Keyboy
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 6 |
| First Seen: | June 13, 2013 |
| Last Seen: | February 20, 2020 |
| OS(es) Affected: | Windows |
Keyboy is a backdoor Trojan that has been used to target computer users in Asian countries. Keyboy attacks have been uncovered in China, India, Vietnam, Taiwan and a number of other countries in the region. Keyboy is distributed using the Microsoft Word documents with an exploit that allows criminals to execute a malicious code on the victim's computer. Keyboy is designed to steal sensitive information from the victim, including online passwords and banking information. The fact that Keyboy attacks are distributed using malicious Word documents means that these can be attached to emails specifically crafted to convince a victim to open the malicious attachment. Since many computer users ignore that DOC files can be malicious, thinking that only EXE and other executable can be used to execute the malicious code, they are more likely to open these malicious attachments than with other types of attacks.
Table of Contents
Keyboy’s Intended Targets
One example of a Keyboy attack included a malicious document written in Vietnamese that was clearly targeted to academics in Vietnam. A second example of Keyboy attacks includes a document with information on India's telecommunication's industry, meaning that its targets may include government officials and telecommunications companies. In both cases, these documents attempt to exploit known vulnerabilities in Microsoft Office. An important detail that should be noted is that these vulnerabilities have been patched in recent versions of Microsoft Office and will only target computers using an outdated version of this office suite. The purpose of these attacks is to install Keyboy, a backdoor Trojan that allows criminals to gain access to the infected computer.
Once installed, Keyboy steals passwords and other sensitive information stored on the victim's web browser. Keyboy also includes a keylogger component that tracks all information typed on the infected computer's keyboard and components that allow a remote party to browse files on the infected computer and spy on its activities. Using Keyboy, criminals can gain complete access to the compromised machine from a remote location. Keyboy attacks have been used to target specific people in Asia, including minorities in China and government officials. While the Keyboy component itself is not particularly complicated, its targeted distribution method makes Keyboy highly effective. Today, many malware developers have understood that creating advanced malware is often not as effective as being able to exploit social engineering and tricking computer users themselves into doing all of the work instead.
SpyHunter Detects & Remove Keyboy
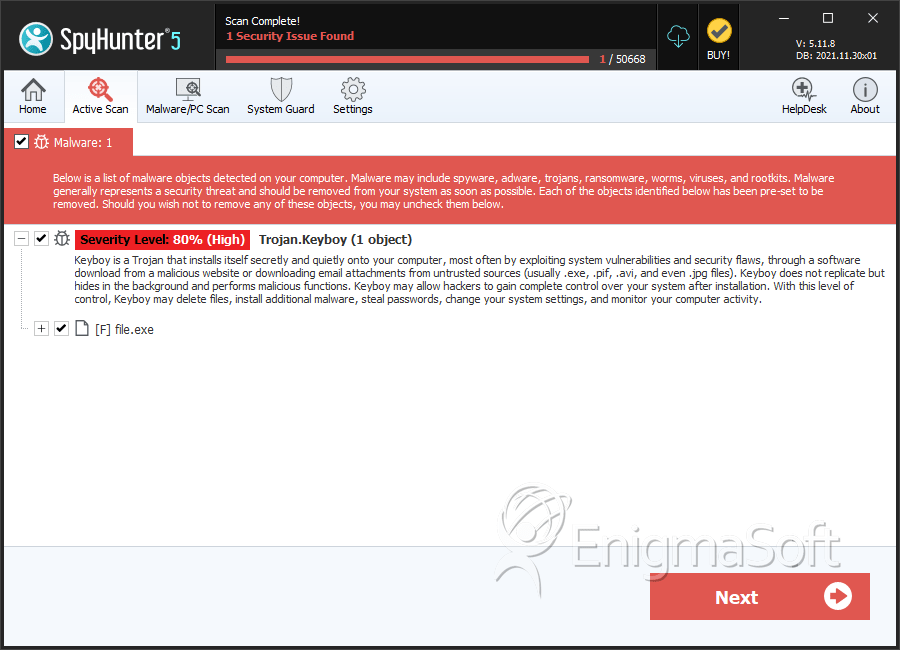
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 23d284245e53ae4fe05c517d807ffccf | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.