Kraken Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 246 |
| First Seen: | December 13, 2016 |
| Last Seen: | September 11, 2021 |
| OS(es) Affected: | Windows |
The Kraken Ransomware is named after the title of the ransom note displayed on the victim's screen. Apparently, the designers behind the Kraken Ransomware are not as creative as those behind the Jigsaw Ransomware and the Mahasaraswati Ransomware, which include a mascot so to speak. The Kraken Ransomware is spread among users via spam emails, links that lead to compromised pages, and executable with a double extension that may appear as benign documents.
Table of Contents
What Encryption Standards are Supported by the Kraken Ransomware
The Kraken Ransomware is a standard encryption Trojan that is programmed to append the '.kraken' suffix to encrypted files and encode their names using base64 algorithm. The Kraken crypto-threat is using the AES-256 cipher to encrypt the contents of data containers that are used to store images, presentations, audio, videos, databases and spreadsheets. We have seen the Kraken Ransomware corrupt the following filetypes:
.3GP, .7Z, .APK, .AVI, .BMP, .CDR, .CER, .CHM, CONF, .CSS, .CSV, .DAT, .DB, .DBF, .DJVU, .DBX, .DOCM, ,DOC, .EPUB, .DOCX .FB2, .FLV, .GIF, .GZ, .ISO .IBOOKS,.JPEG, .JPG, .KEY, .MDB .MD2, .MDF, .MHT, .MOBI .MHTM, .MKV, .MOV, .MP3, .MP4, .MPG .MPEG, .PICT, .PDF, .PPS, .PKG, .PNG, .PPT .PPTX, .PPSX, .PSD, .RAR, .RTF, .SCR, .SWF, .SAV, .TIFF, .TIF, .TBL, .TORRENT, .TXT, .VSD,.WMV, .XLS, .XLSX, .XPS, .XML, .CKP, ZIP, .JAVA, .PY, .ASM, .C, .CPP, .CS, .JS, .PHP, .DACPAC, .RBW, .RB, .MRG, .DCX, .DB3, .SQL, .SQLITE3, .SQLITE, .SQLITEDB, .PSD, .PSP, .PDB, .DXF, .DWG, .DRW, .CASB, .CCP, .CAL, .CMX, .CR2.
The Kraken Ransomware Behaves Like the Donald Trump Ransomware
In-depth analysis showed that the Kraken Ransomware functions similarly to the Donald Trump Ransomware, but there appears to be no direct connection between those projects. The Kraken Ransomware can encode data stored on local drives, removable media and network shares connected to the infected computer. As stated above, file content and name is encoded simultaneously. While the content is enciphered with an AES-256 algorithm, the names are transcoded using a simple base64 algorithm. For example, 'wild rye.pptx' is transformed to 'd2lsZCByeWU=.kraken' and the ransom demand is delivered to the desktop in '_HELP_YOUR_FILES.html,' which you can open with your Internet client.
'KRAKEN
Your documents, photos, databases and other important files have been encrypted!
Decryption of your files is only possible with the special decryption program.
To buy your decryption program follow the steps below.'
A Kraken Decryptor is Offered for Purchase with Bitcoins
Experts do not encourage paying the ransom, which varies across the versions of the Kraken Ransomware. Samples that were recovered from the machines of compromised users reveal that the operators of the Kraken Ransomware may offer a decryption tool named 'Kraken Decryptor' for prices that range between 0.25 BTC and 1 BTC, which translates to 195 USD and 781 USD. Unfortunately, there isn't a free decryptor for users who were affected by the Kraken Ransomware and your options for recovery are limited. The copies made by the Shadow Volume Service on Windows may be unaffected, and you may be able to use them to rebuild your data. However, threats such as the CryptoLocker Ransomware and the Vo_ Ransomware tend to delete those copies, and you should be prepared to create backups manually and use utilities like Google Drive. The complete removal of the Kraken Ransomware should be processed with a reliable anti-malware scanner that can recognize and delete threatening objects on your system.
