DNS Changer
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 10,657 |
| Threat Level: | 90 % (High) |
| Infected Computers: | 2,495 |
| First Seen: | July 24, 2009 |
| Last Seen: | August 11, 2023 |
| OS(es) Affected: | Windows |

DNS Changer Image
DNS Changer is a Trojan that is designed to force a computer system to use rogue DNS servers. Also, DNS Changer is being referred to as the Internet Doomsday Virus, Ghost Click Malware, DNS Changer Rootkit, DNS Changer Malware, DNS Changer Trojan, DNS Changer Virus, FBI DNS Changer or DNSChanger. A DNS Changer infection will typically have two steps, in order to reroute the infected computer’s traffic to these malicious DNS servers:
- A DNS Changer malware infection will change the infected computer system’s settings, in order to replace the DNS servers to rogue DNS servers belonging to hackers or online criminals.
- The DNS Changer malware infection will then try to gain access to other devices on the infected computer’s network (such as a router or a gateway). Using common default passwords for these kinds of devices, the DNS Changer malware infection will attempt to replace the ISP’s DNS servers with its own DNS servers related to criminal activity.
While the first step will only affect a specific computer system, the second step will affect all computers on the infected computer’s network, placing them at risk for additional malware threats. The DNS Changer malware infection has been linked to a variety of malware threats, especially the Zlob Trojan and the TDSS Rootkit.
Table of Contents
DNS Changer or FBI DNS Changer May Shut Down Internet Over 250,000 PCs on Monday, July 9th
Countless thousands of computers are still estimated to be infected by the DNS Changer and will lose all Internet connectivity once these servers are brought down. Although the servers that are responsible for these DNS Changer attacks have been shut down and replaced by benign ones in the famous Operation Ghostclick, these ’safe’ servers are due to be shut off on Monday. Until this shutdown occurs, you may not see any symptoms of a DNS Changer infection, since many of the DNS Changer’s attacks were neutered by the mass server replacement that was set up by legal authorities.
Fortunately, a variety of websites have enacted safeguards for the sake of DNS Changer-infected PCs, with popular search engines and social networking sites displaying warning messages if your computer has been determined to be infected by DNS Changer. ESG malware experts also note the burgeoning presence of websites that have been designed explicitly to check for the DNS Changer on your computer, although you should be careful to distinguish between these websites and sites that distribute fake security software via fraudulent system scanners. Dcwg.org is an example of just one of many reputable sites that are devoted specifically to eradicating the DNS Changer.
While there may not be any symptoms of a DNS Changer infection, ESG malware experts note a high probability for the following issues:
- An overall slowdown of your PC, including slowed web-browsing activities.
- Disabled security programs, particularly concerning anti-virus and anti-malware scanners. You may also see fake pop-ups that fraudulently warn you about these programs being infected. ESG malware researchers also emphasize that this issue does place your PC in exceptional danger of being attacked by other PC threats.
Although various governments, Internet service providers, news companies and Internet safety organizations have all cooperated to try to put an end to DNS Changer infections (which are rapidly declining in number at the time of this article’s writing), authorities still estimate that over two hundred and fifty thousand PCs to be affected by the Internet blackout on Monday, as explained on the video below.
The current date for the server shutdown is 12:01 AM (Eastern Time) July 9th, and if you believe that your computer may be afflicted with the DNS Changer, you should act to disinfect your PC with a suitable anti-malware program before it’s too late. Standard anti-malware protocol, such as booting your PC from removable media, can also help you disable the DNS Changer and other PC threats if you find that your security software is being blocked.
While this Internet blackout has received vast amounts of news attention, ESG malware researchers can also present a ray of hope in this bleak scenario: the DNS Changer’s attacks have not been found to cause permanent harm to computers under normal scenarios. However, you may need to repair your operating system’s DNS settings from the original CD to regain complete Internet access.
Recognizing a DNS Changer Infection on Your Computer or Network
According to ESG security researchers, the best way to make sure that your router or computer system has not become infected with a DNS Changer malware invasion is to enlist the services of a qualified professional. However, you can evaluate whether your computer system is using the correct DNS servers by checking your computer’s DNS server settings. If you suspect that your router’s DNS settings have been changed, it is also important to check your router’s settings. ESG security researchers recommend consulting your router’s or operating system’s owner’s manual for more details on how to check your DNS server settings.
