Chroomium Browser
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 11,082 |
| Threat Level: | 10 % (Normal) |
| Infected Computers: | 5,374 |
| First Seen: | January 8, 2016 |
| Last Seen: | November 3, 2023 |
| OS(es) Affected: | Windows |
Computer users have reported that their default Web browser was changed to the Chroomium Browser automatically. The Chroomium Browser looks and acts like Google Chrome exactly, but once inside a machine, will redirect computer users to a 'Password Manager' website continually, as part of a tactic to obtain their online passwords. It is highly likely that the Chroomium Browser also may have the capacity to monitor the computer users' online activities as well as expose them to unwanted advertisements and deliver threats to their computers.
Although it is currently unknown exactly what purpose the Chroomium Browser has, the patterns it exhibits make it very likely that the Chroomium Browser is used to collect the computer users' online passwords and other data such as credit card numbers or online banking information. As part of its tactic, the Chroomium Browser changes the affected computer's shortcuts on the Task Bar, Desktop, and Start Menu, leading the browser to the Chroomium Browser instead of Google Chrome. However, since the icons and appearance of both Web browsers are identical, computer users may not be aware that they are using the Chroomium Browser instead of Google Chrome. Because of this, make sure that your online passwords have not been compromised and threats have not been installed on the affected computer after removing the Chroomium Browser and restoring Google Chrome as your default Web browser.
Table of Contents
The Chroomium Browser Pretends to be Google Chrome
The Chroomium Browser is a fake version of Google Chrome. The purpose of the Chroomium Browser is to make computer users believe that they are using Google Chrome instead of this fake Web browser. Computer users will be prompted to enter their password information in a fake 'password manager' Web page continually. The Chroomium Browser takes over a computer silently, replacing all instances of Google Chrome with its own shortcuts and links. However, Google Chrome will not be uninstalled; it will simply not launch as the default Web browser when computer users try to load a Web page. PC security analysts have encountered numerous fake versions of the Google Chrome Web browser, which use this tactic that may be associated with bogus 'unzipper' applications supposedly designed to manage ZIP and RAR files, fake PDF managers and similar low-quality apps.
When the Chroomium Browser is installed on a computer, it will pretend that the Chroomium Browser is the Google Chrome Web browser. The tactic is simple: if the computer users think that the Chroomium Browser is Google Chrome, they will not hesitate to enter their credit card number, online banking information, or similar data into the affected Web browser. Other possible uses for the fake versions of the Google Chrome Web browser may include delivering unwanted content to computer users, such as numerous advertisements and affiliate marketing links. Computer users should double check to ensure that their Web browser is effectively still Google Chrome, especially if they are observing odd advertisements and redirects. Google Chrome also should show up in the Task Manager as 'Chrome.exe' (fake versions of Google Chrome, such as the Chroomium Browser, may appear as 'Chroomium.exe' or 'chrbr.exe').
Removing a Chroomium Browser Infection from a PC
The first step in dealing with the Chroomium Browser is to uninstall this fake Web browser completely. Computer users should uninstall this Web browser manually, deleting its files and Registry keys and using the Windows Control Panel to uninstall the software completely. It is also important to remove all shortcuts created by the Chroomium Browser and create new shortcuts that lead to Google Chrome instead. As part of the installation process, computer users should use a reliable anti-malware application that is fully up-to-date to scan the affected computer for possible threats or other infections that may have been acquired as part of the Chroomium Browser installation. To prevent future issues, computer users should be especially on guard for suspicious behavior from their Web browser, particularly if it is prompting them to enter their password in an unusual way.
SpyHunter Detects & Remove Chroomium Browser
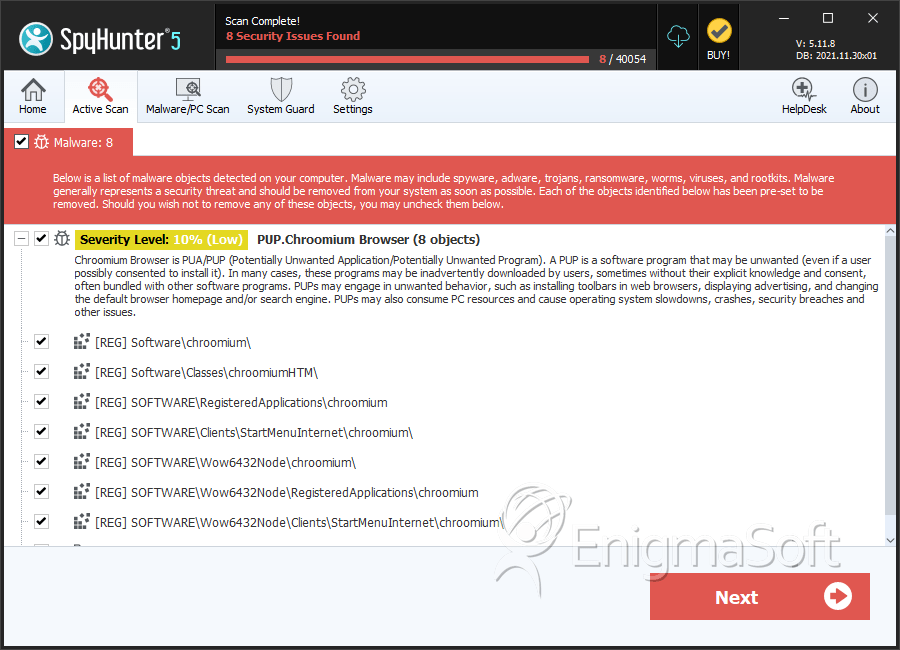
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | browserserver.exe | f1a40d34335be3a0ca9d5308c7f4d5c7 | 1,726 |
| 2. | chrome.exe | 659a112ce076dca7ab73931de57d93e8 | 1,378 |
| 3. | delegate_execute.exe | 9b450fa544844cf492e43e5cff5edee6 | 101 |
| 4. | browserServer.exe171242 | 0fffa9b640f94bc5072a0a4cc3053fe0 | 40 |
| 5. | browserServer.exe511767593.vir | efabe228249f750c06e4004c78c68398 | 32 |
| 6. | browserServer.exe | 4db21890e3881023982b3933c53ac52f | 18 |
| 7. | browserServer.exe | dcfbc6d4aacce09cff568760e9adc88d | 7 |
| 8. | chrome.exe | e4e14363d786a404bdb19b9ccd0ab4ee | 5 |
| 9. | chrome.exe | 48519899e5d106d75e349adaec1d9a4b | 3 |
Registry Details
Directories
Chroomium Browser may create the following directory or directories:
| %PROGRAMFILES%\chroomium Browser |
| %PROGRAMFILES(x86)%\chroomium Browser |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.