IEncrypt Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 2 |
| First Seen: | November 26, 2018 |
| OS(es) Affected: | Windows |
The IEncrypt Ransomware Trojan is a file cryptor program that threat actors pushed to PC users via spam emails and corrupted Microsoft Word documents. The IEncrypt Ransomware was uncovered by researchers in December 2018, but the are samples from September 2018 that suggest an earlier development. The version discussed here is the one from December that is recorded to add the '.cmsnwned' extension to the encrypted files. The IEncrypt Ransomware behaves very similarly to the '.kraussmfz File Extension' Ransomware and the affected users are unable to open data with the following extensions:
.3gp, .avi, .bmp, .cdr, .csv, .dat, .db, .djvu, .docm, .doc, .epub, .docx, .flv, .gif, .iso .ibooks, .jpeg, .jpg, .mdb .md2, .mdf, .mkv, .mov, .mp3, .mp4, .mpg .mpeg, .png, .ppt .pptx, .ppsx, .psd, .rar, .rtf, .sav, .tiff, .tif, .torrent, .txt, .vsd, .wmv, .xls, .xlsx, .xps, .xml, .mrg, .dcx, .db3, .sql, .sqlite3, .sqlite, .sqlitedb, .psp, .pdb, .casb, .ccp, .cr2.
The IEncrypt Ransomware is programmed to delete the Shadow Volume snapshots created by Windows and run commands through cmd.exe to delete the System Restore points you may have created recently. You can recognize the affected data easily since the files receive the '.cmsnwned' extension. For example, 'Glacier Bay National Park and Preserve.pptx' is renamed to 'Glacier Bay National Park and Preserve.pptx.cmsnwned' and a ransom note is dropped to the desktop. The file cryptor at hand is reported to drop a file called 'cmsnwned_readme.txt' and offer the following message:
'Your network was hacked and encrypted.
No free decryption is available on the web.
Email us at mary.weston@protonmail.com (or) beryl.mclennan@tutanota.de to get the ransom amount.
Please, use your company name as the email subject.
TAIL:[random characters]
KEY:[random characters]'
You should note that there are many other versions of the IEncrypt Ransomware deployed to computers. AV companies are working together to limit the distribution of the IEncrypt Ransomware and eliminate associated files. One of the first versions of the IEncrypt Ransomware recommends the users to contact the 'mary.weston@protonmail.com' and 'beryl.mclennan@tutanota.de' email accounts. Versions that have been released later are reported to promote the following email accounts:
florri.nord@protonmail.ch, linda.hartley@tutanota.com, henry.prowse@tutanota.com, imran.adil@tutanota.com, jakie.nunes@tutanota.com, mary.swann@protonmail.com, sarah.barrick@protonmail.com, shirley.rourke@protonmail.com.
In late March, iEncrypt was used in an orchestrated attack against Arizona Beverages USA - one of the biggest American beverage suppliers. The company suffered a major blow to its infrastructure and digital order processing was out of order for days, resulting in millions of dollars in losses. The company had to resort to calling in external security experts to help flush the ransomware from its systems and rebuild the network virtually from scratch. Arizona Beverages was running its servers on outdated versions of Windows that were lacking years' worth of patches and security updates, which no doubt aided the attack.
There is currently no tool that can decrypt files scrambled by iEncrypt. It is never a good idea to pay ransom to the cybercriminals behind any ransomware so the only method of recovering data from systems hit by iEncrypt remains hard backup on external drives or the cloud.
We recommend that the users avoid paying money to the cybercriminals and run a deep scan with a reputable anti-malware product. Remove the IEncrypt Ransomware and use data backups to return your system to normal. The IEncrypt Ransomware is not likely to damage your Windows installation, but it is possible that newer versions may leave a backdoor opened after your data is encrypted. AV engines flag the related files with the following alerts:
Malware@#a8oorqlmdexa
Ransom.FileLocker
Ransom_ICRYPT.THAABBAH
Trojan ( 0054201a1 )
Trojan.Emotet.Win32.7750
Trojan.Encoder.26780
Trojan.Generic.D1DE93B0
Trojan.GenericKD.31364016
Trojan.Win32.Emotet.fknyjx
Trojan/Win32.Fuerboos.R245827
W32/Injector.EBUV!tr
SpyHunter Detects & Remove IEncrypt Ransomware
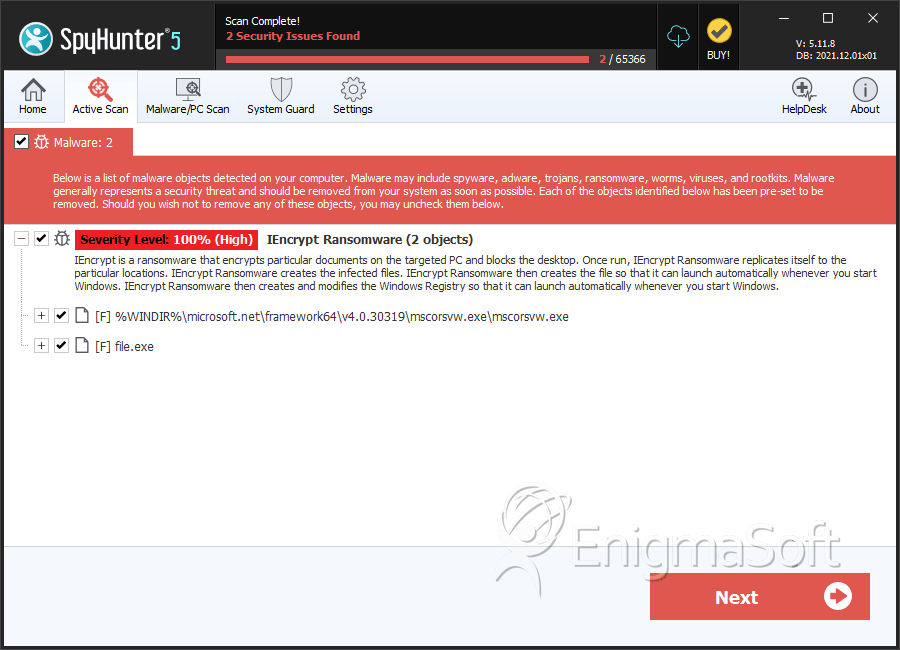
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | mscorsvw.exe | 02ade94c4b5bd3295d775a6d48a968c2 | 1 |
| 2. | file.exe | ba167e9c0645c0304af9c779b1f4e322 | 1 |

