NGRBot
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 14,309 |
| Threat Level: | 50 % (Medium) |
| Infected Computers: | 704 |
| First Seen: | October 12, 2011 |
| Last Seen: | September 17, 2023 |
| OS(es) Affected: | Windows |
NGRBot is a dangerous malware infection that is known for mimicking Skype in order to trick computer users into opening its malicious executable file. ESG security researchers observed that the NGRBot infection is being distributed in spam email messages that contain what is supposed to be a Skype link. This supposed link claims to lead the computer user to an image file. However, this link actually downloads a file named skype_09-10-12_image.exe. Of course, the EXE extension is not correspondent to an image file. Rather, this malicious executable installs NGRBot, also known as Dorgbot or Dorkbot. This particular variant of the NGRBot infection was first detected in October 6 of 2012. It contains the same functionality as previous Dorkbot variants except for an additional malicious module that allows this malware threat to abduct sensitive data such as credit card details or login credentials for numerous websites.
The NGRBot infection contains a specific module that allows this threat to steal private information such as login credentials for popular websites and online accounts. By analyzing NGRBot's code, ESG security researchers have observed that the NGRBot can steal the following private information:
- The NGRBot malware infection has the ability to detect web traffic involving credit card transactions. It is designed to steal credit card data as well as online banking information. NGRBot then transfers this data to a third party which can then use these credit card numbers to steal the victim's identity.
- NGRBot also contains a module that allows NGRBot to steal login information for popular webmail and social media services, such as Gmail, Facebook, Yahoo and Twitter.
- However, the NGRBot infection can also steal login information for popular pornographic websites (such as YouPorn and Brazzers) or for some of the largest private torrent websites (such as WhatCD or Torrentleech). This login information is then sold on shady websites and IRC networks.
- In fact, few websites are not included in NGRBot's list of potential theft targets. This malware infection will steal login credentials for websites ranging from eBay and PayPal to Godaddy and Netflix, among many others.
Like most Dorkbot variants, NGRBot spreads via Skype and instant messaging services. It will send out messages from an infected computer that will typically read 'hey, have you seen this pic?' followed by a malicious link to the NGRBot executable. These messages can be sent out in dozens of different languages, allowing NGRBot to attack computers all around the world.
