Marlboro Ransomware
A new ransomware family known as Marlboro Ransomware was reported recently. Fortunately, in less than 24 hours, malware researchers tracked down the Marlboro Ransomware infection, analyzed it, and released a decryption program. The Marlboro Ransomware was first observed on January 12, being spread through spam email messages. These messages include a corrupted Microsoft Word attachment that downloads and installs the Marlboro Ransomware on the victim's computer. If your machine has been exposed to the Marlboro Ransomware, malware researchers recommend using the available decryption utility to restore the affected files after removing the Marlboro Ransomware completely with the help of a reliable security application.
Table of Contents
The Marlboro Ransomware is Related to a Highly Sophisticated Spam Campaign
The Marlboro Ransomware exists in two versions currently, targeting 32-bit and 64-bit versions of the Windows operating system. During the infection, the Marlboro Ransomware will drop two different installers on the victim's computer. This technique is observed in ransomware threats frequently, although it may be used by other threats, such as banking Trojans and Point of Sale (PoS) threats. The Marlboro Ransomware is downloaded from free online hosting providers, which have already suspended the Marlboro Ransomware's accounts (although it is likely that new ones will appear to take their places.) Although the Marlboro Ransomware was decryptable and its hosting was publicly available, the spam campaign associated with the Marlboro Ransomware is quite sophisticated.
There is a Small Mal-Function in the Marlboro Ransomware’s Decryptor
The encryption method used by the Marlboro Ransomware is not particularly strong. The Marlboro Ransomware uses the XOR encryption, which was cracked by malware analysts almost as soon as the Marlboro Ransomware infection was detected for the first time. The files encrypted by the Marlboro Ransomware will be identified by the addition of the file extension '.oops' to the end of each file name. The Marlboro Ransomware drops its ransom note in the form of an HTML file named '_HELP_Recover_Files_.html' on the victim's computer. The Marlboro Ransomware's ransom note claims that a typical, stronger method of encryption (a combination of RSA and AES encryption) was used during the attack. Below is the full text of the Marlboro Ransomware ransom note:
'!!! IMPORTANT INFORMATION !!!
All of your files are encrypted with RSA-2048 and AES-128 ciphers.More information about RSA and AES can be found here:
https://en.wikipedia.org/wiki/RSA_(cryptosystem)
https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Decrypting of your files is only possible with private key and decrypt program, which is on our secret server.
To receive your private key you need to make payment to us.
After you make payment run program called ‘DecryptFiles' that is located on your Desktop and your Documents.
Program will automatically decrypt all of your files!
If you try to decrypt files with another software your files can be forever lost.
How to buy decrypter?
1. You can make a payment with BitCoins, there are many methods to get them.
2. You should register BitCoin Wallet
3. Purchase Bitcoins – Althought it is not very easy to buy bitcoins, it is getting simpler every day.
Here are our recommendations:
Localbitcoins.com (WU) – Buy Bitcoins with Western Union
Coincafe.com – Recommended for fast, simple service.
Localbitcoins.com Service allows you to search for people in your community willing to sell bitcoins to you directly.
CEX.IO – Buy Bitcoins with VISA/MASTERCARD or Wire Transfer
btcdirect.eu – THE BEST FOR EUROPE
4. Send 0.2 BTC to Bitcoin address:
5. After you make payment, run program called ‘DecryptFiles'that is located on your Desktop and your Documents.
Program will automatically decrypt all of your files!'
During its attack, the Marlboro Ransomware also drops a decryptor named 'de Marlboro,' which connects to the Command and Control server to check for the ransom payment and then decrypts the victim's files. Fortunately, PC security researchers were able to take advantage of the presence of this decryptor to develop a decryption utility that is now available to computer users affected by this threat. One small problem with the decryptor is that the Marlboro Ransomware infection will truncate a tiny portion of each file it encrypts, which cannot be reconstructed by the decryption utility. However, for most files, this will not be a significant problem.
