Mobef Ransomware
The Mobef Ransomware is one of the countless encryption ransomware Trojans that have appeared in the last year. Like other encryption ransomware threats, the Mobef Ransomware takes over a computer by encrypting its victim's files and then asking for a ransom to decrypt these files. The Mobef Ransomware will change the affected files' extensions and display a ransom note in the form of text and HTML files dropped in the folders containing the encrypted files. The Mobef Ransomware will also change the affected computer's Desktop wallpaper image into a ransom note with instructions on payment.
Table of Contents
How the Mobef Ransomware may Make Computer Users Pay Its Ransom
The Mobef Ransomware may be delivered in the form of a corrupted email attachment that may be a zipped file that hides a corrupted script. When the Mobef Ransomware enters a computer, it runs in the background and starts encrypting the victim's files. In its configuration data, the Mobef Ransomware contains a long list of file extensions; the Mobef Ransomware searches for these file types and encrypts them using an advanced encryption algorithm. The decryption key is stored on remote servers controlled by the Mobef Ransomware's creators. The con artists will not provide the decryption key until the victim's pay an enormous ransom amount. The Mobef Ransomware currently demands payment of four BitCoins, which is almost $2000 USD at the average exchange rate. This is quite high by ransomware standards because the demanded payments are between 0.5 and 1.5 BitCoin. In any case, computer users should avoid paying this extraordinary amount. Prevention is the key to dealing with the Mobef Ransomware and similar threats and using a backup on an external memory device or the cloud will cost a tiny fraction of what it would cost to pay the con artists to recover from a Mobef Ransomware attack.
Preventing the Mobef Ransomware Attacks
There have been an outstanding rise in the Mobef Ransomware and similar ransomware attacks in the last two years. This is in part because ransomware has become freely available to con artists through the rise of the RaaS (Ransomware as a Service) industry. This is a service that con artists provide, allowing other con artists to create their own customized ransomware threats easily. In fact, most of these ransomware threats are virtually identical, only differing in the amount demanded and the details of the ransom notes. The best prevention practice is to ensure that all files are backed up on an external memory device or the cloud. Avoid opening unsolicited email attachments that could be used to deliver the Mobef Ransomware. PC security researchers recommend a good anti-spam solution to ensure that corrupted emails such as those associated with the Mobef Ransomware do not land in your inbox in the first place. The following is an example of a ransom note used by the Mobef Ransomware:
YourID: -
PC: -
USER: -
*********
Hi there
Your files are now encrypted. I have the key to decrypt them back.
I will give you a decrypter if you pay me. Email me at:
momsbestfriend_@_protonmail.com or torrenttracker_@_india.com
If you don't get a reply or if both emails die, then contact me using a guaranteed, foolproof Bitmessage:
download it form here hxxps://github.com/mailchuck/PyBitmessage/releases/download/v0.5.8/Bitmessage-0.5.8.exe
Run it, click New Identity and then send me a message at BM-NBvzKEY8raDBKb9Gp1xZMRQpeU5svwg2
Just remember that Bitmessage is slow, it takes 5 minutes to send a message and 15 to get a reply.
Cheers
P.S. WARNING!!!!! Don't delete this file: 427047.txt
Some of the files that are encrypted during the Mobef Ransomware attack include:
.3ds, .4db, .4DD, .7z, .7zip, .accdb, .accdt, .aep, .aes, .ai, .arj, .axx, .bak, .bpw, .cdr, Cer, .crp , .crt, .csv, .db, .dbf, .dbx, .der, .doc, .docm, .docx, .dot, .dotm, .dotx, .dwfx, .dwg, .dwk, .dxf,. eml, eml, .fdb, .gdb, .gho, .gpg, .gxk, .hid, .idx, .ifx, .iso, .kdb, .kdbx, .key, .ksd, .max, .mdb, .mdf, .mpd, .mpp, .myo, .nba, .nbf, nsf, .nv2, .odb, .odp, ods, odt, .ofx, p12, .pdb, .pdf, .pfx , .pgp, .ppj, pps, .ppsx, .ppt, .pptx, .prproj, .psd, .psw, .qba, .qbb, .QBO, .QBW, .qfx, .qif, .rar,. raw, rpt, .rtf, .saj, .sdc, .sdf, .sko, .sql, .sqllite, .sxc, .tar, .tax, .tbl, tib, .txt, .wdb, .xls, .xlsm, .xlsx, .xml, .zip.
SpyHunter Detects & Remove Mobef Ransomware
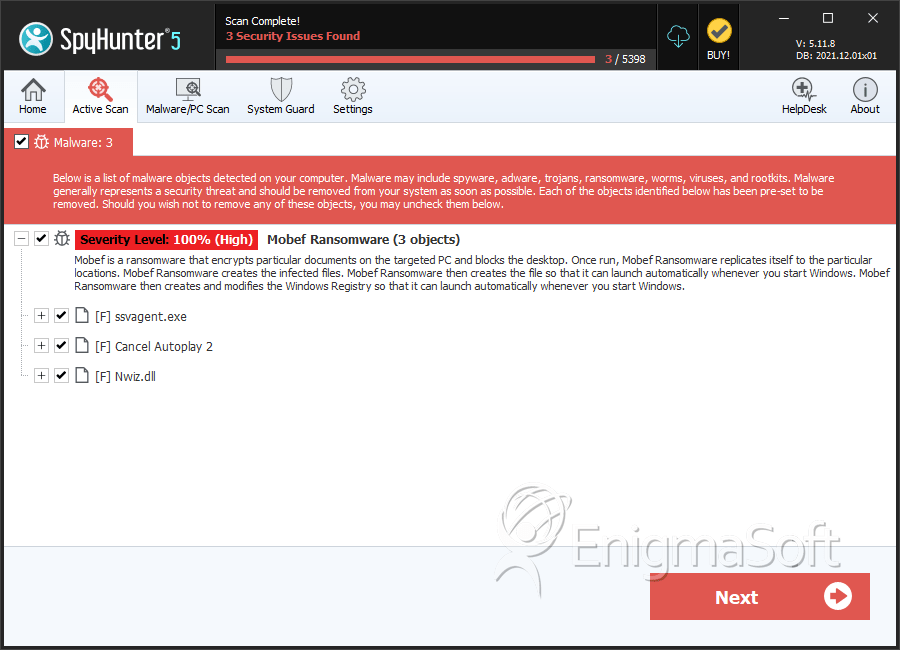
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ssvagent.exe | af97e29f412dceeadd8b1e2411113846 | 0 |
| 2. | Cancel Autoplay 2 | 116d442d8ec5c62f32c7ba507a5569be | 0 |
| 3. | Nwiz.dll | a1dd4a627a9a3d4dc68df7ebeaa9ead4 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.