Kirk Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | March 17, 2017 |
| Last Seen: | April 11, 2022 |
| OS(es) Affected: | Windows |
The Kirk Ransomware is a ransomware Trojan that is themed around Star Trek. PC security researchers first received reports of the Kirk Ransomware attack on March 16, 2017. The Kirk Ransomware is being spread to computers that execute the Windows operating system through the use of spam email messages. These emails contain corrupted text attachments that include corrupted macro scripts that allow the installation of the Kirk Ransomware on the victim's computer. In its data, the Kirk Ransomware includes the 'Spock Decryptor,' which allows the Kirk Ransomware to carry out its attack without needing the victim to be connected to the Internet. The Kirk Ransomware uses a combination of the AES and RSA encryptions to ensure that the victim's files are fully encrypted and not recoverable without access to the decryption key.
Table of Contents
The Similarities of the Kirk Ransomware and the Karma Ransomware
The Kirk Ransomware shares numerous things in common with the Karma Ransomware, although it is clear that the Kirk Ransomware is a standalone infection and does not seem to belong to any specific ransomware family. The Kirk Ransomware encrypts more than 900 different files types during its attack. The files encrypted by the Kirk Ransomware will be identified by the extension '.kirked,' which is added to the end of each affected file's name. The files that have been encrypted by the Kirk Ransomware become inaccessible completely until the victim pays a ransom in exchange for the decryption key. Malware analysts strongly advise against paying this ransom.
How the Kirk Ransomware Ransom Process Works
The Kirk Ransomware is written in Python and demands payment using the Monero digital currency, unlike most ransomware Trojans that demand payment using BitCoins. The Kirk Ransomware's ransom note is delivered in a text note named 'RANSOM_NOTE.txt' that is dropped on the infected computer's Desktop. Currently, the Kirk Ransomware demands the payment of 50 Monero, which is near $1200 USD at the current exchange rate. The Kirk Ransomware's ransom note is quite long and contains several pictures created using ASCII characters. Below is a fragment of the Kirk Ransomware's ransom note:
'Oh no! The Kirk Ransomware has encrypted your files!
-----------------------------------------------------------------------------------------------------
> ! IMPORTANT ! READ CAREFULLY:
Your computer has fallen victim to the Kirk malware and important files have been encrypted - locked
up so they don't work. This may have broken some software, including games, office suites etc.
Here's a list of some the file extensions that were targetted:
.3g2 .rar .jar .cgi .class .jtd .potx .xex .dds
.3gp .jpg .csv .pl .cd .jtt .potm .tiger .ff
.asf .jpeg .psd .com .java .hwp .sda .lbf .yrp
.asx .png .wav .wsf .swift .602 .sdd .cab .pck
.avi .tiff .ogg .bmp .vb .pdb .sdp .rx3 .t3
.flv .zip .wma .bmp .ods .psw .cgm .epk .ltx
.ai .7z .aif .gif .xlr .xlw .wotreplay.vol .uasset
.m2ts .dif.z .mpa .tif .xls .xlt .rofl .asset .bikey
.mkv .exe .wpl .tiff .xlsx .xlsm .pak .forge .patch
.mov .tar.gz .arj .htm .dot .xltx .big .lng .upk
.mp4 .tar .deb .js .docm .xltm .bik .sii .uax
.mpg .mp3 .pkg .jsp .dotx .xlsb .xtbl .litemod .mdl
.mpeg .sh .db .php .dotm .wk1 .unity3d .vef .lvl
mpeg4 .c .dbf .xhtml .wpd .wks .capx .dat .qst
.rm .cpp .sav .cfm .wps .123 .ttarch .papa .ddv
.swf .h .xml .rss .rtf .sdc .iwi .psark .pta
.vob .mov .html .key .sdw .slk .rgss3a .ydk
.wmv .gif .aiml .odp .sgl .pxl .gblorb .mpq
.doc .txt .apk .pps .vor .wb2 .xwm .wtf
.docx .py .bat .ppt .uot .pot .j2e .bsa
.pdf .pyc .bin .pptx .uof .pptm .mpk .re4
There are an additional 441 file extensions that are targetted. They are mostly to do with games.
To get your files back, you need to pay. Now. Payments recieved more than 48 hours after the time of
infection will be charged double. Further time penalties are listed below. The time of infection has
been logged.
Any files with the extensions listed above will now have the extra extension '.kirked', these files
are encrypted using military grade encryption.
In the place you ran this program from, you should find a note (named RANSOM_NOTE.txt) similar to this one.
You will also find a file named 'pwd' - this is your encrypted password file. Although it was
generated by your computer, you have no way of ever decrypting it. This is due to the security
of both the way it was generated and the way it was encrypted. Your files were encrypted using
this password.'
Dealing with the Kirk Ransomware
The best way to deal with the Kirk Ransomware is to have backup copies of all files. This is the best protection against ransomware since it removes the con artists' power to demand ransom payments from the victim. Apart from having file backups, PC security researchers strongly recommend the use of a reliable security program that is fully up-to-date.
SpyHunter Detects & Remove Kirk Ransomware
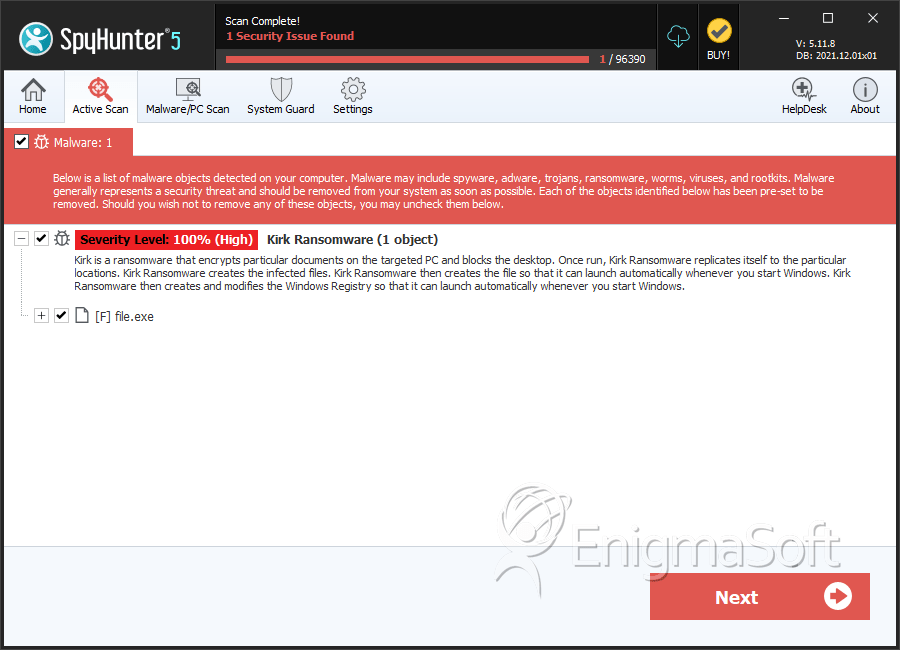
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 78117f7acc8b385e9b29fe711436d16d | 2 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.