Hermes Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 38 |
| First Seen: | February 15, 2017 |
| Last Seen: | June 17, 2020 |
| OS(es) Affected: | Windows |
The Hermes Ransomware was first observed in the wild on February 13, 2017. The Hermes Ransomware is a ransomware Trojan that identifies the files encrypted during its attack with the file extension '.HERMES.' The Hermes Ransomware carries out a typical ransomware attack, which involves encrypting the victims' files to demand the payment of a ransom. If your computer has been infected with the Hermes Ransomware, malware researchers recommend the use of a reliable security program and then the restoration of the affected files using backup copies. Unfortunately, the encryption algorithms used by the Hermes Ransomware (AES 256 and RSA 1024) mean that once the Hermes Ransomware has encrypted a file, it will no longer be recoverable without access to the decryption key.
Table of Contents
How the Hermes Ransomwaremay be Installed on a Computer
The Hermes Ransomware is installed on victims' computers after they open an unsolicited email attachment. In most cases, the documents used to distribute the Hermes Ransomware exploit vulnerabilities in macros, running corrupted code on the victim's computer as soon as the document is opened. One way to prevent this from happening, apart from being cautious when handling unsolicited email attachments, is to disable the macro functionality in a common word processor software so that these corrupted macros will not run automatically. The Hermes Ransomware is capable of carrying out attacks on various versions of the Windows operating system, including both 64-bit and 32-bit versions of Windows 7, 8 and 10. The Hermes Ransomware will encrypt files on all local drives, as well as on external memory devices connected to the infected computer, also targeting directories that are shared on a network. The Hermes Ransomware will target various file types, including the following:
.3GP, .7Z, .APK, .AVI, .BMP, .CDR, .CER, .CHM, .CONF, .CSS, .CSV, .DAT, .DB, .DBF, .DJVU, .DBX, .DOCM, ,DOC, .EPUB, .DOCX .FB2, .FLV, .GIF, .GZ, .ISO .IBOOKS,.JPEG, .JPG, .KEY, .MDB .MD2, .MDF, .MHT, .MOBI .MHTM, .MKV, .MOV, .MP3, .MP4, .MPG .MPEG, .PICT, .PDF, .PPS, .PKG, .PNG, .PPT .PPTX, .PPSX, .PSD, .RAR, .RTF, .SCR, .SWF, .SAV, .TIFF, .TIF, .TBL, .TORRENT, .TXT, .VSD, .WMV, .XLS, .XLSX, .XPS, .XML, .CKP, .ZIP, .JAVA, .PY, .ASM, .C, .CPP, .CS, .JS, .PHP, .DACPAC, .RBW, .RB, .MRG, .DCX, .DB3, .SQL, .SQLITE3, .SQLITE, .SQLITEDB, .PSD, .PSP, .PDB, .DXF, .DWG, .DRW, .CASB, .CCP, .CAL, .CMX, .CR2.
The encrypted files will have the '.HERMES' extension added to the end of the file name. The Hermes Ransomware will drop an HTML file named 'DECRYPT_INFORMATION.html,' which opens in the victim's Web browser and displays the following ransom note:
'Hermes Ransomware
All your important files are encrypted
Your files has been encrypted using RSA2048 algorithm with unique public-key stored on your PC. There is only one way to get your files back: contact with us, pay, and get decryptor software.
You have "UNIQUEID_DO_NOT_REMOVE" file on your desktop also it duplicated in some folders, its your unique idkey, attach it to letter when contact with us. Also you can decrypt 3 files for test. We accept Bitcoin, you can find exchangers on [LINK TO BITCOIN.COM] and others. Contact information:
primary email: BM-2cXfK4B5IA/9nvci7dYxUhuHYZSmJZ9zibwH©bitmessage.ch
reserve email: x2486@india.com'
PC security analysts strongly advise computer users to disregard the Hermes Ransomware message.
Dealing with the Hermes Ransomware
Malware analysts advise computer users to avoid contacting the people at the email address mentioned in the ransom note or paying the Hermes Ransomware's ransom. In many cases, the people responsible for the Hermes Ransomware and similar attacks will not deliver on their promise to provide the decryption key and, even if they do, paying the Hermes Ransomware ransom allows them to continue carrying out attacks on innocent computer users. Preventive measures are the best way to deal with the Hermes Ransomware. Simply having regular backups of all files makes computer users invulnerable to attacks like the Hermes Ransomware. If the possibility to recover all the files from a backup exists, then the extortionists lose any leverage to demand the payment of a ransom from the victim of a Hermes Ransomware attack.
SpyHunter Detects & Remove Hermes Ransomware
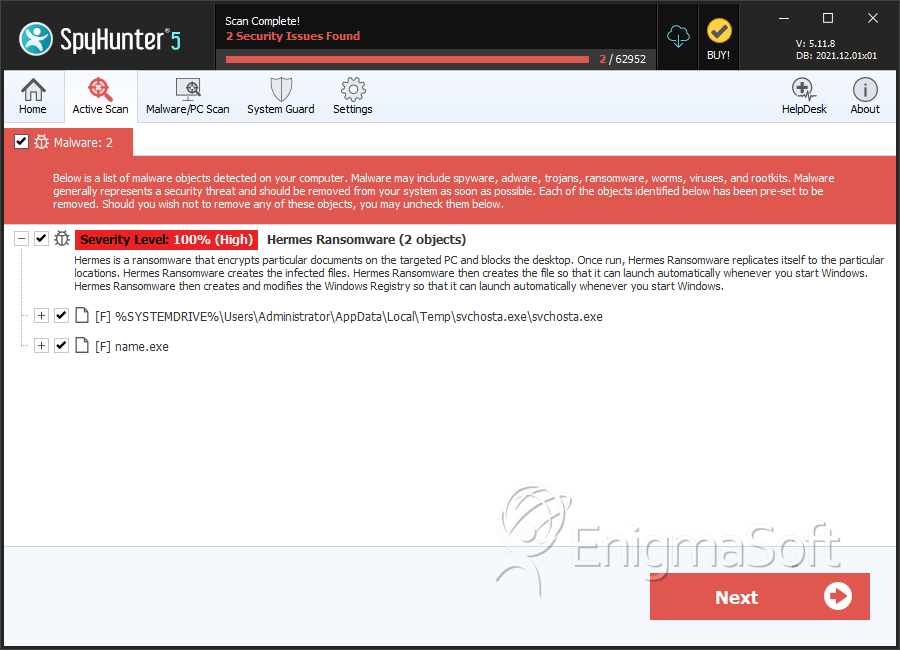
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | svchosta.exe | af93204bc5fa9b99c9b9b9012be9bb1b | 8 |
| 2. | name.exe | 6bbff3614efa6329bb43b2b0a6be8b9c | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.