While having your computer be directed to rogue DNS servers is dangerous, DNS Changer is particularly dangerous because of its associated malware threats. Once your computer is infected, all security updates have likely stopped. It is also possible that your anti-malware software is already blocked or disabled. This exponentially increases the likelihood of becoming infected with additional malicious infections. ESG security researchers recommend using a legitimate anti-malware program to remove a DNS Changer infection, as well as possible associated malware threats. It is also important to double-check your online accounts and credit card statements to make sure that your personal information and security have not become compromised.
How to Check for Rogue DNS Servers and DNS Changer Malware Manually on Windows
Below are two options you can use to display detailed information about your IP and identify whether your computer is using rogue DNS.
Windows Option #1: Using the FBI website to check if your computer is affected by DNS Changer
- Go to the Start menu.
- Type in cmd into the Start search box and press Enter.
- Type in ipconfig/all into the Command Prompt and press Enter.
- Locate and copy the IP address next to the DNS servers title and type in those numbers exactly as you see them on the form at: https://forms.fbi.gov/check-to-see-if-your-computer-is-using-rogue-DNS. After the IP address is filled in, the FBI website will identify the DNS address to determine if it is being shut down or not.
Windows Option #2: Running ncpa.cpl to check whether your machine has been infected with DNS Changer Virus
- Run the ncpa.cpl application by typing it into the Run box within the Start menu or typing ncpa.clp into the Start menu's 'search programs or files' box. Press Enter.
- Right-click your Local Area Connection icon and select Properties to enter into the Network Interface Properties page.
- Click once on the Internet Protocol (TCP/IP) item. Click the Properties button.
- Check if the item 'Use the following DNS Server address' is set. Make a note of its status and IP address.
- Compare your IP address with the list of malformed IPs provided by the FBI:
- 85.255.112.0 through 85.255.127.255
- 67.210.0.0 through 67.210.15.255
- 93.188.160.0 through 93.188.167.255
- 77.67.83.0 through 77.67.83.255
- 213.109.64.0 through 213.109.79.255
- 64.28.176.0 through 64.28.191.255
If your IP address falls within the range of any of the listed IPs above, you may be infected with DNS Changer malware and impacted by the FBI's server shut down.
If you are able to obtain a DNS server address automatically, you may switch your DNS to use Google's public DNS for the current time.
Google's free DNS server IPs:
- 8.8.8.8
- 8.8.4.4
Open DNS free server option:
- 208.67.222.222
- 208.67.220.220
How to Check for the DNS Changer Malware Manually on Mac
To check if your IP address falls within the malformed DNS addresses range, perform the following steps on your Mac computer.
- Click the Apple menu.
- Select System Preferences.
- Click Network.
- Find and click your connection (shows as Green).
- Click Advanced.
- Click the DNS tab.
- Copy the IP address in the DNS Severs box and type it into the FBI website: https://forms.fbi.gov/check-to-see-if-your-computer-is-using-rogue-DNS.After the IP address is filled in, the FBI website will find the DNS address to see if it is being shut down or not.
If you are able to obtain a DNS Server address automatically, you may switch your DNS to use Google's public DNS for the current time.
Google's free DNS server IPs:
- 8.8.8.8
- 8.8.4.4
Open DNS free server option:
- 208.67.222.222
- 208.67.220.220
How to Fix DNS Server Settings Manually
You may manually reset your DNS Settings configuration through a DHCP. If you are connected to an Internet Service Provider or corporate network that allows automatic DNS settings, you may follow the steps below to reset your configuration.
Please note: These steps are for advanced PC users. It is not advisable for users who are unfamiliar with the Windows Registry or custom network settings to utilize this procedure.
- Backup your network settings by using the Registry Editor to make a copy under HKEY_LOCAL_MACHINE\SYSTEM\ControlSet\SERVICES\TCPIP
- Run ncpa.cpl from the Start menu's Run or Search box.
- Once Network Connections are brought up, right-click your active network connection. Click Internet Protocol (TCP/IP) once and then click the Properties button.
- Select to radio button where it says 'Obtain DBS Sever Address Automatically'.
- Click OK and then OK again.
