Backdoor.Cycbot.G
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 60 % (Medium) |
| Infected Computers: | 6,496 |
| First Seen: | October 14, 2011 |
| Last Seen: | October 5, 2022 |
| OS(es) Affected: | Windows |
In November of 2011, Backdoor.Cycbot.G was involved in a series of online attacks linked to a fraudulent email. Victims of Backdoor.Cycbot.G attack received an email claiming to come from the iTunes store. The subject of the email thanks the victim for their purchase on iTunes and claims that the victim has won a gift. The content of the email indicate that the victim has won a gift certificate with a $50 USD value. However, ESG security researchers strongly recommend not following the instructions in this email. Doing so will invariably result in a dangerous Backdoor.Cycbot.G Trojan infection. This is due to the fact that this dangerous email instructs its victim to open an attached compressed file in order to learn their supposed gift certificate's authorization code. This claim should be more than enough to set off an alarm in any experienced computer user's mind, and rightly so. Once the ZIP file containing Backdoor.Cycbot.G installed on the victim's computer and is decompressed, a cybercriminal can use Backdoor.Cycbot.G to gain control of the victim's computer from a remote location. ESG security researchers strongly recommend avoiding all unsolicited email attachments, even if they appear to come from a trusted company such as this supposed email from the iTunes store. Criminals have become quite adept at mimicking legitimate corporate emails and can make their fraudulent emails seem quite authentic.
Table of Contents
Backdoor.Cycbot.G Lets Criminals into Your Computer System
Backdoor.Cycbot.G has been linked with dangerous botnets, that is, vast networks of computer systems infected with a Trojan that allows a hacker to control them from afar. Computers infected with Backdoor.Cycbot.G will contact a specific IRC server in order to receive automated instructions. This allows criminals to coordinate attacks by controlling thousands of infected computers simultaneously. Backdoor.Cycbot.G is the first step in this kind of criminal activity, creating a hole in the victim's security which can then be exploited to install a dangerous RAT (Remote Access Trojan) which allows this level of remote control. Criminals use computers infected with Backdoor.Cycbot.G to perform all kinds of dangerous actions. Some examples of these criminal actions include sending out massive quantities of spam email (such as the spam email that contains the infected attachment that delivers Backdoor.Cycbot.G), purposefully overloading a specific server through a DDoS attack, or participating in networks dedicated to money laundering or distribution of child pornography.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Fortinet | W32/Gbot.RWR!tr.bdr |
