Kozaka
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 3,903 |
| Threat Level: | 20 % (Normal) |
| Infected Computers: | 2,813 |
| First Seen: | November 5, 2013 |
| Last Seen: | September 4, 2023 |
| OS(es) Affected: | Windows |

Kozaka Image
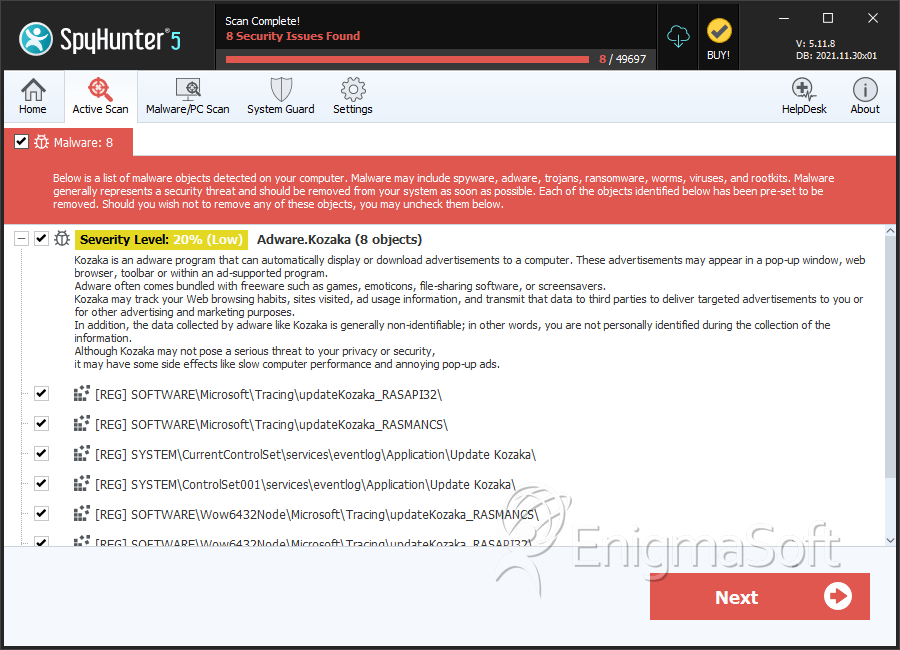
Kozaka is an adware that may display pop-up adverts, discounts, sponsored links and coupons via a pop-up box on shopping related and social networking websites that are visited by computer users. The pop-up adverts of Kozaka may be displayed as boxes, which include a variety of coupons that are available or as underlined keywords, which when clicked, may cover a screen of a PC with a pop-up advert that declares to be sent to the PC user by Kozaka. Kozaka may rapidly expand itself on the computer system. When installed on the PC, Kozaka may compromise the computer user's activities on the machine. Kozaka may embed an add-on, extension or plug-in in Mozilla Firefox, Internet Explorer and Google Chrome when PC users install free software products that might had packaged into their installation Kozaka. When web users install any free software products, they may also install Kozaka. Whenever the PC user will visit shopping related or social networking websites, Kozaka may display a 'See Similar' button on the images of the product, which when clicked may display pop-up advertisements by Kozaka. Kozaka may also display advertising banners on the websites visited by computer users, and as they browse the Internet, Kozaka may display offers, discounts, coupons and deals available on various websites.
Table of Contents
Aliases
8 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| AntiVir | TR/Trash.Gen |
| Symantec | Bloodhound.MalPE |
| AVG | Skodna.Generic.ARC |
| Antiy-AVL | AdWare/Win32.WebCake.gen |
| DrWeb | Adware.Plugin.124 |
| Comodo | Application.Win32.Altbrowse.AK |
| Kaspersky | not-a-virus:AdWare.Win32.Agent.ahbx |
| McAfee | Artemis!171DA209E2AF |
SpyHunter Detects & Remove Kozaka
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Kozakauninstall.exe | 40125ef9cf8ec1f30070b83d140415ef | 9 |
| 2. | updateKozaka.exe | d281b527c93e0a5fe9e1120bbdee6635 | 7 |
| 3. | updateKozaka.exe | 8418e055454cb319377d14fb4af06b55 | 3 |
| 4. | Kozakabho.dll | ed6e31ba6f2c9d8f771b6f35545d83dc | 3 |
| 5. | utilKozaka.exe | 5b0b343f92edece633f144c1f22c8cc5 | 2 |
| 6. | updateKozaka.exe | 6aeca52eb470f364b832f56222ccc23e | 1 |
| 7. | updateKozaka.exe | 230dfb5a23cd995d06a2ecf1e7236a66 | 1 |
| 8. | utilKozaka.exe | 688b342462ca0d4785c0e12fbdfdd3c4 | 1 |
| 9. | updateKozaka.exe | 5273ce694db25ad2b9b6d16fdfbd46d9 | 1 |
Registry Details
Directories
Kozaka may create the following directory or directories:
| %PROGRAMFILES%\Kozaka |
| %PROGRAMFILES(x86)%\Kozaka |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.