Radxlove7@india.com Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 11 |
| First Seen: | August 23, 2016 |
| OS(es) Affected: | Windows |
The Radxlove7@india.com Ransomware belongs to an extensive family of ransomware that can be identified because of its use of the extension '.XBTL' to mark the files that have been encrypted. Like other ransomware Trojans, the Radxlove7@india.com Ransomware is designed to take the victim's files hostage by encrypting them with a strong encryption algorithm. The Radxlove7@india.com Ransomware belongs to a large family of ransomware that uses india.com email addresses and tends to target enterprise systems rather than individuals. Some of the most threatening attacks attributed to threats in the Radxlove7@india.com Ransomware's family have been on servers belonging to certain businesses, resulting in significant monetary losses and affecting numerous customers. PC security analysts advise computer users to not pay the Radxlove7@india.com Ransomware's ransom since this is what allows con artists to continue creating variants in this threat family. Instead, you should have a robust backup policy so that encrypted files can be restored from a backup version quickly.
Table of Contents
How the Radxlove7@india.com Ransomware’s Attack Works
The Radxlove7@india.com Ransomware attack is simple and similar to countless other encryption ransomware Trojans. The Radxlove7@india.com Ransomware may arrive on the victim's computer through a corrupted email attachment. The Radxlove7@india.com Ransomware will encrypt the victim's files using its strong encryption algorithm and then drop a ransom note in the form of a text file. The Radxlove7@india.com Ransomware ransom note will contain information on how to pay the ransom by using some anonymous payment method and informing the victim of the attack. In the case of the Radxlove7@india.com Ransomware, computer users are instructed to send an email to the Radxlove7@india.com email address.
When the Radxlove7@india.com Ransomware enters a computer, it may be dropped as a file with the extension EXE, DLL, TMP, VBS, BAT or CMD. This file may be delivered to one of the following directories on the targeted computer:
%AppData%
%Roaming%
%Local%
%LocalRow%
%Windows%
%System%
%System32%
%Temp%
The file containing the Radxlove7@india.com Ransomware may be named in a way that makes it seem as if it is a legitimate file belonging to the Windows operating system. Once the Radxlove7@india.com Ransomware has been installed, it makes changes to the Windows' settings that allow the Radxlove7@india.com Ransomware to run when Windows starts up automatically. To carry its attack, the Radxlove7@india.com Ransomware will search for the following file types on the victim's computer:
PNG .PSD .PSPIMAGE .TGA .THM .TIF .TIFF .YUV .AI .EPS .PS .SVG .INDD .PCT .PDF .XLR .XLS .XLSX .ACCDB .DB .DBF .MDB .PDB .SQL .APK .APP .BAT .CGI .COM .EXE .GADGET .JAR .PIF .WSF .DEM .GAM .NES .ROM .SAV CAD Files .DWG .DXF GIS Files .GPX .KML .KMZ .ASP .ASPX .CER .CFM .CSR .CSS .HTM .HTML .JS .JSP .PHP .RSS .XHTML. DOC .DOCX .LOG .MSG .ODT .PAGES .RTF .TEX .TXT .WPD .WPS .CSV .DAT .GED .KEY .KEYCHAIN .PPS .PPT .PPTX ..INI .PRF Encoded Files .HQX .MIM .UUE .7Z .CBR .DEB .GZ .PKG .RAR .RPM .SITX .TAR.GZ .ZIP .ZIPX .BIN .CUE .DMG .ISO .MDF .TOAST .VCD SDF .TAR .TAX2014 .TAX2015 .VCF .XML Audio Files .AIF .IFF .M3U .M4A .MID .MP3 .MPA .WAV .WMA Video Files .3G2 .3GP .ASF .AVI .FLV .M4V .MOV .MP4 .MPG .RM .SRT .SWF .VOB .WMV 3D .3DM .3DS .MAX .OBJ R.BMP .DDS .GIF .JPG ..CRX .PLUGIN .FNT .FON .OTF .TTF .CAB .CPL .CUR .DESKTHEMEPACK .DLL .DMP .DRV .ICNS .ICO .LNK .SYS .CFG.
Whenever the Radxlove7@india.com Ransomware finds one of these types of files, it encrypts it using its strong encryption algorithm. Every time the Radxlove7@india.com Ransomware encrypts a file, it drops a text file containing its ransom message in that directory. The Radxlove7@india.com Ransomware also will change the encrypted file's extension to '.XBTL.'
Mitigating the Effects of a Radxlove7@india.com Ransomware Attack
Unfortunately, it may not be possible to decrypt the files that have been encrypted by the Radxlove7@india.com Ransomware without access to the decryption key. Because of this, it is a must-do to have backups of all files. That way, computer users can restore the files encrypted by the Radxlove7@india.com Ransomware from the backup location easily, making it unnecessary to pay the Radxlove7@india.com Ransomware's ransom demand.
SpyHunter Detects & Remove Radxlove7@india.com Ransomware
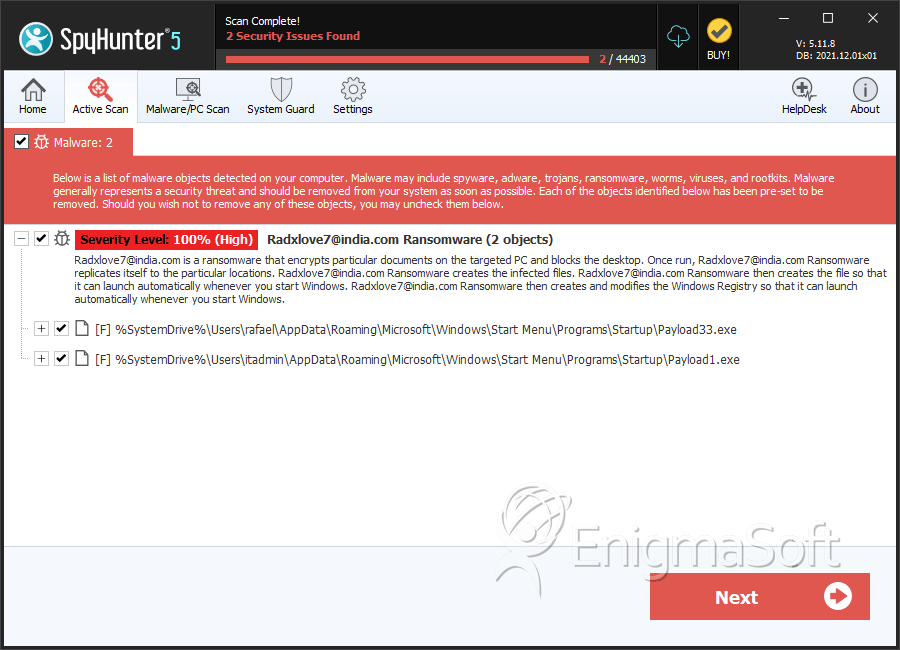
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Payload33.exe | 8fdf33752a626f8c40ca948d01225892 | 8 |
| 2. | Payload1.exe | 976d5f82cf82cd8079324f2f071b19d7 | 3 |