How to Prevent DNS Changer Malware
There is no guarantee on preventing DNS Changer malware with any specific method. However, you may follow our recommended prevention tips to help prevent DNS Changer malware in the future.
- Block and monitor network systems attempting to access one of the rogue DNS servers.
- Create custom registry rules to protect specific registry keys. Before changing the keys, make sure you have checked 'Obtain the DNS server address Automatically' in the Internet Protocol (TCP/IP), found in the Properties window. The following registry keys may be edited for an Access Protection Rule to protect them:HKEY_LOCAL_MACHINE\SYSTEM\ControlSet\SERVICES\TCPIP\PARAMETERS\DHCPNAMESERVER = {Value Specified}
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet\SERVICES\TCPIP\PARAMETERS\NAMESERVER = {Value Specified}
- When the 'Use the following DNS Server Addresses' already is checked, use the Registry Editor to access the following registry key:HKEY_LOCAL_MACHINE\SYSTEM\ControlSet\SERVICES\TCPIP
- Check 'HKEY_LOCAL_MACHINE\SYSTEM\ControlSet\SERVICES\TCPIP\Parameters\Interfaces' key to search for your adapters (CLSIDs).
- Then set Access Protection Rules for the keys below:HKEY_LOCAL_MACHINE\SYSTEM\ControlSet\SERVICES\TCPIP\Parameters\Interface\{YOUR CLSID}\DHCPNAMESERVER
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet\SERVICES\TCPIP\Parameters\Interface\{YOUR CLSID}\NAMESERVER
- Do not leave the default username and password on your modems or routers.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Prevx1 | High Risk Cloaked Malware |
| Panda | Trj/CI.A |
| NOD32 | probably a variant of Win32/DNSChanger |
| McAfee-GW-Edition | Rootkit.Rootkit.XCP.6 |
| McAfee | DNSChanger.gen |
| Ikarus | Trojan.Win32.DNSChanger |
| F-Secure | Trojan.Win32.DNSChanger.gtb |
| Comodo | TrojWare.Win32.DNSChanger.gtb |
| BitDefender | Trojan.Generic.792834 |
| AVG | Generic11.GUS |
| Avast | Win32:Rootkit-gen |
| Authentium | W32/Trojan2.EBTM |
| Antiy-AVL | Trojan/Win32.DNSChanger |
| AntiVir | RKIT/Rootkit.XCP.6 |
| a-squared | Trojan.Win32.DNSChanger!IK |
SpyHunter Detects & Remove DNS Changer
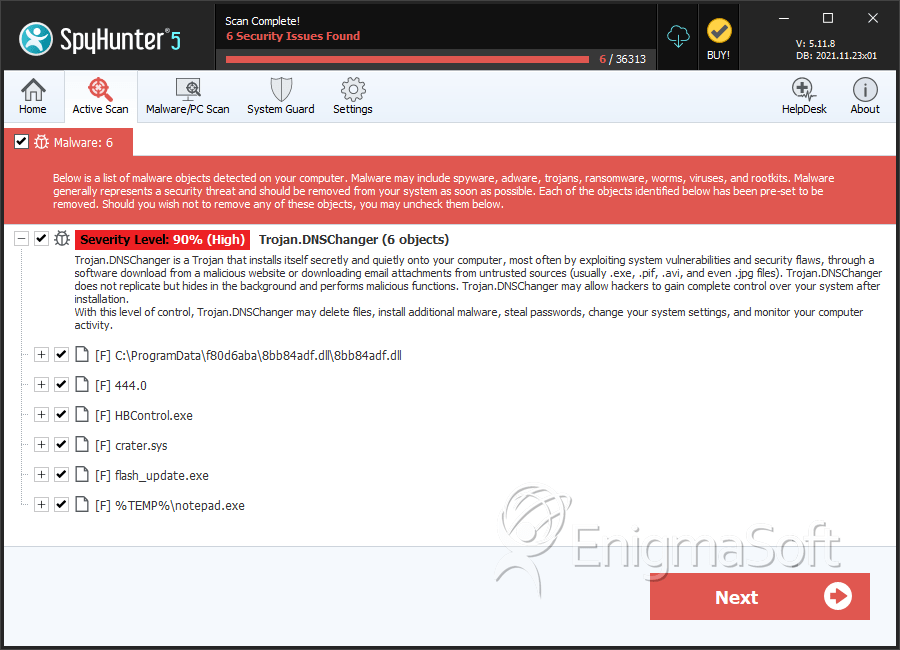
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 8bb84adf.dll | 4575093a4eb00e33121ea8fc5da4417d | 122 |
| 2. | ndisprot.sys | ||
| 3. | MSIVXserv.sys | ||
| 4. | C:\resycled\bootmatrix.com | ||