Update October 1st, 2018 — Kraken Cryptor 1.6 Ransomware
The release of the Kraken Cryptor 1.6 Ransomware exhibited small changes to the encryption routine and a new file infrastructure. The samples acquired by researchers were obtained from phishing pages leveraging the Fallout Exploit Kit. Given the small changes observed in the code of the Kraken Cryptor v1.6, some researchers referred to it as the 'Kraken Cryptor: Fallout Edition.' User reports and lab tests confirmed that the Kraken Cryptor 1.6 Ransomware included a new ransom note titled '# How to Decrypt Files-[random_extension].html.' The threat continues to refer to the 'onionhelp@memeware.net' email account as the primary center for users who are looking for a 'Kraken Decryptor.' This time around, the Kraken Cryptor team added a BitMessage account — BM-2cWdhn4f5UyMvruDBGs5bK77NsCFALMJkR@bitmessage.ch that victims could contact in case they are willing to pay for the decryption service. The body of the message in '# How to Decrypt Files-[random_extension].html' was preserved compared to earlier versions and the only difference was the inclusion of the BitMessage account. Detection names for the Kraken Cryptor 1.6 Ransomware include:
Artemis!99829D5483EF
Msil.Trojan.Selfdel.Huza
Ransom/W32.Kraken.109056
Ransom_KRAKEN.THAOOHAH
Trojan ( 0053d3441 )
Trojan.GenericKD.40562119
Trojan.MulDrop8.44704
W32/Trojan.ZBHD-0614
Win32/Trojan.Ransom.84d
malicious_confidence_90% (D)
Update October 15th, 2018 — Kraken Cryptor 2.0.4 Ransomware
Researchers tagged the updated version of the Kraken Cryptor on October 19th, 2018 as the Kraken Cryptor 2.0.4 Ransomware. The name is based on comments from the threat authors found during a detailed analysis of the new samples retrieved from compromised users. However, the majority of updates in the v2.0.4 compared to v1.5 listed above encompass bug fixes and new network protocols. The Kraken Cryptor 2.0.4 Ransomware was found to communicate with a TOR-based server on 'kraken656kn6wyyx.onion' using a TOR2WEB proxy service. Lab tests showed that the threat might run on infected hosts as 'Main.exe' and support anti-debugging and geo-location features. The threat actors appear to segment their development of new versions and deploy highly customized encryption software aimed at PC users in more than fifteen countries. Also, the price for decryption services was lowered to 0.075 Bitcoin (≈482 USD/422 EUR) in the ransom note. The threat feature two new email accounts for contact with the ransomware operators — 'nikolatesla@cock.li' and 'nikolateslaproton@protonmail.com.'. Detection names for the Kraken Cryptor 2.0.4 Ransomware include:
HEUR:Trojan.MSIL.TorJok.gen
MSIL/Filecoder.PI!tr.ransom
Ransom_KRAKEN.THJAIAH
Trojan ( 0053c9261 )
Trojan.Generic.D1DD54E1
Trojan.GenericKD.31282401
Trojan.IGENERIC
Trojan.MSIL.kgvf
Trojan/Win32.Agent.C2755621
W32/Trojan.RDPF-8809
Win32/Trojan.Ransom.601
Win32:RansomX-gen [Ransom]
a variant of MSIL/Filecoder.PI
Update October 19th, 2018 — Kraken Cryptor 2.0.5 Ransomware
The Kraken Cryptor 2.0.5 Ransomware is categorized as the second major update to the Kraken Cryptor Ransomware. Samples of the Kraken Cryptor 2.0.5 Ransomware include the file description 'Researchers Editon: Zero Resistance,' and it is suspected that the threat might be intended as an offense towards computer security researchers. The Kraken Cryptor 2.0.5 Ransomware is reported to encipher nearly three hundred file types and sport a relatively small size for its capabilities. The Kraken Cryptor 2.0.5 Ransomware is reported to encrypt standard and uncommon data containers. Filenames receive the '.JLQUF' extension and something like 'Church of Our Lady Victorious.pptx' is renamed to 'Church of Our Lady Victorious.pptx.JLQU.' This time the ransom message is packed as 'Instructions.txt,' and it is dropped to the user's desktop. The content of 'Instructions.txt' reads:
'All your files has been encrypted by "KRAKEN CRYPTOR"
Read the following instructions carefully to decrypt your files.
