JS/Exploit-Blacole
JS/Exploit-Blacole is a dangerous JavaScript exploit that is used to install powerful rootkits on its victims' computers. JS/Exploit-Blacole carries out its attack by taking advantage of a known vulnerability in the Java Runtime Environment. This vulnerability is present in both Oracle Java SE and in Java for Business. Using this exploit, criminals can execute malicious code on the infected computers. Although the vulnerabilities exploited by JS/Exploit-Blacole have been patched in recent versions of the Java Runtime Environment, many computer users still run outdated versions of Java that are vulnerable to JS/Exploit-Blacole. In fact, the JS/Exploit-Blacole infection first appeared in the Russian Federation where criminals used JS/Exploit-Blacole to exploit these very same outdated versions of Java running on computer users' machines. JS/Exploit-Blacole was disseminated through compromised websites that would run the malicious script on the victim's computer.
The JS/Exploit-Blacole attack typically occurs when the victim visits a compromised website. This means that the first step for criminals using JS/Exploit-Blacole is by gaining access to a mainstream website, typically by exploiting weak passwords or security measures. Once this is done, criminals will install the JS/Exploit-Blacole malicious script on the infected website. This, in turn, means that all computer users accessing this website with a web browser using an outdated version of Java will become infected. The JS/Exploit-Blacole script will run on visitors' computers and, using this vulnerability in Java, will execute malicious code that allows JS/Exploit-Blacole to drop other malicious files on the victim's computer.
Table of Contents
Consequences of Being Exposed to the JS/Exploit-Blacole Exploit
The JS/Exploit-Blacole exploit is typically used to install dangerous bootkits on the infected computer. These will typically include a banking Trojan designed to steal online banking data and credit card numbers. These kinds of malware infections will also typically be distributed using spam email, meaning that your computer may be used to send out spam email messages. It is important to understand that conventional anti-virus programs may have a hard time detecting the presence of the kinds of rootkit infections that have been associated with the JS/Exploit-Blacole exploit. Because of this, ESG malware analysts exhort PC users to use a specialized anti-rootkit tool to ensure that their computer has not been compromised. To prevent attacks involving JS/Exploit-Blacole, it is advisable to keep your version of Java updated and to disable JavaScript unless it is necessary.
SpyHunter Detects & Remove JS/Exploit-Blacole
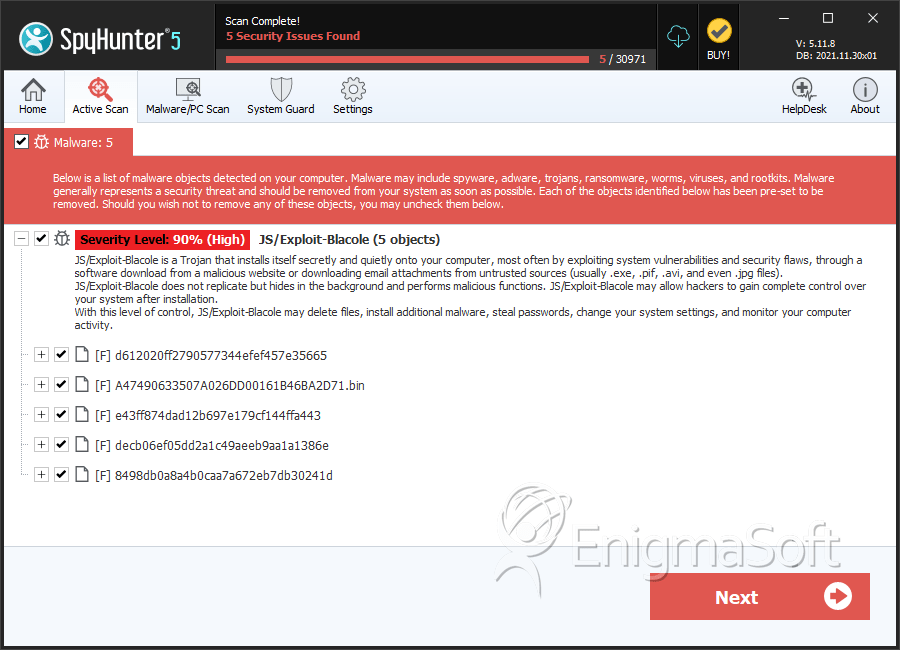
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | g43kb6j34kblq6jh34kb6j3kl4.jar | ||
| 2. | d612020ff2790577344efef457e35665 | d612020ff2790577344efef457e35665 | 0 |
| 3. | A47490633507A026DD00161B46BA2D71.bin | a47490633507a026dd00161b46ba2d71 | 0 |
| 4. | e43ff874dad12b697e179cf144ffa443 | e43ff874dad12b697e179cf144ffa443 | 0 |
| 5. | decb06ef05dd2a1c49aeeb9aa1a1386e | decb06ef05dd2a1c49aeeb9aa1a1386e | 0 |
| 6. | 8498db0a8a4b0caa7a672eb7db30241d | 8498db0a8a4b0caa7a672eb7db30241d | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.