| 5. | msqpdxserv.sys | ||
| 6. | D:\resycled\ntldr.com | ||
| 7. | G:\resycled\ntldr.com | ||
| 8. | %SYSTEM_DRIVE%\resycled\ntldr.com | ||
| 9. | %SYSTEM%\kdlly.exe | ||
| 10. | %SYSTEM%\kdkgg.exe | ||
| 11. | %SYSTEM%\msmgs.exe | ||
| 12. | %SYSTEM%\cmd32.exe | ||
| 13. | %SYSTEM%\krl32mainweq.dll | ||
| 14. | %PROGRAM_FILES%\videosoft\Uninstall.exe | ||
| 15. | %COMMON_DOCUMENTS%\cmijj.exe | ||
| 16. | %COMMON_DOCUMENTS%\LSSAS.exe | ||
| 17. | %WINDOWS%\vkl_1253053752.exe | ||
| 18. | %WINDOWS%\vkl_1252834085.exe | ||
| 19. | %WINDOWS%\vkl_1253173827.exe | ||
| 20. | %WINDOWS%\vkl_1252481066.exe | ||
| 21. | %WINDOWS%\vkl_1253181421.exe | ||
| 22. | _VOIDd.sys | ||
| 23. | seneka.sys | ||
| 24. | C:\Windows\system32\wdmaud.sys | ||
| 25. | TDSSserv.sys | ||
| 26. | I:\resycled\ntldr.com | ||
| 27. | H:\resycled\ntldr.com | ||
| 28. | M:\resycled\ntldr.com | ||
| 29. | %SYSTEM%\MSlgx.exe | ||
| 30. | %SYSTEM%\lsass.exe | ||
| 31. | %SYSTEM%\kdgzh.exe | ||
| 32. | %SYSTEM%\mssms.exe | ||
| 33. | %SYSTEM%\kduev.exe | ||
| 34. | %SYSTEM%\drivers\ndisprot.sys | ||
| 35. | %COMMON_DOCUMENTS%\mstsc.exe | ||
| 36. | %COMMON_DOCUMENTS%\msert.exe | ||
| 37. | %WINDOWS%\vkl_1252834079.exe | ||
| 38. | %WINDOWS%\vkl_1252765671.exe | ||
| 39. | %WINDOWS%\vkl_1253165426.exe | ||
| 40. | %WINDOWS%\vkl_1252768743.exe | ||
| 41. | %WINDOWS%\vkl_1253181420.exe | ||
| 42. | %WINDOWS%\vkl_1252768769.exe | ||
| 43. | ESQULserv.sys | ||
| 44. | H8SRTd.sys | ||
| 45. | gaopdxserv.sys | ||
| 46. | gxvxcserv.sys | ||
| 47. | UACd.sys | ||
| 48. | F:\resycled\ntldr.com | ||
| 49. | E:\resycled\ntldr.com | ||
| 50. | %SYSTEM%\csrcs.exe | ||
| 51. | %SYSTEM%\cmd64.exe | ||
| 52. | %SYSTEM%\kdqwt.exe | ||
| 53. | %SYSTEM%\msnqp.exe | ||
| 54. | %SYSTEM%\csrns.exe | ||
| 55. | %SYSTEM%\csrss.exe | ||
| 56. | %PROFILE_TEMP%\AlfaBR.exe | ||
| 57. | %COMMON_DOCUMENTS%\csrss.exe | ||
| 58. | %WINDOWS%\vkl_1252511207.exe | ||
| 59. | %WINDOWS%\vkl_1252511321.exe | ||
| 60. | %WINDOWS%\vkl_1253165416.exe | ||
| 61. | %WINDOWS%\vkl_1252968719.exe | ||
| 62. | %WINDOWS%\vkl_1253173833.exe | ||
| 63. | %WINDOWS%\vkl_1252765651.exe | ||
| 64. | D:\resycled | ||
| 65. | B:\resycled | ||
| 66. | C:\resycled | ||
| 67. | P:\resycled | ||
| 68. | T:\resycled | ||
| 69. | Q:\resycled | ||
| 70. | S:\resycled | ||
| 71. | %SYSTEM_DRIVE%\resycled | ||
