Mousetrap Trojan
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 135 |
| First Seen: | March 22, 2012 |
| Last Seen: | August 2, 2021 |
| OS(es) Affected: | Windows |
The Mousetrap Trojan is part of an elaborate chain of malware infections that attempt to steal your money and bank account information through a sophisticated malware attack involving multiple components. According to ESG security analysts, the Mousetrap Trojan involves a series of malicious downloads that allow criminals to circumvent many tactics that security software uses to identify and remove Trojans and other malware. Basically, the Mousetrap Trojan infection begins through a Java applet infection that takes advantage of vulnerabilities in Adobe Flash Player in order to trick the victim's computer system into downloading a malicious executable file (with the EXE extension). These Java applets tend to be found in compromised websites that are otherwise not associated with malware, although they may also be found on dangerous attack websites designed for the sole purpose of delivering this malware onto the victim's computer system. The next step is the installation of a downloader Visual Basic Trojan which connects to one of dozens different IP addresses in order to install a banker Trojan on the victim's computer system. This banker Trojan makes changes to the Windows Registry, which forces the infected computer system to start Mousetrap Trojan automatically when Windows is launched.
Table of Contents
The Mousetrap Trojan Attack Does Not Stop with the Installation of the Banking Trojan
Installing the Mousetrap Trojan banking component is not the end of the Mousetrap Trojan attack. Once installed, Mousetrap Trojan will connect to another list of malicious IP addresses in order to update itself and ensure that Mousetrap Trojan can be reinstalled once Mousetrap Trojan is removed. Once Mousetrap Trojan does this, Mousetrap Trojan deletes itself! This makes Mousetrap Trojan nearly impossible for security software and PC security researchers to gain access to this banking Trojan in order to study Mousetrap Trojan. For example, being able to access its hard-coded list of malicious IP addresses would be essential for malware analysts to be able to identify and block these dangerous links. The way the Mousetrap Trojan attack works is by replacing the login form for many banks with a fake website designed to imitate the real thing. The victim enters their data into a bogus login form which then sends this data to criminals behind the Mousetrap Trojan attack. Like most malware threats, the Mousetrap Trojan attack can be thwarted with the help of a reliable anti-virus program that is fully updated with the latest malware definitions.
SpyHunter Detects & Remove Mousetrap Trojan
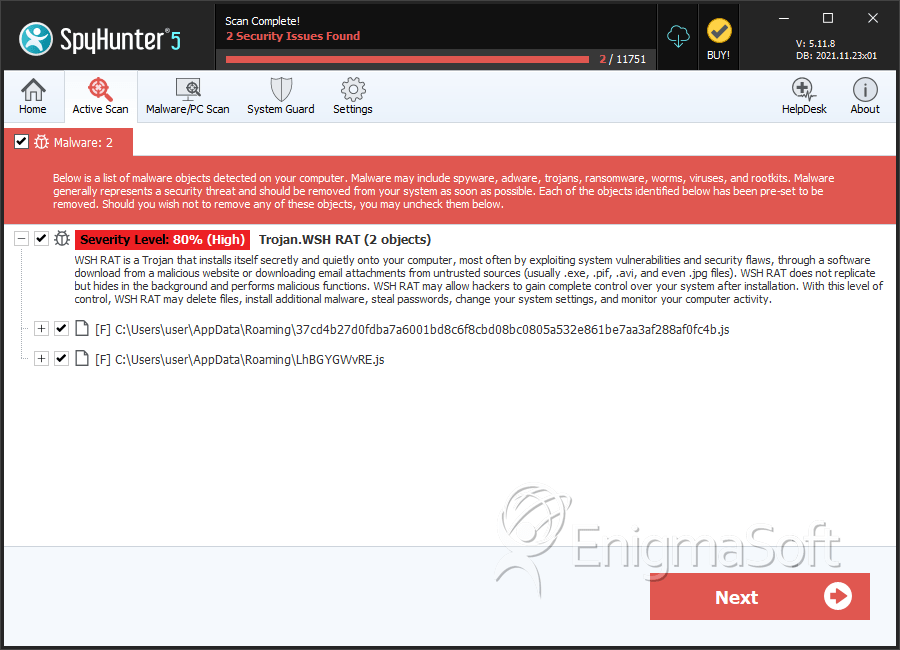
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 37cd4b27d0fdba7a6001bd8c6f8cbd08bc0805a532e861be7aa3af288af0fc4b.js | 0734d82c472d619bb304954fe29b569c | 14 |
| 2. | LhBGYGWvRE.js | 417966e39f3611d46c46b04e956a3ac0 | 9 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.