Holycrypt Ransomware
The HolyCrypt Ransomware is a ransomware Trojan that made its appearance in the Summer of 2016. The HolyCrypt Ransomware can be identified easily because it adds the prefix '(encrypted)' to each file it encrypts and uses the email address HolyCrypt@aol.com in its ransom note. The HolyCrypt Ransomware's ransom note allows the victim to send three files to the email address mentioned above to prove that it can decrypt the victim's files. Apart from delivering its ransom note, the HolyCrypt Ransomware changes the affected computer's Desktop wallpaper image and includes an image of a skull wearing a bandana in its message. If the HolyCrypt Ransomware has impacted your machine, PC security analysts strongly advise against paying the ransom. Instead, computer users should restore their files from a backup location and remove the HolyCrypt Ransomware with the help of a reliable, fully updated anti-malware application completely.
Table of Contents
General Characteristics of the HolyCrypt Ransomware Trojan
Like most ransomware Trojans, the HolyCrypt Ransomware is designed to encrypt the victim's files, making them unusable. The HolyCrypt Ransomware's developers have the decryption key, essentially taking the victim's files hostage. The HolyCrypt Ransomware drops its ransom note in the form of an image file named 'alert.jpg' on the victim's computer. This ransom message is characterized by the large image of a skull at the top of the message. The most predictable distribution method associated with the HolyCrypt Ransomware is the use of spam email messages with corrupted embedded URLs or files.
The HolyCrypt Ransomware Attack
The HolyCrypt Ransomware has been linked to a variety of spam email campaigns. The HolyCrypt Ransomware may arrive in this email and be installed on the victim's computer as soon as a corrupted attachment is opened, or the victim clicks on an embedded link. The HolyCrypt Ransomware will drop its payload in one of the following Windows folders:
%User’s Profile%
%Local%
%Temp%
%AppData%
%SystemDrive%
%SystemRoot%
%LocalAppData%
%ProgramData%
%WinDir%
The HolyCrypt Ransomware makes changes to the Windows Registry that allows the HolyCrypt Ransomware to run when Windows starts up automatically. The following Registry modifications would allow the HolyCrypt Ransomware to carry out its attack in the background:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
The HolyCrypt Ransomware targets a wide variety of files with its encryption algorithm, adding the string '(encrypted)' to the beginning of each file name. The full text of the HolyCrypt Ransomware's ransom note reads as follows:
'YOUR COMPUTER HAS BEEN LOCKED!
Your documents, photos, databases and other important files have been locked with strongest encryption and unique key, generated for this computer. Private decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay and obtain the private key.
The server will eliminate the key after 24h.'
The HolyCrypt Ransomware seems to be written in Python, and may be a variety of a ransomware encryptor that is being distributed on a GitHub named Holy-Crypt currently. It is possible that this open source code was modified by the HolyCrypt Ransomware's creators to make this ransomware Trojan.
Dealing with the HolyCrypt Ransomware
Computer users should stay away from paying the HolyCrypt Ransomware's ransom since this enables con artists to continue carrying out these kinds of attacks. Note that con artists may go back on their word to provide the decryption key, ignoring the victim after the ransom is paid. The best way to deal with the HolyCrypt Ransomware and other encryption ransomware variants is to use a reliable anti-malware program to remove the HolyCrypt Ransomware and then restore the affected files from a backup location. Wiping the affected hard drive clean and restoring it from a backup is an effective and more drastic solution. Unfortunately, the files encrypted by the HolyCrypt Ransomware are rarely recoverable, although some file recovery programs and decryptors can sometimes be effective against these encryption ransomware threats (with new ones being released by PC security analysts every day).
SpyHunter Detects & Remove Holycrypt Ransomware
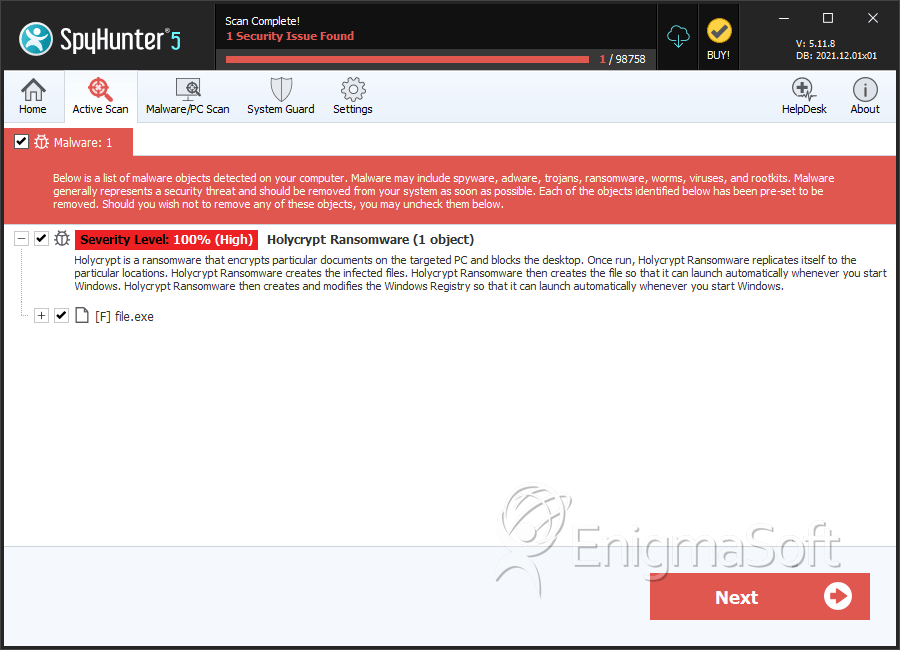
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 4313fd0a3d2cbedd4570230931833fe1 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.