-----BEGIN KRAKEN ENCRYPTED UNIQUE KEY-----
[random characters]
-----END KRAKEN ENCRYPTED UNIQUE KEY-----
(What happened to my computer)?
All of your files such as documents, images, videos and other files with the different names and extensions are encrypted by "KRAKEN CRYPTOR". Don't delete '.JLQUF' files! there are not virus and are your files, but encrypted!
The speed, power and complexity of this encryption have been high and if you are now viewing this guide.
It means that "KRAKEN CRYPTOR" immediately removed form your system!
No way to recovery your files without "KRAKEN DECRYPTOR" software and your computer "UNIQUE KEY"!
You need to buy it from us because only we can help you!
(How can recovery my files)?
We guarantee that you can recover all your files soon safely.
You can decrypt one of your encrypted smaller file for free in the first contact with us.
For the decryption service, we also need your "KRAKEN ENCRYPTED UNIQUE KEY" you can see this in the top!
Are you want to decrypt all of your encrypted files? If yes! You need to pay for decryption service to us!
After your payment made, all of your encrypted files has been decrypted.
(How much is need to pay)?
You need to pay 0.075 BTC, payment only can made as Bitcoins.
This links help you to understand whats is a Bitcoins and how it work.
h[tt]ps://en.wikipedia[.]org/wiki/Bitcoin
This price is for the contact with us in first week otherwise it will increase.
(Where can buy Bitcoins)?
The easiest way to buy Bitcoins is LocalBitcoins website.
You must register on this site and click "BUY Bitcoins" then choose your country to find sellers and their prices.
h[tt]ps://localBitcoins[.]com
Other places to buy Bitcoins in exchange for other currencies worldwide: h[tt]ps://www.bestbitcoinexchange[.]io
(How to contact you)?
We use best and easy way to communications. It's email support, you can see our emails below. Please send your message with same subject to both address.
E-Mail: nikolatesla@cock.li
Alternative: nikolateslaproton@protonmail.com
(Attention)
DON'T MODIFY OR RENAME ENCRYPTED FILES.
DON'T MODIFY "KRAKEN ENCRYPT UNIQUE KEY".
DON'T MODIFY "KRAKEN ENCRYPT UNIQUE KEY".
DON'T ASK PEOPLE OR DATA RECOVERY CENTERS, THEY ARE MAY ADD EXTRA CHARGE.
(Additional)
Project "KRAKEN CRYPTOR" doesn't damage any of your files, this action is reversible if you follow the instructions above. Also, our policy is obvious: "NO PAYMENT, NO DECRYPT"!'
The Kraken Cryptor 2.0.5 Ransomware continues to use the emails — 'nikolatesla@cock.li' and 'nikolateslaproton@protonmail.com.' The Kraken Cryptor 2.0.5 Ransomware uses the TOR Network to hide its data transmissions and prevent computer security companies from assisting law enforcement agencies in tracking the origin of this crypto-threat attacks. Unfortunately, you can’t restore the data affected by the Kraken Cryptor 2.0.5 Ransomware unless you are prepared for such an occasion and have backup copies on a separate memory drive.