| 72. | %PROGRAM_FILES%\DigitalHQ | ||
| 73. | %PROGRAM_FILES%\Network Monitor | ||
| 74. | %PROGRAM_FILES%\SiteEntry | ||
| 75. | %PROGRAM_FILES%\DVDConv | ||
| 76. | %PROGRAM_FILES%\AccessMV | ||
| 77. | %PROGRAM_FILES%\DecodingHQ | ||
| 78. | %PROGRAM_FILES%\PlayMe | ||
| 79. | %PROGRAM_FILES%\QuickTiming | ||
| 80. | %PROGRAM_FILES%\FullMovies | ||
| 81. | %PROGRAM_FILES%\PlusCodec | ||
| 82. | %PROGRAM_FILES%\PLDivX | ||
| 83. | %PROGRAM_FILES%\DVDextraPL | ||
| 84. | %PROGRAM_FILES%\freshplay | ||
| 85. | %PROGRAM_FILES%\HDQuality | ||
| 86. | %PROGRAM_FILES%\aquaplay | ||
| 87. | %PROGRAMS%\HDtvcodec | ||
| 88. | %PROGRAMS%\HeroCodec | ||
| 89. | %PROGRAMS%\totalvid | ||
| 90. | %PROGRAMS%\MoviesPlay | ||
| 91. | %PROGRAMS%\UNICCodec | ||
| 92. | %PROGRAMS%\FreeHDplay | ||
| 93. | %PROGRAMS%\QuickyPlaeyr | ||
| 94. | %PROGRAMS%\HDExtrem | ||
| 95. | %PROGRAMS%\DVDTool | ||
| 96. | %PROGRAMS%\PLDivX | ||
| 97. | %PROGRAMS%\DVDextraPL | ||
| 98. | %PROGRAMS%\Mediaview | ||
| 99. | F:\autorun.inf | ||
| 100. | %WINDOWS%\vkl_1250424439 | ||
| 101. | %WINDOWS%\vkl_1250425267 | ||
| 102. | %WINDOWS%\vkl_1251463593 | ||
| 103. | %WINDOWS%\vkl_1250425328 | ||
| 104. | %WINDOWS%\Tasks\MSWD-5d240b12.job | ||
| 105. | %WINDOWS%\Tasks\MSWD-2969d51d.job | ||
| 106. | %WINDOWS%\Tasks\MSWD-6145903c.job | ||
| 107. | %WINDOWS%\Tasks\MSWD-28d8d31d.job | ||
| 108. | %WINDOWS%\Tasks\MSWD-3e4ae7ad.job | ||
| 109. | %WINDOWS%\Tasks\MSWD-1b4abb06.job | ||
| 110. | %WINDOWS%\Tasks\MSWD-b868995b.job | ||
| 111. | %WINDOWS%\Temp\tempo-289.tmp | ||
| 112. | %WINDOWS%\Temp\tempo-B7D.tmp | ||
| 113. | %WINDOWS%\Temp\tempo-97265.tmp | ||
| 114. | %WINDOWS%\Temp\tempo-394365031.tmp | ||
| 115. | M:\resycled | ||
| 116. | I:\resycled | ||
| 117. | G:\resycled | ||
| 118. | E:\resycled | ||
| 119. | W:\resycled | ||
| 120. | R:\resycled | ||
| 121. | J:\resycled | ||
| 122. | O:\resycled | ||
| 123. | %MYPICTURES%\resycled | ||
| 124. | %PROGRAM_FILES%\BestHD | ||
| 125. | %PROGRAM_FILES%\DDnsFilter | ||
| 126. | %PROGRAM_FILES%\HDExtrem | ||
| 127. | %PROGRAM_FILES%\HDtvcodec | ||
| 128. | %PROGRAM_FILES%\UltraVideo | ||
| 129. | %PROGRAM_FILES%\videoplay | ||
| 130. | %PROGRAM_FILES%\Convert2Play | ||
| 131. | %PROGRAM_FILES%\HeroCodec | ||
| 132. | %PROGRAM_FILES%\AlfaBR | ||
| 133. | %PROGRAM_FILES%\EZVideo | ||
| 134. | %PROGRAM_FILES%\SunPorn | ||