| AntiVir | TR/Kazy.50365.7 |
| BitDefender | Gen:Variant.Kazy.50365 |
| Kaspersky | Backdoor.Win32.Gbot.rwr |
| CAT-QuickHeal | Trojan.Cycbot.b |
| TrendMicro | TROJ_GEN.R4FCCE1 |
| AVG | Generic26.AZJZ |
| AVG | unknown virus Win32/DH{NA} |
| Kaspersky | Trojan.Win32.Menti.mimy |
| ClamAV | Trojan.Agent-278835 |
| AVG | BackDoor.Generic15.BPFY |
| Avast | Win32:Cycbot-UR [Trj] |
| AVG | Generic25.BYLN |
| DrWeb | Win32.HLLW.Autoruner1.2147 |
| F-Secure | Rogue:W32/FakeAv.EZ |
SpyHunter Detects & Remove Backdoor.Cycbot.G
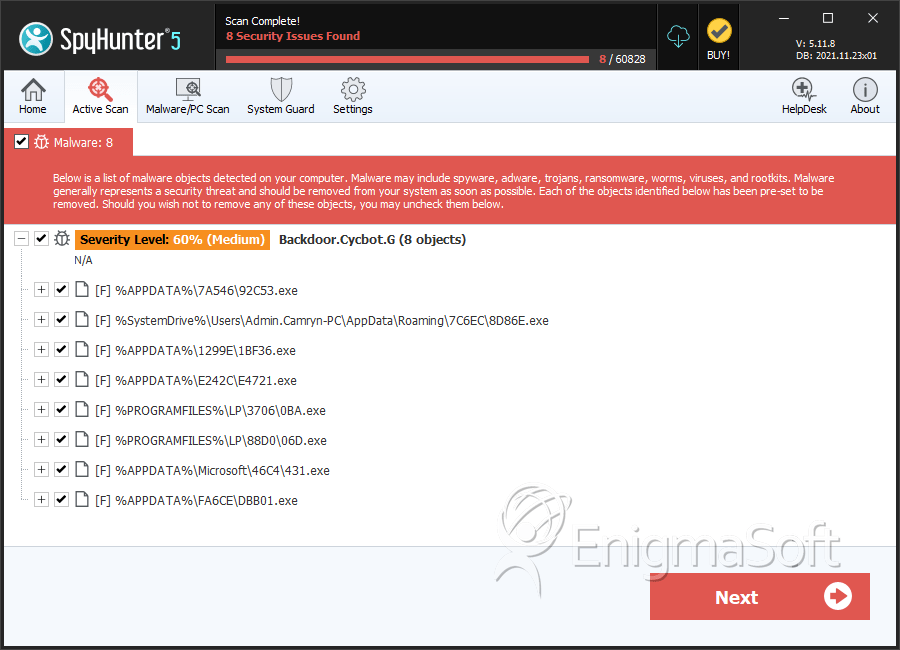
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 049.exe | f0c32895313a7a1d5ba8016d73d3ef6e | 43 |
| 2. | 636.exe | 63d2c701f256066a688ca421a66cd0ad | 33 |
| 3. | 92C53.exe | 1edb623f52c6ca84b7b7ded517ed5c36 | 31 |
| 4. | 8D86E.exe | 96634cae1833ff6dc58b697d135b2bcc | 24 |
| 5. | 1BF36.exe | eeaa55cd828b2b4fd91898d57ae243d8 | 17 |
| 6. | java.exe | efd07fc7b3e13248215cb44338a8b9a3 | 8 |
| 7. | F16.exe | 6603336c067282d5889912e0dd2bf875 | 7 |
| 8. | 0BA.exe | 00c1a57f17d751ef9f9b77e09ef0e3b2 | 5 |
| 9. | java.exe | 231dc5f80657b2f94280d67b11d710db | 5 |
| 10. | 06D.exe | f3e783ebfcac36b471a0122d34fa2c21 | 3 |
| 11. | 431.exe | 1a76ba96f623c3a8cd48f78002eb1df7 | 3 |
| 12. | E68.exe | b63ee194af49b866e8ace0d60b793972 | 2 |
| 13. | 1D72A.exe | 57104c80feb2eb39107335c460644883 | 2 |
| 14. | 86EB3.exe | 25a545171ad394b93ffab2dcddb1dd04 | 2 |
| 15. | CA7FF.exe | 168e5ca8983bd57347fbc251ce21bab9 | 2 |
| 16. | DF590.exe | f58f6b43b04dfe17db38c9c9c522314f | 2 |
| 17. | 3B5.exe | f942202bf5e5e359bfea2edb23c750c9 | 2 |
| 18. | C6F.exe | 051346caaf2767531a1aba8b55cb3afd | 2 |
| 19. | AE4.exe | 24f8aee77069cc3866022e285f101fed | 1 |
| 20. | 23D97.exe | 2c95652147440529d354d1093d037113 | 1 |
| 21. | chrome.exe | c66d133b4c0edab319e07daaaf8402c1 | 1 |
| 22. | java.exe | b3a9bc46ef26dfb8ff9d45580491bdb7 | 1 |
| 23. | 0CC.exe | 3b130c9d702b795d15f2a01a51e3505b | 1 |
| 24. | java.exe | 2d60380f8b0f019852b567e01bda9691 | 1 |
| 25. | 45F46.exe | 3512404389377320fba4b371da4cd8c2 | 1 |
| 26. | java.exe | b4f2c5c4cdccce6503927a0414ccb6d6 | 1 |
| 27. | java.exe | 2bd8320cc9fc03f8f4fa14bd61646e3e | 1 |
| 28. | 7D1.exe | 9867c309b4ca46d781da435ed667064d | 1 |
| 29. | iexplore.exe | b21d9e1df64c9e5ec41defdea67a8ce9 | 1 |
| 30. | java.exe | fe793524d89ee1c889041cda481b1dbd | 1 |
| 31. |
C:\Documents and Settings\ |
||
| 32. |
C:\Documents and Settings\ |
||
| 33. |
C:\Documents and Settings\ |
||
| 34. |
C:\Documents and Settings\ |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.