, RATs also may be used by con artists to carry out threat attacks. The same remote access capabilities that allow legitimate computer users to control a computer remotely may allow con artists to take control of a computer and use it for a variety of illegitimate uses. OzoneRAT is being distributed through a spam email campaign that is designed to target German-speaking computer users. OzoneRAT is a relatively new RAT that is available commercially.
Table of Contents
How OzoneRAT may Be Distributed
Spam email messages associated with OzoneRAT may contain a subject line that makes it seems as if the email contains a billing statement for a 'Cable service.' This corrupted email contains a file attachment that is a Microsoft Word document. Although computer users may not associate Microsoft Word documents with threats, this is quite a common way of distributing them. These threatening documents exploit macros that allow the con artist to execute corrupted code on the victim's computer. These email messages use an old-fashioned technique that involves tricking computer users into clicking on a 'thumbnail' image twice, which is a corrupted Javascript that initiates OzoneRAT's attack.
The Infection Process Used by OzoneRAT
The corrupted script associated with the OzoneRAT attack will install a bogus SSL Certificate that may create proxies on the three most popular Web browsers for the Windows operating system; Internet Explorer, Mozilla Firefox and Google Chrome. These proxies will lead to a TOR URL, an anonymous address in the Dark Web. Through these proxies, the con artists controlling OzoneRAT can force computers to visit phishing pages or a variety of other corrupted websites that can then be used to collect online passwords, credit card numbers and online banking accounts. OzoneRAT will be installed on the victim's computer downloaded from OzoneRAT's Command and Control server in its full version in a DLL file. OzoneRAT is installed on the victim's computer by covert techniques that allow OzoneRAT to avoid detection. OzoneRAT has been commercially available for one year. Clients of OzoneRAT can purchase a $20 standard package or a $50 USD 'Platinum' package, with a lifetime license and additional features that allow the user to mine BitCoins and build corrupted files that exploit Microsoft Word vulnerabilities.
OzoneRAT Has Multiple Capabilities
OzoneRAT provides its users with an easy to use interface, typical of modern RAT's. This interface allows the controller to see which servers and ports are being used. Unfortunately, not a lot of expertise is required to operate OzoneRAT, meaning that this threat puts considerable power into the hand of con artists that wouldn't otherwise be able to build and use this threat component. There are numerous RAT operations that can be carried out with OzoneRAT, including simple file operations and controlling the victim's computer from a remote Desktop. OzoneRAT has one advanced feature that is not available in many other RATs, which allows the attacker to control the infected computer in a way that is completely invisible to the victim. OzoneRAT's website claims that OzoneRAT should not be used for illegal or harmful purposes, although this is clearly not something they mean since it includes such features as the exploit builder and the ability to hide from the victim.
What's important to understand about OzoneRAT is that this threat, which gives con artists full power over the victim's computer, is being distributed in a spam email campaign that relies on victims clicking on an image and opening an unsolicited email attachment. This is where one can see just how it crucial it is to establish safe online protocols and security measures.
SpyHunter Detects & Remove OzoneRAT
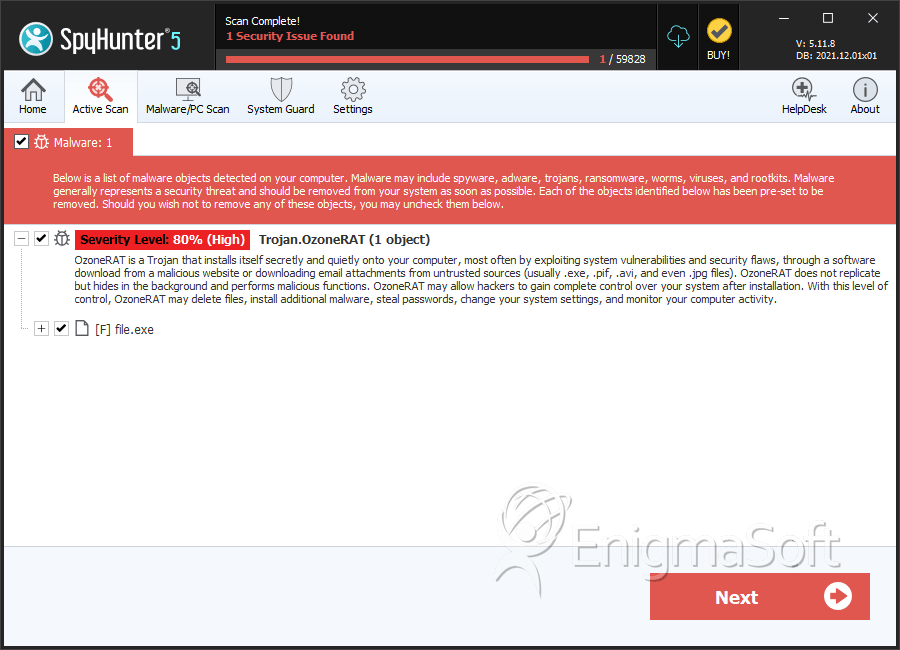
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 1d6510c0503e6702cde6fa6c3375711c | 0 |
| 2. | file.exe | 5b47d516fe9ecb7bc1d3eb6d4631e274 | 0 |
| 3. | file.exe | 199fc3fdc3bd77d7f0c04232b15a3b12 | 0 |
| 4. | file.exe | c00ca3114f32f880ee0d712a20d07b3d | 0 |
| 5. | file.exe | da2b37ed0761698b36018fe3b30170d8 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.