GozNym
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 50 % (Medium) |
| Infected Computers: | 3 |
| First Seen: | April 15, 2016 |
| Last Seen: | February 14, 2019 |
| OS(es) Affected: | Windows |
 GozNym is a Trojan infection that combines two very destructive threats: Gozi ISFB and Nymaim. Respectively, GozNym's name consists of the names of these two threats. GozNym has become a serious threat to computer security. By taking the best capabilities of the two threats on which it is based, GozNym creates a new threat that is particularly sophisticated and difficult to deal with. The latest news around the malware show that it has been operated by a well-organized group of cyber crooks whose main targets have been banks, credit unions, and popular e-commerce platforms all over the world. True to its nature, within just a few weeks after its first appearance in April 2016, GozNym managed to misappropriate millions of dollars from financial institutions in the USA, Germany, and Canada. At that time, GozNym was linked to another malware operation known as Avalanche which provided hosting to several large malware families, including GozNym, but got largely dismantled the same year.
GozNym is a Trojan infection that combines two very destructive threats: Gozi ISFB and Nymaim. Respectively, GozNym's name consists of the names of these two threats. GozNym has become a serious threat to computer security. By taking the best capabilities of the two threats on which it is based, GozNym creates a new threat that is particularly sophisticated and difficult to deal with. The latest news around the malware show that it has been operated by a well-organized group of cyber crooks whose main targets have been banks, credit unions, and popular e-commerce platforms all over the world. True to its nature, within just a few weeks after its first appearance in April 2016, GozNym managed to misappropriate millions of dollars from financial institutions in the USA, Germany, and Canada. At that time, GozNym was linked to another malware operation known as Avalanche which provided hosting to several large malware families, including GozNym, but got largely dismantled the same year.
Table of Contents
The Global GozNym Malware Operation Has Been Taken Down
In May 2019, after a coordinated international investigation with the participation of police authorities of six countries, Europol, and the US Justice Department, the GozNym malware operation has been taken down. Five of the ten members of the hacking crew have been arrested, while the rest have managed to escape and are hiding from justice, supposedly, in Russia. It has been estimated that the GozNym malware has infected 41,000 computers during its existence, and has attempted to extract $100 million from its victims. Yet, it remains unclear how much of that money the crooks actually managed to pull off. Details from the indictment reveal the strictly organized structure of the hacking crew which operated GozNym malware. The crew consisted of freelancer cybercrime experts from Russia and several other countries, each highly specialized in a particular task along the operational chain of the malware - coders, malware developers, "bullet-proof" hosting providers, overseers, "account takeover" managers, people to "cash out" and launder the stolen funds, "money mules", etc. It looks like the members of the crew have been recruited from online forums, and they coordinated their activities over chat.
The Deadly Combination That Ended Up as the GozNym Trojan
Back in 2016, PC security researchers discovered GozNym while observing what appeared to be a hybrid of Gozi ISFB and Nymaim. Apparently, the creators of Nymaim recompiled this threat's source code and included portions of the previously leaked Gozi ISFB in its code to give it new capabilities. Thus, the combination of these two threats has resulted in a threat that has been used to conduct major financial fraud attacks against more than 24 banks in the United States and Canada.
GozNym has the best features of each of its components. The Trojan uses Nymaim's highly effective dropper and infiltration mechanisms; at the same time, it implements Gozi ISFB's capabilities of extracting the victim's money and financial data. Nymaim, known for its persistence and stealth, allows GozNym to enter a computer undetected and run in the background without alerting the victim or the affected computer's security software. From Gozi ISFB, GozNym has taken the ability to defraud computer users through their Web browser. The fusion of the two powerful malware threats has proven to be highly effective in carrying out attacks on unsuspecting computer users.
How Has GozNym Spread in the Wild
GozNym has been spread through corrupted email attachments. Malicious files associated with GozNym may leverage a vulnerability in Microsoft Office that allows the execution of corrupted code when macros are enabled. GozNym uses Nymaim's two-stage Trojan dropper to carry out its attacks, a feature that had already caught PC security researchers' attention. This means that GozNym enters the victim's computer through an exploit kit, then the malware delivers the second stage of its payload on the victim's computer. Essentially, GozNym uses two executable files to carry out its attack. There are traces of a possible hybrid of these two threats; earlier versions of this threat would use Nymaim's dropper to inject Gozi ISFB's financial module in the form of a corrupted DLL file.
Once GozNym has entered the victim's computer, the malware acts as a keylogger. It hijacks the victim’s web browsers and makes them inject phishing fields into online banking websites. When the user then logs into their online banking account, the malware steals the credentials and takes over the account. Furthermore, GozNym inserts a field in the hijacked browser designed to trick the user into entering a second code. This code is then captured and later used to defeat two-factor authentication. GozNym also has an obfuscated code which allows it to evade anti-malware programs.
Once the victim’s credentials are stolen, they are sent to an administration panel where the "account takeover" specialists use them to log into the accounts and try to steal funds through electronic transfers. Next comes the "cash out" step in which other members of the crew receive the stolen funds and take care of the money laundry. Finally, low-level operators, or so-called "money mules," withdraw the money from ATMs. These last members of the GozNym hacking crew have not been convicted.
GozNym used as a botnet and connection to C&C servers
The many actions of GozNym can be traced to it acting as a botnet where it comprises several systems. Among those systems, GozNym may be leveraged in ways to connect through specific IP (Internet Protocol) addresses. Those IPs are from specific countries found by computer security researchers.
Cisco Talos team's GozNym IP connects by country chart
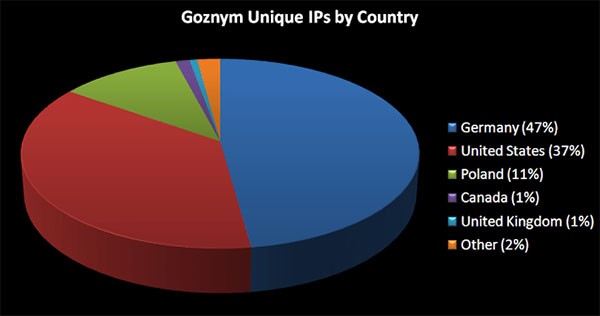
Among the countries where beacons were received to communicate with systems infected with GozNym, Germany ranked at the top with 47% and the United States following behind at 37%. The chart above is a representation of the unique IPs by country found to be utilized for the GozNym threat and servers as identified by experts from the Cisco Talos team who have analyzed the threat and identified is variants.

