GetCrypt Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 21 |
| First Seen: | May 24, 2019 |
| Last Seen: | April 21, 2020 |
| OS(es) Affected: | Windows |
Malware experts have identified a new ransomware threat, which is targeting innocent users. They dubbed it the GetCrypt Ransomware. File-locking Trojans, like the GetCrypt Ransomware, have been very popular among cybercriminals in recent years. They claim their victims by tricking the users into allowing the threat onto their computers. Then the data-encrypting Trojan locks the user's data and demands cash in return for the decryption key. This is a very aggressive and threatening malware type.
The GetCrypt Ransomware is likely being propagated using mass spam email campaigns, bogus application updates and corrupted pirated software. Once the GetCrypt Ransomware lands on your machine, it will perform an extensive scan of your data. When the scan is completed, the GetCrypt Ransomware would have identified and located all the files it was set to encrypt. Logically, the next step is the encryption process itself. The GetCrypt Ransomware would lock your files and add a new extension at the end of the file name. It is interesting that this file-locking Trojan does not have a consistent extension that it adds; instead, the GetCrypt Ransomware applies random 4-character extensions to the affected files. For example, the new extension could be '.OGHF' or '.TRSP,' etc. The next step is dropping the ransom note. The GetCrypt Ransomware's ransom note is named '# DECRYPT MY FILES #.txt.' Using only capital letters accompanied by exclamation marks or other symbols as a ransom note name is a common method used by cybercriminals because it makes the note more visible to the victim. In the note, the creators of the GetCrypt Ransomware inform the users that their data have been locked using a 'strong algorithm.' They also go on to say that it is impossible to recover the encrypted data without using the original key (which the attackers have). Then, the authors of the GetCrypt Ransomware provide an email 'getcrypt@cock.li,' where the user is meant to contact them. In case they do not receive a reply within 48 hours, the attackers ask the victim to send an email to an alternative address – cryptget@tutanota.com.
We recommend you not to follow these instructions. It is not a good idea to pay cybercriminals not only because your cash will go towards their shady future endeavors, but because it is likely that they will not provide you with the decryption key they are promising. A better option is to make sure you install a reputable anti-malware application and have it clean your computer of this nasty bug.
SpyHunter Detects & Remove GetCrypt Ransomware
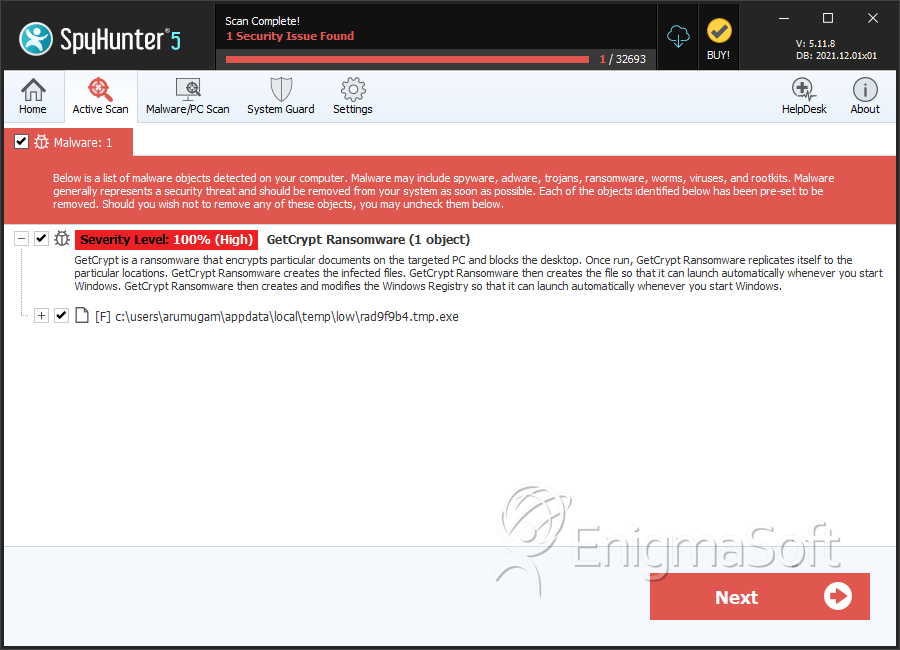
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | rad9f9b4.tmp.exe | 6d21c5c3bcff6076179bccd9ea6d1464 | 9 |

