Troj/DarkDrp-A
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 90 % (High) |
| Infected Computers: | 1 |
| First Seen: | September 11, 2012 |
| Last Seen: | April 14, 2020 |
| OS(es) Affected: | Windows |
The Troj/DarkDrp-A Trojan is the second component in a malware attack that involves attacking a computer through a social engineering scam that initiates with a HLP file, that is, a fake Windows Help file. Criminals have found to use these Windows Help files in order to install malicious executable files on the victim's computer. For example, a malicious HLP file detected in August of 2012 known as Troj/HlpDrp-B will cause the infected computer to display a misleading error message while Troj/HlpDrp-B installs Troj/DarkDrp-A in the background. This malicious HLP file, named 'Amministrazione.hlp' (Italian for 'Administration') is a novel way of delivering malware into a victim's computer.
Table of Contents
The Malware Attack that Includes the Troj/DarkDrp-A Component
Troj/DarkDrp-A is part of a multi-component malware attack that also includes a social engineering approach in order to convince computer users to open what seems to be a safe Windows Help file. However, when this file is opened, it will force the victim's computer to display an error message reading:
Help could not read the current Help file.
Make sure there are no errors on the disk, or if the file is on a network drive, that the server is active. (163)
This error message is designed to distract the victim. While the victim is reading this error message, the Troj/DarkDrp-A component is dropped in the background. Troj/DarkDrp-A takes the form of an executable file that is named Windows Security Center.exe. This malicious executable file will install a keylogger component on the victim's computer, in the form of a malicious DLL file. Detected as both Troj/Agent-OVJ or Mal/DarkShell-A, this dangerous DLL file will keep track of the victim's activity on the infected computer in order to steal important data, which may include credit card numbers, email passwords, and online banking data.
The Goal of a Troj/DarkDrp-A Infection
Once installed, the malicious keylogger will keep track of all activity on the victim's computer, storing all keystrokes on a fake UserData file in the Documents and Settings directory. The malicious DLL will attempt to send this information to the remote host images.zyns.com, known to be linked to malware attacks. It is important to be suspicious of HLP files. While Windows Help files are generally considered safe, they can be altered to install malware such as Troj/DarkDrp-A on the victim's computer.
SpyHunter Detects & Remove Troj/DarkDrp-A
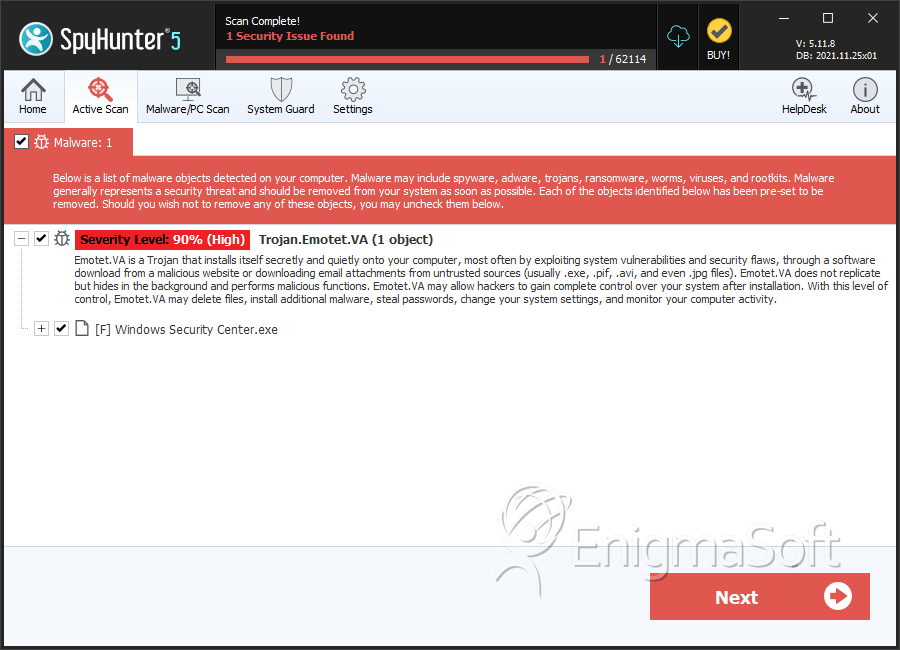
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | RECYCLER.DLL | ||
| 2. | Windows Security Center.exe | ||
| 3. | \Documents and Settings\username\Local Settings\Application Data\UserData.dat | ||
| 4. | Amministrazione.hlp | ||
| 5. | Windows Security Center.exe | d63932bcb32ffd8ae244a646fb4263cc | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.