Update October 21st, 2018 — Kraken Cryptor 2.0.6 Ransomware
The new version of the Kraken Cryptor appears to communicate over the Internet and the TOR Network with its C2 (Command and Control) servers and with cybersecurity forums. It was reported that the Kraken Cryptor 2.0.6 Ransomware is deployed through spam emails and exploit kits hosted on unsafe domains. Once the malware managed to enter a computer, it would use shortened URLs to access cybersecurity forum pages during the encryption process. It is suspected that the Kraken Cryptor 2.0.6 Ransomware may incorporate code from legitimate sites to encipher user-generated data uniquely. Computer security researchers managed to extrapolate the number of compromised users based on the number of network requests from unique IP addresses. When this article was written, there were nearly three hundred users who had been infected with the Kraken Cryptor 2.0.6 Ransomware. The Trojan uses the same ransom message we have listed with the Kraken Cryptor 2.0.5 Ransomware above, and the ransom amount appears to be the same. The Ransomware business may be in a decline since crypto-jacking campaigns proved more lucrative in 2018 and late 2017, but cyber threats like the Kraken Cryptor, the Dharma Ransomware, the Crysis Ransomware, and the Everbe 2.0 Ransomware remain active and potent.
SpyHunter Detects & Remove Kraken Ransomware
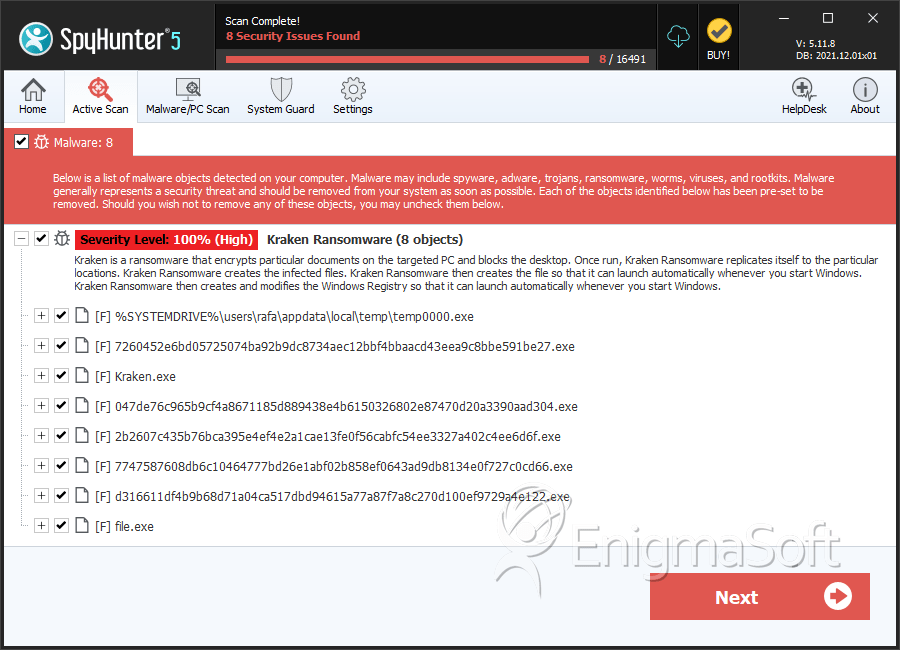
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | kraken.exe | 732eabe16e1e499fb19e75877f7a477e | 35 |
| 2. | temp0000.exe | 1acfdefd7d823688159e6369f5f32ec4 | 1 |
| 3. | 7260452e6bd05725074ba92b9dc8734aec12bbf4bbaacd43eea9c8bbe591be27.exe | 9d07b89cd606bf2379ecc25fd4a4667e | 1 |
| 4. | 047de76c965b9cf4a8671185d889438e4b6150326802e87470d20a3390aad304.exe | 6db9f96b1c56bcb56bc88904683465da | 0 |
| 5. | 2b2607c435b76bca395e4ef4e2a1cae13fe0f56cabfc54ee3327a402c4ee6d6f.exe | ce7606cfdfc05f9d4b336df2c78a46c3 | 0 |
| 6. | 7747587608db6c10464777bd26e1abf02b858ef0643ad9db8134e0f727c0cd66.exe | 02f37c965c175e54796e32de28c15a9a | 0 |
| 7. | d316611df4b9b68d71a04ca517dbd94615a77a87f7a8c270d100ef9729a4e122.exe | 99829d5483ef57c05af928322bd5d6fd | 0 |
| 8. | file.exe | 6224156f14a8d05dbaacbaa1c27acf33 | 0 |
