CryptoFortress
CryptoFortress is a ransomware threat the takes over an infected computer and encrypts its files. This has become a common tactic for ransomware developers because the encryption is nearly impossible to break without the decryption key. This means that even if CryptoFortress is removed from the infected computer, the files remain encrypted. This allows third parties to ask for a ransom, threatening computer users by withholding access to the encrypted files. CryptoFortress may spread through corrupted email messages containing threatening file attachments or disguised into embedded links which may lead to attack websites. CryptoFortress also may be spread using fake file downloads, such as bogus updates for Flash player or fake media players. Once CryptoFortress has been successfully delivered to the victim's computer, all files on the infected computer are encrypted.
The people behind CryptoFortress will demand payment of a ransom from the victim in order to decrypt the affected files. Currently, the CryptoFortress demands one Bitcoin in order to decrypt the files. Bitcoin, being anonymous, is especially suited for these types of instances. Bitcoin prices have varied wildly in the last few years. As of the writing of this, one Bitcoin was worth approximately $310 USD. There are many threats that carry out this same attack with small variations to the process. CryptoFortress is very similar to TorrentLocker, another ransomware threat. In fact, CryptoFortress and Torrentlocker use similar Web pages and source code, making it likely that the same people are responsible for both.
Table of Contents
How CryptoFortress Infects a Computer
CryptoFortress searches for supported data files on the victim's computer. CryptoFortress will look for pictures, videos and documents since these tend to have data that is important for the computer user and hard to replace. CryptoFortress then creates a copy of the file and adds the FRTRSS extension (.frtrss added to the end of the file's name). CryptoFortress then encrypts the file before restoring its original name and extension. Victims of CryptoFortress are allowed to decrypt two small files with no charge to demonstrate that the people responsible for CryptoFortress are capable of decrypting the affected files. CryptoFortress demands a ransom from the victim in order to decrypt the rest. Paying CryptoFortress' ransom allows third parties to continue carrying out their attacks. If you have a way to avoid the payment (for example, a backup of your files), it is recommended to avoid paying the fee to restore the files.
CryptoFortress targets files with the following extensions: .unity3d, .blob, .wma, .avi, .rar, .DayZProfile, .doc, .odb, .asset, ,forge, .cas, .map, .mcgame, .rgss3a, .big, .wotreplay, .xxx, .m3u, .png, .jpeg, .txt, .crt, .x3f, .ai, .eps, .pdf, .lvl, .sis, .gdb. Note that many of these files extensions represent game saved files, meaning that CryptoFortress targets computer users engaged in computer games purposefully, halting their progress until they pay CryptoFortress' fee. Currently, there is no way of restoring the encrypted files without a decryption key. Considering this, you should protect yourself from falling prey to these types of attacks by maintaining regular file backups on a separate device or on the cloud.
Protecting Yourself from a CryptoFortress Attack
CryptoFortress spreads using typical threat delivery methods. Some examples of how CryptoFortress may be spread include spam email attachments, attack websites and fake file downloads. Although a reliable security program is essential in halting CryptoFortress attacks, knowing how to stay safe while browsing the Web is just as important. Some things to remember when avoiding threat attacks like CryptoFortress include the following:
- Stay away from suspicious websites. High-risk websites include pornographic websites and file sharing networks.
- Avoid peer-to-peer file sharing and pirated software or other media.
- Never open unknown files or links, even if they come from an email address that appears to be trusted.
SpyHunter Detects & Remove CryptoFortress
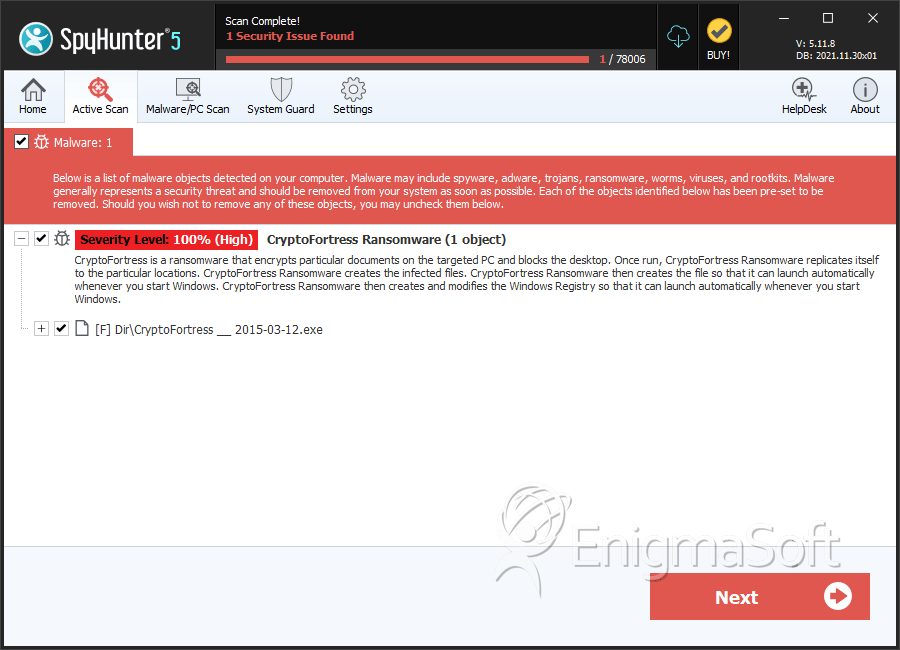
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | CryptoFortress __ 2015-03-12.exe | e6dda3e06fd32fc3670d13098f3e22c9 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.