Epoblockl Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | November 20, 2018 |
| Last Seen: | March 30, 2019 |
| OS(es) Affected: | Windows |
The Epoblockl Ransomware is an encryption ransomware Trojan that is used to take the victims' files hostage and then demand a ransom payment in exchange for the compromised data. The Epoblockl Ransomware is a variant of HiddenTear, an open source ransomware platform that has been available since 2015 and has spawned countless variants. The Epoblockl Ransomware variant appeared in November 2018 specifically.
Table of Contents
Why the Epoblockl Ransomware is Threatening
The Epoblockl Ransomware is typically distributed using corrupted spam email attachments, often in the form of Microsoft Word documents with embedded macro scripts that download and install the Epoblockl Ransomware onto the victim's computer. Once the Epoblockl Ransomware has been installed, it uses the AES and RSA encryptions to make the victim's files inaccessible. The Epoblockl Ransomware targets a wide variety of file types, which may include files with the following file extensions:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The Epoblockl Ransomware marks the victim's files with new file extensions, which may be '.Epoblockl' or '.Crypted,' depending on the specific variant of the Epoblockl Ransomware that has infected the victim's computer. Once the victim's files have been encrypted, the Epoblockl Ransomware delivers a ransom note on the victim's computer's desktop that contains the following text message:
'Your files have been encrypted with AES-128
tommy.sanders@tutanota.com, 0btc.
Please pay immediately'
The Epoblockl Ransomware ransom note typically takes the form of a text file named either 'EPOBLOCKL-NOTE.txt' or 'CRYPTED-NOTE.txt.' PC security researchers have observed a couple of variants of the Epoblockl Ransomware Trojan, both derived from HiddenTear.
Protecting Your Data from Threats Like the Epoblockl Ransomware
The criminals responsible for the Epoblockl Ransomware shouldn't be contacted. Contacting these criminals will expose you to additional infections and will not do anything to help restore any data compromised by the Epoblockl Ransomware attack. Apart from this, it is important to have file backups, either stored on the cloud or an external memory device. Having file backups ensures that computer users can restore their data quickly after an Epoblockl Ransomware infection without having to contact the criminals and risk additional problems. Unfortunately, due to the strength of the encryption method that is used by the Epoblockl Ransomware attack, it is not possible to decrypt the data encrypted by the Epoblockl Ransomware without having the decryption key. Therefore, prevention is the most important measure. Apart from file backups, computer users also should make sure that they have a strong security program that is fully up-to-date and that take steps to handle any spam email or similar unwanted, potentially threatening content safely.
SpyHunter Detects & Remove Epoblockl Ransomware
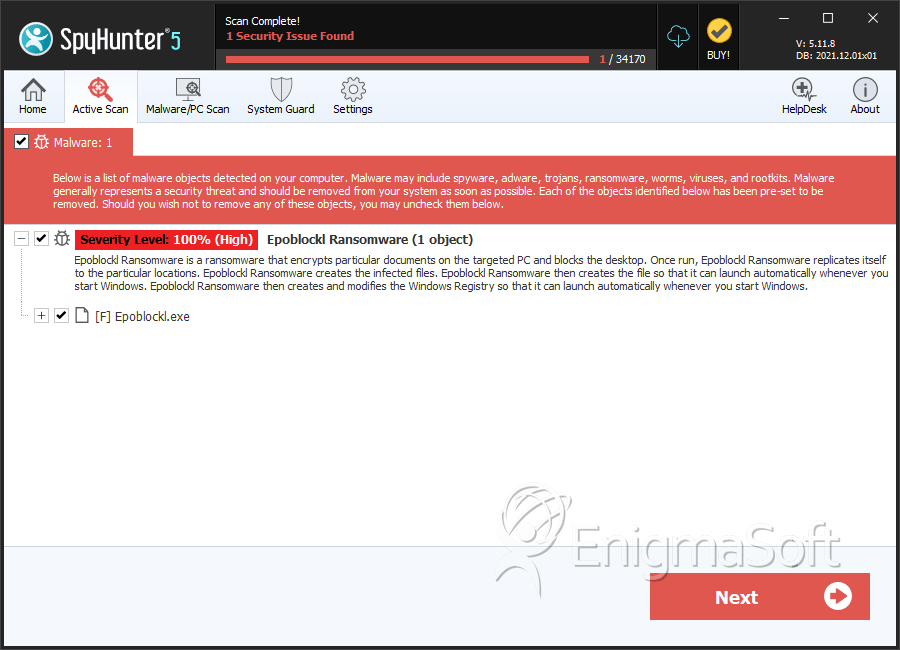
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Epoblockl.exe | e16aa5abbe623ae88b549d80a1c24b91 | 1 |
