Troj/Plugx-G
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 50 % (Medium) |
| Infected Computers: | 3 |
| First Seen: | February 28, 2013 |
| Last Seen: | May 11, 2020 |
| OS(es) Affected: | Windows |
Troj/Plugx-G is a dangerous backdoor Trojan that has been involved in high profile attack that uses advanced techniques to trick security software in order to protect itself from detection and removal. For all intents and purposes, the Troj/Plugx-G Trojan has little to set Troj/Plugx-G apart from typical backdoor Trojan attacks. However, Troj/Plugx-G uses social engineering tactics that target pro-Tibet activists and some self-defense tactics that have captures the attention of security analysts. This version of Troj/Plugx-G uses several protective layers in order to trick anti-malware software. One of these protective layers makes security software believe that Troj/Plugx-G is a signed, legitimate Nvidia application!
Table of Contents
How a Malicious Document Installs the Troj/Plugx-G Backdoor on a Victim’s Computer
The Troj/Plugx-G infection process is anything but straightforward. This complicated process has caught the attention of PC security researchers. According to malware analysts, Troj/Plugx-G takes advantage of a known security vulnerability, executes malicious code in two stages and takes advantage of a legitimate application in order to attack a computer user. The initial attack begins with a malicious RTF document that uses a popular vulnerability known as CVE-2012-0158. This malicious RTF document contains an embedded OLE document which takes advantage of the well-known Listview vulnerability. The basic steps in this kind of attack are the following:
- A malicious RTF document uses the vulnerability mentioned above to execute malicious code.
- This malicious code executes a malicious executable file that is extracted from the malicious file.
- This executable installs a backdoor on the victim's computer which can then be used to deliver other malware and spy on the infected computer.
The Twists Involved in the Installation of Troj/Plugx-G
One interesting aspect of the Troj/Plugx-G attack is that Troj/Plugx-G uses two stages of malicious code, making it more difficult for PC security researchers to study and for anti-malware programs to detect. Opening the malicious RTF file in Microsoft Office triggers the malicious code. However, this malicious code does not install Troj/Plugx-G. Rather, it directs to a second stage of executable code that is hidden deeply in the malicious RTF file. PC security researchers studying the Troj/Plugx-G attack pattern have stumbled upon clever obfuscation techniques deliberately placed in this document to make it more difficult for computer security analysts do understand what is going on. This involves a clever decoy ZIP file and various layers of encryption. Despite this attack's sophistication, the Troj/Plugx-G infection can still be avoided by simply refusing to open unsolicited email attachments and following basic online safety guidelines.
SpyHunter Detects & Remove Troj/Plugx-G
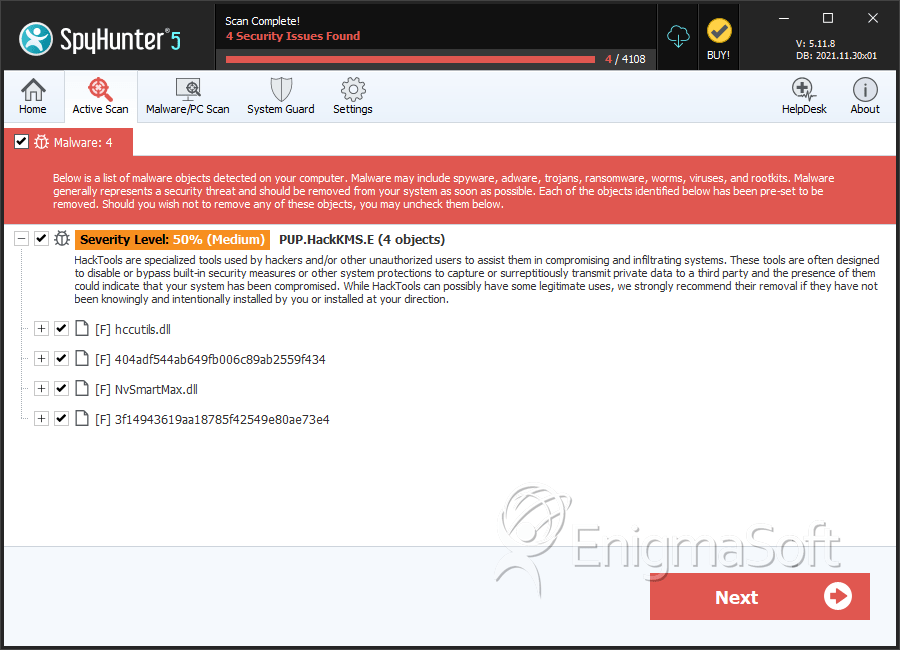
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | %ALLUSERPROFILES%\SxS\NvSmartMax.dll | ||
| 2. | %ALLUSERPROFILES%\SxS\Nv.exe | ||
| 3. | %ALLUSERPROFILES%\SxS\NvSmartMax.dll.url | ||
| 4. | hccutils.dll | 2910076a244e57de342b1f080c8e50a9 | 0 |
| 5. | 404adf544ab649fb006c89ab2559f434 | 404adf544ab649fb006c89ab2559f434 | 0 |
| 6. | NvSmartMax.dll | d659d95d46f71f172cd4f2aca9532949 | 0 |
| 7. | 3f14943619aa18785f42549e80ae73e4 | 3f14943619aa18785f42549e80ae73e4 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.