'ihurricane@sigaint.org' Ransomware
The 'ihurricane@sigaint.org' Ransomware is a ransomware Trojan that is used to take money from computer users. The 'ihurricane@sigaint.org' Ransomware is a variant of the Stampado Ransomware. The 'ihurricane@sigaint.org' Ransomware was released on the Dark Web for con artists to purchase. Variants of the 'ihurricane@sigaint.org' Ransomware are on sale for $39 USD on the Dark Web currently. Con artists can take advantage of this Ransomware as a Service (RaaS) offer to buy a ready made ransomware Trojan and then carry out attacks on the targets of their choice. The 'ihurricane@sigaint.org' Ransomware is being distributed using corrupted spam email attachments, which use corrupted files that exploit known vulnerabilities on victims' computers.
The 'ihurricane@sigaint.org' Ransomware Uses a Unusual Distribution Method
The 'ihurricane@sigaint.org' Ransomware was observed on an obscure Web page that had poor security measures. The 'ihurricane@sigaint.org' Ransomware was being distributed on jmhare.com, a website that was most probably compromised by the operators of this ransomware Trojan. Malware analysts extracted a sample of the 'ihurricane@sigaint.org' Ransomware, as well as a dropper, which is used to deliver the 'ihurricane@sigaint.org' Ransomware to the victim's computer. An unusual distribution technique is associated with the 'ihurricane@sigaint.org' Ransomware. Computer users are prompted to download a file that is supposed to be an anti-virus program. The file, named 'AVG_5Years_Antivirus_Activated_2017,' is supposedly a pirated version of a known anti-virus program. The file is a real installer for an anti-virus program. However, the 'ihurricane@sigaint.org' Ransomware's dropper is embedded into this installer. When the installer runs, the 'ihurricane@sigaint.org' Ransomware dropper connects to a remote server and downloads and installs the 'ihurricane@sigaint.org' Ransomware's executable.
How the 'ihurricane@sigaint.org' Ransomware Infects a Computer
It is not unusual to deliver threats in the form of anti-virus software and, in fact, there are whole categories of threats that pose as security software. In the case of the 'ihurricane@sigaint.org' Ransomware, it is likely that the con artists have taken advantage of an already available anti-virus installer and used it to deliver the 'ihurricane@sigaint.org' Ransomware. The 'ihurricane@sigaint.org' Ransomware infection itself is a standard encryption Trojan. Like most other ransomware Trojans of this type, the 'ihurricane@sigaint.org' Ransomware uses a combination of the AES and RSA encryption to make the victim's files inaccessible. The 'ihurricane@sigaint.org' Ransomware targets common file types, which include media, image, document and database files. Files that have been encrypted by the 'ihurricane@sigaint.org' Ransomware become no longer accessible. One way in which the 'ihurricane@sigaint.org' Ransomware is different from many other ransomware Trojans is that the 'ihurricane@sigaint.org' Ransomware does not change the affected files' extensions. However, the files that are encrypted will show up in the Windows Explorer as a blank icon. Once the 'ihurricane@sigaint.org' Ransomware finishes encrypting the victim's files, the 'ihurricane@sigaint.org' Ransomware displays a pop-up window containing the 'ihurricane@sigaint.org' Ransomware's ransom note. The note is short, asking the victim to contact the 'ihurricane@sigaint.org' email.
Dealing with the Threat of an 'ihurricane@sigaint.org' Ransomware Attack
The 'ihurricane@sigaint.org' Ransomware demands the payment of a ransom using BitCoins, an online currency that allows con artists to receive payments anonymously. Although the exact amount that the 'ihurricane@sigaint.org' Ransomware demands from victims is not known, it is likely that it is in the same range as most other variants of this threat, between 0.5 and 2 BitCoins (between $400 USD and $1600 USD). Computer users should avoid paying the 'ihurricane@sigaint.org' Ransomware ransom. In many cases, con artists will ignore the victims of the attack or may ask for even more money. Most importantly, a decryptor for the 'ihurricane@sigaint.org' Ransomware may not even be available, as is the case with other variants of this threat. Instead, computer users should take steps to backup their files regularly, either on the cloud or external memory devices. Having backups of all files can help computer users become invulnerable from attacks like the 'ihurricane@sigaint.org' Ransomware completely If victims have backups of the files, then the con artists no longer have the leverage to ask for ransom.
SpyHunter Detects & Remove 'ihurricane@sigaint.org' Ransomware
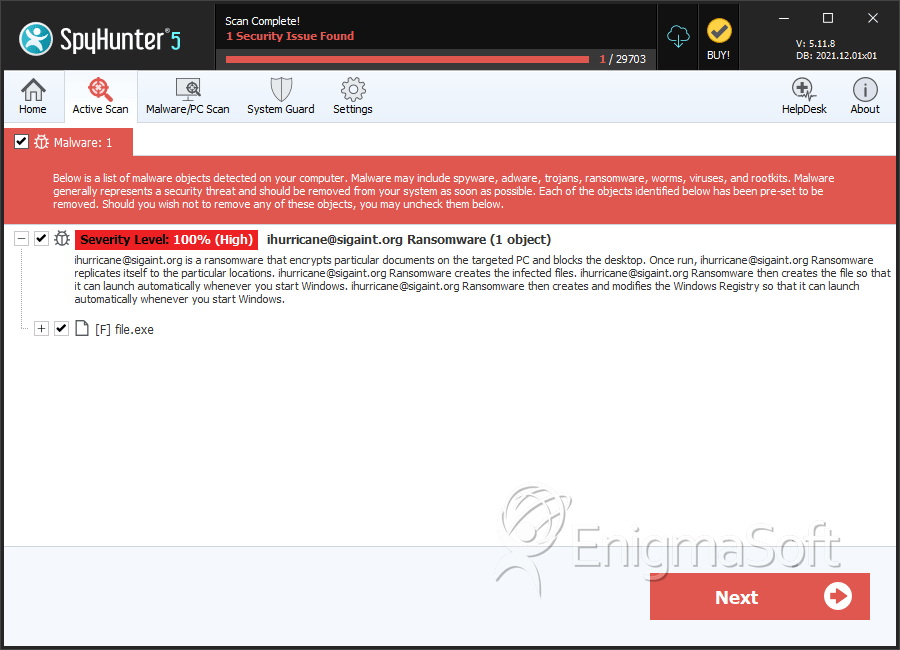
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | a7902b621da3e735c9089139e208f412 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.