Anatova Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | January 24, 2019 |
| Last Seen: | October 30, 2020 |
| OS(es) Affected: | Windows |
The Anatova Ransomware is an encryption ransomware Trojan. This means that the Anatova Ransomware is designed to carry out an attack that involves taking the victim's files hostage by enciphering them with a strong encryption algorithm. The Anatova Ransomware then demands a ransom payment in exchange for supposedly restoring access to the compromised data.
Table of Contents
Although Very Common, the Anatova Ransomware can Cause a Lot of Damage
The Anatova Ransomware uses the AES encryption to make the victim's files inaccessible. The Anatova Ransomware demands a ransom payment in DASH, a cryptocurrency, and delivers its ransom note as a text file named 'ANATOVA.TXT' dropped on the infected computer. The Anatova Ransomware targets the user-generated files in its attack, which may include a wide variety of types that may include media files, databases, configuration files and numerous others. Threats like the Anatova Ransomware target the files specified below in these attacks:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
Typically, the Anatova Ransomware will be delivered to the victim through spam email messages, although there are numerous other ways in which threats like the Anatova Ransomware can be delivered, which include fake software downloads and tampered online advertisements. Once the Anatova Ransomware has been installed and the victim's files compromised, the Anatova Ransomware delivers the following message in its ransom note:
'All your files are crypted. Only us can decrypt your files, you need pay 10 DASH in the address:
XpRvUwSjSeHfJqLePsRfQtCKa1VMwaXh12
After the payment send us the address used to make the payment to one of these mail addresses:
anatova2@tutanota.com
anatoday@tutanota.com
Later wait for our reply with your decryptor. If you want can send us ONE JPG FILE ONLY max 200kb to decrypt per free before of payment.
Dont try fuck us, in this case you NEVER will recover your files. Nothing personal, only business.
Send this file untouched with your payment or/and free file!'
Preventing the Anatova Ransomware Attacks
Unfortunately, you cannot recover the files encrypted by the Anatova Ransomware at this time. Because of this, it is paramount that computer users take measures to prevent this and similar attacks. The best prevention method is to have backup copies of all data, preventing the criminals from having any leverage to enable them to demand a ransom payment. If the copies are kept on the cloud or an external memory device, then the victim can simply delete the compromised files and the Anatova Ransomware itself and restore any compromised data by replacing it with the backup copy. Apart from having file backups, PC security researchers also advise that computer users should have a security program that is always updated and capable of detecting and removing the Anatova Ransomware before it can carry out its attack.
SpyHunter Detects & Remove Anatova Ransomware
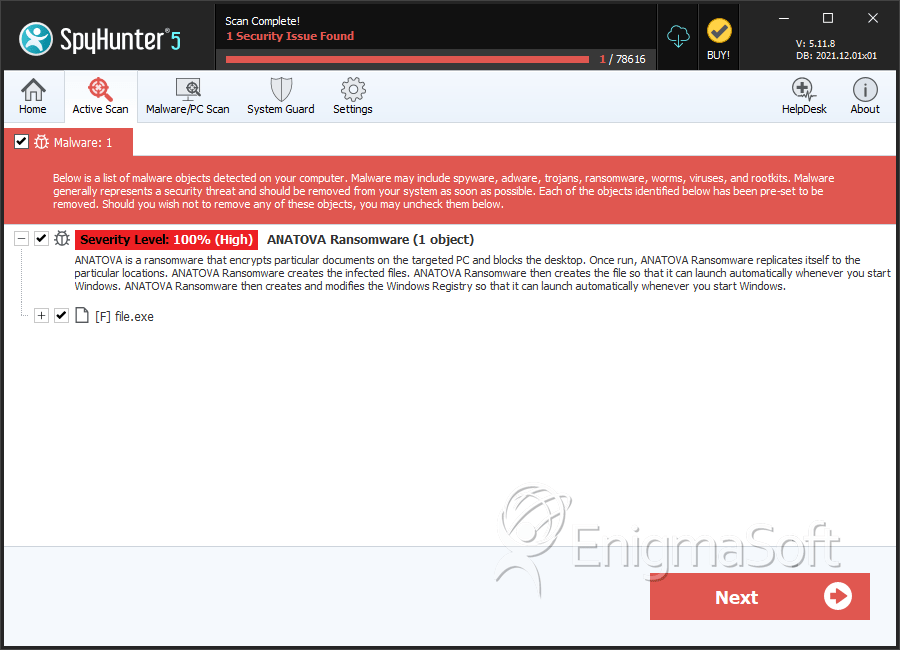
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 2a0da563f5b88c4d630aefbcd212a35e | 0 |