SpyHunter Detects & Remove NGRBot
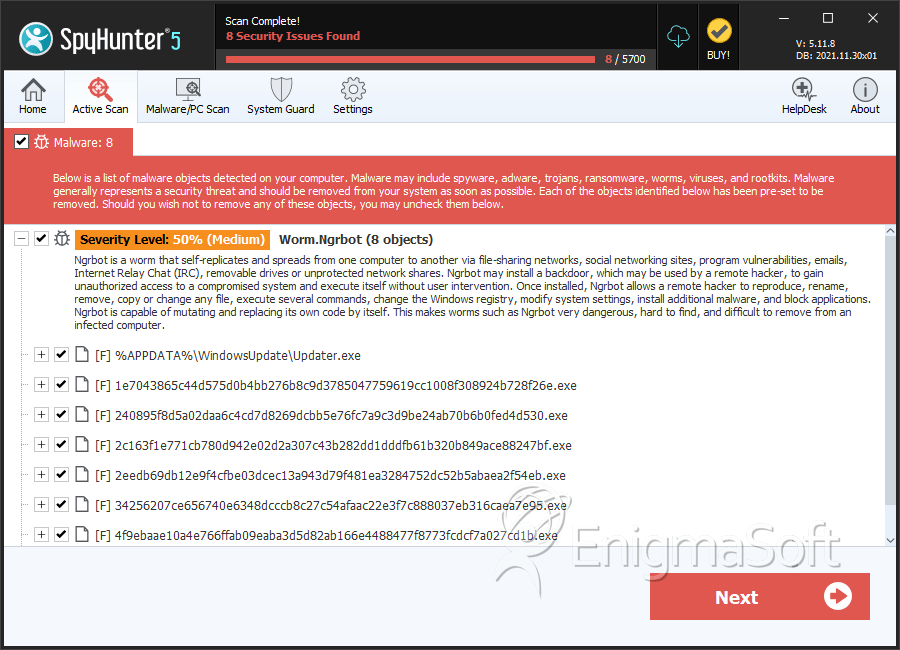
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Updater.exe | 37b5e18358555a966797b758ffeff421 | 1 |
| 2. | Updater.exe | 5f4afe2a2d57f7d465aa79c2f54b4c98 | 1 |
| 3. | Updater.exe | 976aa6512b7c51f981cdabd139339cba | 1 |
| 4. | Updater.exe | 31df33e39e9dca80dffa47cb16a92447 | 1 |
| 5. | Updater.exe | 85fa792219fbd83172e5995bc946cf89 | 1 |
| 6. | Updater.exe | bc48162696ef51f3cd0e41e5525e276c | 1 |
| 7. | Updater.exe | c7322ed05d4d9d56de469cc395b3523a | 1 |
| 8. | Updater.exe | 0b8ea7404f6d83b2d0a1f21d90c087d1 | 1 |
| 9. | skype_09-10-12_image.exe | ||
| 10. | 1e7043865c44d575d0b4bb276b8c9d3785047759619cc1008f308924b728f26e.exe | a8f8dca809ebe47ebd4b8959c31feb09 | 0 |
| 11. | 240895f8d5a02daa6c4cd7d8269dcbb5e76fc7a9c3d9be24ab70b6b0fed4d530.exe | dc9f89723be818ce3aeb3aa90952527e | 0 |
| 12. | 2c163f1e771cb780d942e02d2a307c43b282dd1dddfb61b320b849ace88247bf.exe | 7a50d83015675403368b2bef66e318aa | 0 |
| 13. | 2eedb69db12e9f4cfbe03dcec13a943d79f481ea3284752dc52b5abaea2f54eb.exe | de5b1fa1d1e4f77e37f7d690634c0815 | 0 |
| 14. | 34256207ce656740e6348dcccb8c27c54afaac22e3f7c888037eb316caea7e95.exe | 0d1d3e9872c31a9fdb4dc159fbce0bd1 | 0 |
| 15. | 4f9ebaae10a4e766ffab09eaba3d5d82ab166e4488477f8773fcdcf7a027cd1b.exe | 2ee9b76bf1bdd22568932a8d0f4cc65f | 0 |
| 16. | 5c7b5503f3d89d01b87bc3f011291a7e88132930b3286b08e9336a98553432d4.exe | 31805681a9b937b4719dc5ffd87b0bfe | 0 |
| 17. | 69d024a92ddfcf100ef49f386d6e7640cfd68d23a4ea0aa2b3137f23a8fe51b8.exe | 0b8ac10e8c00019836e49c175bb2dbb5 | 0 |
| 18. | 83cbd9b81abb41ecafd55267d572c85cbd446ce46966d2d88b2f21b72030c1d1.exe | 7297b7162a6b6fd4a83754498fbf2476 | 0 |
| 19. | caa7055cc2b8cddd4fc393684f486a41d0337dd8756887fc5e4d825f011dd725.exe | 2885b3e20b8ab5c69de65a4e4a41217d | 0 |
| 20. | d3ba40454935b2c76739e9c9817e111a4367184e3a53ceb4ecb793c00f5c1e55.exe | 7baf8d13dad8f72095e1dd3430153c08 | 0 |
| 21. | d430d81486b8ba0612f7cfcf4690753d959e3e83f92da7ad100b503608a24be6.exe | b0b0bdec8eb412cede97f5af42a75bfe | 0 |
| 22. | dcdee113e5975c51af48c267ac2190be8c8bf22dac5ec46562dbb36eca9ea0dc.exe | 0321b58d6fdea96d9c507af0128a57e6 | 0 |
| 23. | ddfd6b9cf184c31970b749a9272ccacdc14ed7062000cdcc660fc25e574aabb9.exe | 02b6329f8867151ae3bfa83793d3721b | 0 |
| 24. | f301b32407a2c914fea10b3199ef24da8a5db3770608ac515cef80a42150fd30.exe | ab1ed595ac14fe212ab73ed041b89003 | 0 |
| 25. | file.exe | ccc4e1ec557e352ffe5c52b651b67c76 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.