Updated CryptoWall 3.0 Ransomware Using Advanced Anti-Tracking Features
Cybercrooks are always on the look for ways to efficiently garnish their bank account at the expense of victimized computer users. In their latest efforts to do so, they have updated the popular CryptoWall Ransomware threat.
The cyber criminals behind the CryptoWall Ransomware released a new version of the malware, which is known to encrypt files and then extort the computer user for money promising a decryption key. CryptoWall 3.0 uses RC4 encrypted I2P channels for its communications with the Command & Control servers and integrates a fail-safe mechanism in case of damaged connections. Basically, this is a means for the ransomware threat to evade tracking in its efforts to connect and receive malicious instructions upon attacking an infected computer.
The new version is distributed via numerous methods including drive-by download attacks, Exploit Kits, known plug-in vulnerabilities, botnets and spam emails loaded with attachments carrying the CryptoWall malware. You can say the CryptoWall is among the nastiest threats on the internet in the realm of ransomware.
Computer users infected with the CryptoWall version 3.0 may have their video, text and image files encrypted with the RSA2048 algorithm. Additionally, they are presented with a tailor-suited notification of what happened. The CryptoWall 3.0 message informs users that they have to pay a ransom in the amount of 2.17 Bitcoins ($500) within seven days. The message is rather firm in its demands but may not fully deliver on its promises if the outrageous fee is paid up.
The code dissection performed by a French security researcher Kafeine, revealed that the CryptoWall 3.0 conducts geolocation observations of the victim's computer through its IP address. The update to version 3.0 enables it to do this in order to facilitate the display of a custom message usually in the language matching the location of the computer, which you can see below:
Image 1. CryptoWall version 3.0 message in French. - Source: Malware.DontNeedCoffee.com
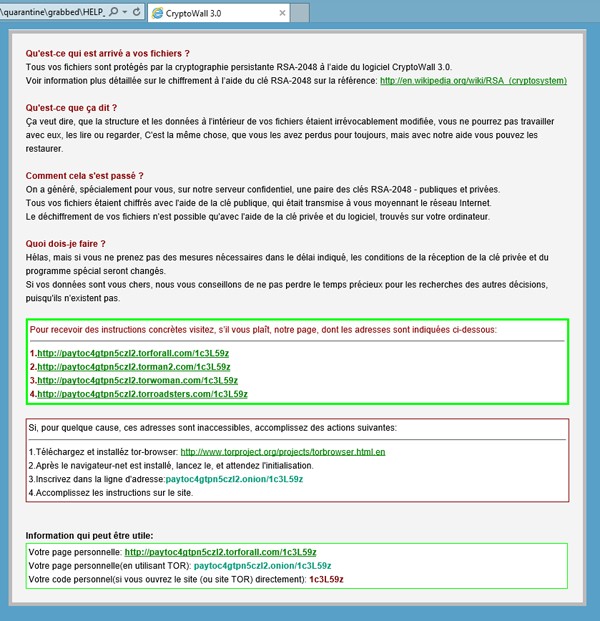
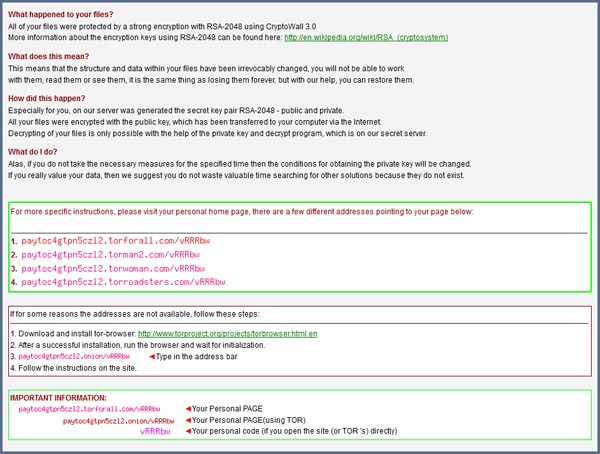
Image 2. 'HELP_DECRYPT.HTML' message by CryptoWall version 3.0 - Source: Malware.DontNeedCoffee.com
CryptoWall 3.0 Techie Details
The ransom demand is presented in the form of several files placed on the victim's desktop: HELP_DECRYPT.HTML, .PNG, .TXT, or .URL It could be noted that the cyber criminals applied extra efforts in helping victims to create a Bitcoin wallet and purchase Bitcoins for the ransom, much like in the case of the CoinVault ransomware.
The boldness of CryptoWall leads us to the fact that it offers one free decryption service in order to validate the efficiency of the ransomware's decryption mechanism. After a successful verification, users are suggested to purchase the decryption key via a Bitcoin transaction to designated virtual wallet codes: 15qZLHkcgGnqaBByno2nq6ufa1og3PjnxU and 1JYYzNHDaGC7noiE4eKatuYA4AThqVocDd.
Kafeine's research revealed that the links offered by CryptoWall version 3.0 and its communications are routed through RC4 encrypted I2P channels allowing it to direct communications anonymously with the C&C servers. If the provided websites are not available through the aforementioned links, victims are advised to install the Tor Browser Bundle and follow a URL that will lead them to a Tor-located website with instruction code: paytoc4gtpn5cz12.onion/vRRRbw
Security experts are steadily reminding computer users that the successful payment of the ransom will not result in recovering or decrypting your files. CryptoWall 3.0 uses the secure RSA2048 encryption method seen in its predecessors CryptoWall 2.0, CryptoDefense and CryptoLocker to ensure the complete encryption of files. Although, CryptoWall does not use social engineering techniques found in ransomware like Kovter, data suggests that the criminals behind the scheme managed to accumulate more than $1.1 million. Computer users, as usual, are urged to keep their software updated and utilize the latest antimalware protection to thwart off attacks from newly-updated ransomware threats and other aggressive malware.