Parasite HTTP RAT
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 275 |
| First Seen: | November 6, 2012 |
| Last Seen: | February 27, 2023 |
| OS(es) Affected: | Windows |
The Parasite HTTP RAT malware is a Remote Access Trojan that was found on compromised systems in July 2018. The Parasite HTTP RAT was used in targeted attacks on human resources departments and job search agencies. A large phishing campaign was used to deliver Microsoft Word files with an embedded macro to users. The macro script was designed to download an encrypted shell from a compromised site; decrypt the payload; perform series of checks for debugging tools, VM (Virtual Machine) environment markers and process analysis kits before the malware is installed.
The Parasite HTTP RAT features a modular structure and can load plug-ins to expand its capabilities as needed. The Parasite HTTP RAT developers have boasted on the Dark Web that their program has a small size (~49kb uncompressed, ~23kb compressed); the program strings are encrypted and it can bypass firewall setups. Other notable features you can find in the Parasite HTTP RAT include support for x86 and x64 Windows systems; = encrypted communication with the 'Command and Control' servers, as well as SSL with a self-signed certificate. Parasite HTTP RAT can inject malicious code into clean processes, load plug-ins and avoid detection using anti-emulation, anti-debugging and a hidden startup.
Threat actors who buy a subscription for the Parasite HTTP RAT are provided an admin panel with CAPTCHA protection and an online builder with multiple backup domains for 'Command and Control' purposes. The Parasite HTTP RAT has all features you would expect from a Remote Access Trojan and then some. The Parasite HTTP RAT can retrieve passwords saved in the Web browser, as well as passwords for IM apps, FTP clients and Email managers. Threat actors can access a hidden VNC (Virtual Network Computing) channel and transfer keyboard and mouse input to remote infected hosts.
Compromised users may not notice the activity of the Parasite HTTP RAT on their systems due to the extensive evasion techniques implemented by the malware developers. You need to avoid spam emails and run security scans regularly to ensure minimal exposure to attacks with Parasite HTTP RAT. AVs may show PC users the following detection names if they have been compromised:
RDN/Generic.grp
TROJ_INJECT.TIFACAR
Trojan ( 00537a6b1 )
Trojan.GenKryptik!8.AA55 (CLOUD)
Trojan.Generic.D1DA9610
Trojan.GenericKD.31102480 (B)
Trojan.Win32.Agent.218112.U
Trojan.Win32.Shelma.acas
Trojan/Win32.Shelma.R233008
Trojan:Win32/Shewab
Win32/Trojan.Exploit.c7a
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Fortinet | W32/Bckdr.AJ |
| Ikarus | not-a-virus:Server-Web.Win32.SmallHTTP |
| Microsoft | HackTool:Win32/Httprat |
| Antiy-AVL | Server-Web/Win32.SmallHTTP |
| Sophos | Mal/Bckdr-AJ |
| McAfee-GW-Edition | Heuristic.LooksLike.Win32.Suspicious.C |
| AntiVir | SPR/SmallHTTP.F |
| Comodo | UnclassifiedMalware |
| Kaspersky | not-a-virus:Server-Web.Win32.SmallHTTP.30565 |
| eSafe | Win32.Server.Web.Sma |
| Avast | Win32:PUP-gen [PUP] |
| Symantec | Trojan.Gen.2 |
| K7AntiVirus | RemoteTool |
| McAfee | Generic PUP.x!bdc |
| CAT-QuickHeal | HackTool.Httprat (Not a Virus) |
SpyHunter Detects & Remove Parasite HTTP RAT
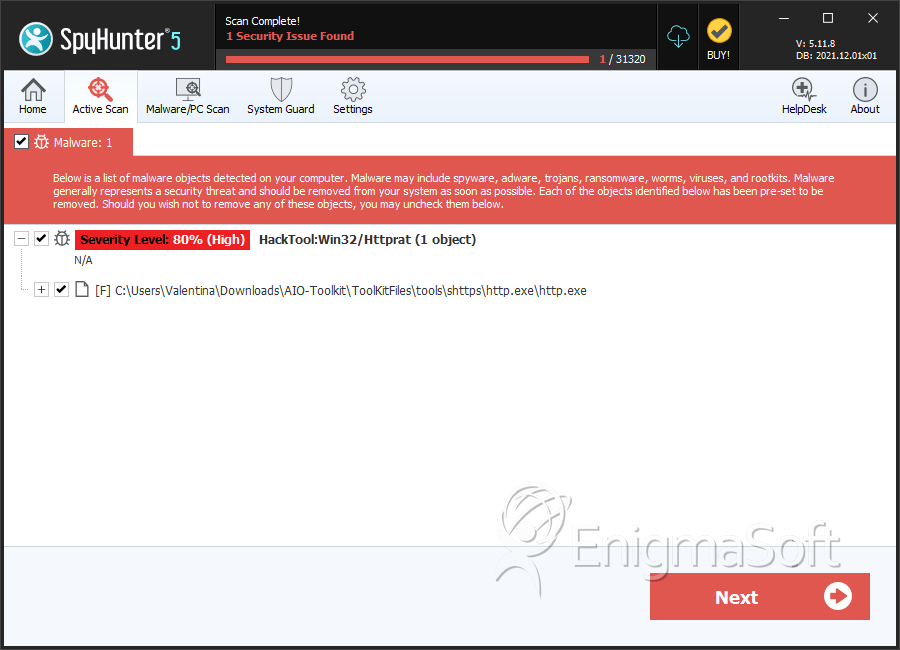
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | http.exe | b93df180f915346b01d03ccc2bc2701f | 147 |