The file types targeted by the Marlboro Ransomware include the following:
ARC,.DOC,.DOT,.MYD,.MYI,.NEF,.Ott,.PAQ,.PPT,.RTF,.SQLITE3,.SQLITEDB,.XLS,.aes,.asc,.asf,.asm,.asp,.aspx,.avi,.bak,.bat,.bmp,
.brd,.bz2,.class,.cmd,.com,.cpp,.crt,.csr,.csv,.dat,.dbf,.dch,.dif,.dip,.djv,.djvu,.docb,.docm,.docx,.dotm,.dotx,.fla,.flv,.frm,.gif,.gpg,
.hwp,.ibd,.jar,.java,.jpeg,.jpg,.key,.lay,.lay6,.ldf,.max,.mdb,.mdf,.mid,.mkv,.mml,.mov,.mp3,.mpeg,.mpg,.ms11,.not,.odb,.odg,.odp,
.ods,.odt,.otg,.otp,.ots,.pas,.pdf,.pem,.php,.png,.pot,.potm,.potx,.ppam,.pps,.ppsm,.ppsx,.pptm,.pptx,.psd,.qcow2,.rar,.raw,.sch,
.sldm,.sldx,.slk,.sql,.stc,.std,.sti,.stw,.svg,.swf,.sxc,.sxd,.sxi,.sxm,.sxw,.tar,.tar,.tbk,.tif,.tiff,.txt,.tz,.uop,.vbs,.vdi,.vmdk,.vmx,.vob,
.wav,.wks,.wma,.wmv,.xlc,.xlm,.xlsb,.xlsm,.xlsx,.xlt,.xltm,.xltx,.xlw,.xml,.zip.
SpyHunter Detects & Remove Marlboro Ransomware
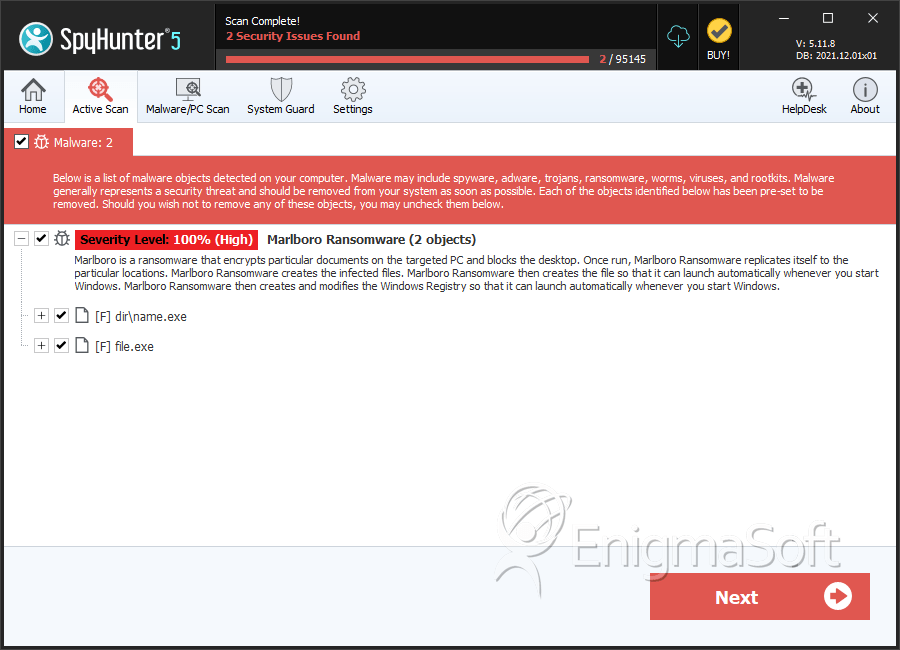
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | name.exe | 5f897b051235b788e52927e8eec07669 | 0 |
| 2. | file.exe | 9c7a41fbe431a41bfdf933436c846858 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.