| 135. | %PROGRAM_FILES%\ExpressVids | ||
| 136. | %PROGRAM_FILES%\PornoPlayer | ||
| 137. | %PROGRAM_FILES%\Mediaview | ||
| 138. | %PROGRAMS%\SiteEntry | ||
| 139. | %PROGRAMS%\QuickTiming | ||
| 140. | %PROGRAMS%\coolplay | ||
| 141. | %PROGRAMS%\DVDConv | ||
| 142. | %PROGRAMS%\homeview | ||
| 143. | %PROGRAMS%\PlayMe | ||
| 144. | %PROGRAMS%\aquaplay | ||
| 145. | %PROGRAMS%\DivxFree | ||
| 146. | %PROGRAMS%\PlayMYDVD | ||
| 147. | %PROGRAMS%\videoplay | ||
| 148. | %PROGRAMS%\BlueRaTech | ||
| 149. | %PROGRAMS%\BHVideo | ||
| 150. | D:\autorun.inf | ||
| 151. | %SYSTEM_DRIVE%\Users\Manuel | ||
| 152. | %WINDOWS%\vkl_1251803401 | ||
| 153. | %WINDOWS%\vkl_1250425221 | ||
| 154. | %WINDOWS%\vkl_1251745894 | ||
| 155. | %WINDOWS%\Tasks\MSWD-af53409d.job | ||
| 156. | %WINDOWS%\Tasks\MSWD-c61509c8.job | ||
| 157. | %WINDOWS%\Tasks\MSWD-27e0d013.job | ||
| 158. | %WINDOWS%\Tasks\MSWD-95cf3d27.job | ||
| 159. | %WINDOWS%\Tasks\MSWD-56802d43.job | ||
| 160. | %WINDOWS%\Tasks\MSWD-ee6b7301.job | ||
| 161. | %WINDOWS%\Tasks\MSWD-88e4ae02.job | ||
| 162. | %WINDOWS%\Temp\tempo-44B.tmp | ||
| 163. | %WINDOWS%\Temp\tempo-45B.tmp | ||
| 164. | %WINDOWS%\Temp\tempo-76546.tmp | ||
| 165. | %WINDOWS%\Temp\tempo-161797121.tmp | ||
| 166. | %WINDOWS%\Temp\DAB.tmp | ||
| 167. | H:\resycled | ||
| 168. | K:\resycled | ||
| 169. | Z:\resycled | ||
| 170. | F:\resycled | ||
| 171. | L:\resycled | ||
| 172. | X:\resycled | ||
| 173. | N:\resycled | ||
| 174. | V:\resycled | ||
| 175. | %PERSONAL%\resycled | ||
| 176. | %PROGRAM_FILES%\ubervid | ||
| 177. | %PROGRAM_FILES%\FreeHDplay | ||
| 178. | %PROGRAM_FILES%\totalvid | ||
| 179. | %PROGRAM_FILES%\DVDTool | ||
| 180. | %PROGRAM_FILES%\homeview | ||
| 181. | %PROGRAM_FILES%\VideoKey | ||
| 182. | %PROGRAM_FILES%\DigitalLabs | ||
| 183. | %PROGRAM_FILES%\QuickyPlaeyr | ||
| 184. | %PROGRAM_FILES%\MpegBuster | ||
| 185. | %PROGRAM_FILES%\iVideo | ||
| 186. | %PROGRAM_FILES%\TonsOfPorn | ||
| 187. | %PROGRAM_FILES%\BlueRaTech | ||
| 188. | %PROGRAM_FILES%\XXXHoliday | ||
| 189. | %PROGRAM_FILES%\PluginVideo | ||
| 190. | %PROGRAMS%\DigitalHQ | ||
| 191. | %PROGRAMS%\AccessMV | ||
| 192. | %PROGRAMS%\HDQuality | ||
| 193. | %PROGRAMS%\DecodingHQ | ||
| 194. | %PROGRAMS%\UltraVideo | ||
| 195. | %PROGRAMS%\DigitalLabs | ||
| 196. | %PROGRAMS%\FullMovies | ||
| 197. | %PROGRAMS%\Convert2Play | ||
