ZeroAccess
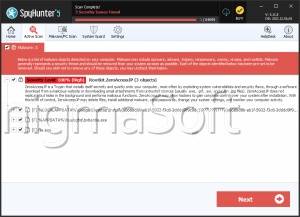
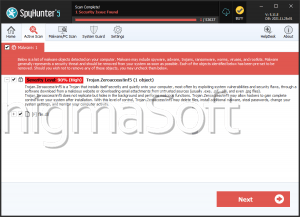
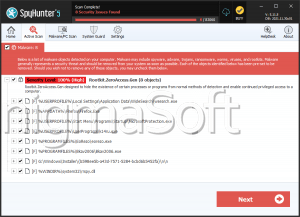
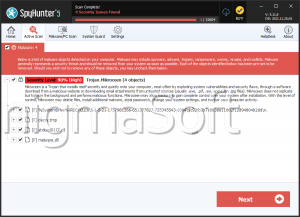
ZeroAccess is a Trojan that has rootkit-like behaviors. This Trojan was first discovered in 2011, so it is important to make sure that all security software are updated up to 2011 at the least. The ZeroAccess Trojan, like many rootkits, has the ability to create a hidden file system, operate completely undetected and create a backdoor into your computer. This backdoor is nothing more than a hole in your computer's security, which a hacker can use to transmit and collect data to and from your computer. The ZeroAccess Trojan also attempts to establish a connection with a remote server. Usually, this is done either to send your private information to a remote party or to allow a hacker to install additional malware onto your computer. Unlike severe rootkits, the ZeroAccess Trojan can be removed with most anti-malware programs, as long as they are updated to include the ZeroAccess Trojan in their databases. ESG team of PC security researchers recommends removing the ZeroAccess Trojan in Safe Mode, in order to bypass its self-defense mechanisms. Because the ZeroAccess Trojan serves as a gateway for other malware, ESG team of malware analysts also recommends making sure that no other malware has been installed onto your computer and that your online accounts and credit card information have not been compromised.
Table of Contents
The ZeroAccess Trojan is Associated with Severe Malware Threats
The ZeroAccess Trojan is mainly used to install other malware such as Backdoor.Tidserv onto the infected computer. This other malware can take a variety of forms with different threat levels and effects. A common kind of malware that may be installed using the ZeroAccess Trojan's back door is a Remote Access Tool. A Remote Access Tool, or RAT, allows a hacker to take control of your computer system. Once the remote access tool has been installed, the hacker can do practically whatever he wants with your computer. This may include installing Trojans that can steal your personal information and sensitive data; installing software designed to scam you, such as rogue security programs or ransomware; or directly using your computer for criminal activities. Computers infected with a RAT will often be used to send out spam email, participate in distributed denial of service (DDoS) attacks, or contribute to other forms of cybercrime. This makes the removal of ZeroAccess Trojan an important priority. Computers infected in this way are unsafe not only to their users, but to the general population.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %System%\Drivers\win32k.sys | |
| 2. | %System%\Drivers\classpnp.sys |