| 198. | %PROGRAMS%\ExpressVids | ||
| 199. | %PROGRAMS%\PluginVideo | ||
| 200. | %PROGRAMS%\sexvid | ||
| 201. | %PROGRAMS%\TonsOfPorn | ||
| 202. | K:\autorun.inf | ||
| 203. | %SYSTEM_DRIVE%\autorun.inf | ||
| 204. | %WINDOWS%\vkl_1250424989 | ||
| 205. | %WINDOWS%\vkl_1250425116 | ||
| 206. | %WINDOWS%\vkl_1251734499 | ||
| 207. | %WINDOWS%\vkl_1250733143 | ||
| 208. | %WINDOWS%\Tasks\MSWD-db3968bf.job | ||
| 209. | %WINDOWS%\Tasks\MSWD-4535c222.job | ||
| 210. | %WINDOWS%\Tasks\MSWD-469d5901.job | ||
| 211. | %WINDOWS%\Tasks\MSWD-b2be9e3f.job | ||
| 212. | %WINDOWS%\Tasks\MSWD-44fcb0c6.job | ||
| 213. | %WINDOWS%\Tasks\MSWD-4354122e.job | ||
| 214. | %WINDOWS%\Temp\tempo-E2B.tmp | ||
| 215. | %WINDOWS%\Temp\tempo-66D.tmp | ||
| 216. | %WINDOWS%\Temp\tempo-1145640.tmp | ||
| 217. | %WINDOWS%\Temp\tempo-161796561.tmp | ||
| 218. | %WINDOWS%\Temp\tempo-394365218.tmp | ||
| 219. | CLADD | b4960ba4f1d5b62e8e1f2ddaeb09199b | 0 |
| 220. | CLADD | 6f6c87b2dba431dbc2f3b63af5a040c7 | 0 |
| 221. | CLADD | e8b3efb412f7dfb5a476e38bc54fe704 | 0 |
| 222. | CLADD | 5df184d2bce3f1a9ab1490c4fc2c7f78 | 0 |
| 223. | CLADD | c76425b68572b801674014c4fd0165dc | 0 |
| 224. | CLADD | a481fa00af99a3d5ae563d4caa18448b | 0 |
| 225. | CLADD | 7d092ed8cf34ed6e6b382a3fcaab1376 | 0 |
| 226. | CLADD | da5a2a83888bef5034a8ee7d008ed337 | 0 |
| 227. | CLADD | bd508f1e5da986d94f5c07fd01724fe1 | 0 |
| 228. | CLADD | e381897df008bdecc66bc9d049cda629 | 0 |
| 229. | CLADD | 53f7acfa5993e48da6449222d91857d9 | 0 |
| 230. | CLADD | 502794cf64c5c49a4e264b5d912b8837 | 0 |
| 231. | CLADD | 8b67a8e98d72b506c26661cd9119f3b6 | 0 |
| 232. | CLADD | 464f1352973317cda3f1b88dfa706f52 | 0 |
| 233. | CLADD | b5bf9a8d699a642e4e0a70b4e728bbc6 | 0 |
| 234. | CLADD | 91d0c05343dfc9fc8a26efc5e788ed08 | 0 |
| 235. | CLADD | 4764cf4b585f3b6d6db0390e8525b680 | 0 |
| 236. | CLADD | 00ed95b196598c41fd99211ee071a239 | 0 |
| 237. | CLADD | d63caa4550a08435913c7bf70b80a719 | 0 |
| 238. | CLADD | 3aada12fae37c81ed52558bf7472210c | 0 |
| 239. | CLADD | 6cfbbcc3cc8f11395ebb1afdbfedbab7 | 0 |
| 240. | CLADD | 710fa7e6083c8a9c136ad09fdc25b499 | 0 |
| 241. | CLADD | 429e73c9da88a78d5f7d05fe870ab20d | 0 |
| 242. | crater.sys | 93db3a3e09ab5dca68e2f2dca92f64c3 | 0 |
| 243. | flash_update.exe | 8e3f18c030049ad18e2889821cff96e2 | 0 |
| 244. | notepad.exe | fdc6f4169bc2fcb4f047511e6002523f | 0 |

