Hackers Behind HolyCrypt Fumble Its Creation but Still Manage to Conjure Potent Ransomware
 It is not very often that cyber-security researchers get their hands on a beta version of malware that is yet to be unleashed on users, yet that is exactly what happened in late July with a threat called HolyCrypt Ransomware. In an intriguing turn of events, AVG security researcher, Jakub Kroustek, managed to acquire an unfinished version of the now infamous HolyCrypt Ransomware discovering some interesting facts about the fumbled ransomware creation.
It is not very often that cyber-security researchers get their hands on a beta version of malware that is yet to be unleashed on users, yet that is exactly what happened in late July with a threat called HolyCrypt Ransomware. In an intriguing turn of events, AVG security researcher, Jakub Kroustek, managed to acquire an unfinished version of the now infamous HolyCrypt Ransomware discovering some interesting facts about the fumbled ransomware creation.
July was a busy month, for both cyber-criminals and the IT security researchers who opposed said crooks at every turn. So, what's so special about the HolyCrypt Ransomware?
Well, for starters, this is one of the very few instances that researchers have managed to get an unfinished version of a serious threat so they can study its code and learn more about the mindset and practices of its creator. Then there's the fact that HolyCrypt Ransomware is Python based and 64-bit, which is unusual in the current landscape of traditional encryption type ransomware.
Unfortunately, the impressive actions of Jakub Kroustek have not allowed IT security experts to make HolyCrypt Ransomware completely irrelevant, but IT specialists have since then managed to gain valuable insight for the detection and prevention of HolyCrypt Ransomware infections.
Table of Contents
What Is HolyCrypt Ransomware?
HolyCrypt Ransomware is malware commonly spread through spam email attachments or malicious website exploits. It targets PCs running the Windows operating system, and once it infects a device it runs in the background and dumps 'hidden' copies of itself in various locations, including the following:
- %User's Profile%
- %Local%
- %Temp%
- %AppData%
- %SystemDrive%
- %SystemRoot%
- %LocalAppData%
- %ProgramData%
- %WinDir%
HolyCrypt Ransomware manages to drop several copies of itself to ensure its perseverance on the infected device, then quickly makes certain changes to the following registry keys:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Runonce
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices
- HKEY_CURRENT_USER\Control Panel\Desktop
The changes made by HolyCrypt assure that it is running in the background upon startup, enabling it to achieve its ultimate goal, which is to encrypt valuable files stored on the infected computer's hard drive. The so called 'test' version that IT security specialists initially got their hands on was relatively limited as to the files it targets for encryption, such as .txt, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .jpg, .png, .csv, .sql, .mdb, .sln, .php, .asp, .aspx, .html, .xml, and .psd.
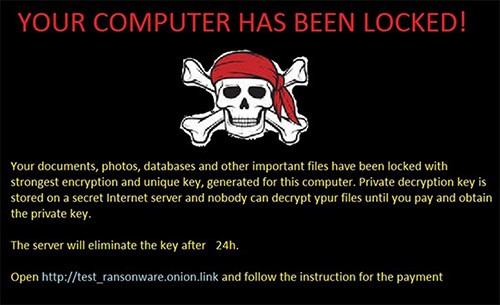
The list of targeted file types above has been expanded in the versions of HolyCrypt Ransomware that now plague users worldwide. HolyCrypt Ransomware uses a nearly undefeatable RSA and AES encryption algorithm to encrypt any and all files it detects on the infected device. Once the encryption process is completed, it replaces the machine's desktop background with the following threatening note:
YOUR COMPUTER HAS BEEN LOCKED!
Your documents, photos, databases and other important files have been locked with strongest encryption and unique key, generated for this computer. Private decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay and obtain the private key.
The server will eliminate the key after 24h.
Open http://test_ransonware.onion.link and follow the instruction for the payment
Following the cyber-criminals' instructions eventually leads to their demands – namely, they demand that the user pay 0.5-1.5 Bitcoin (currently, 1 Bitcoin is equivalent to approximately $660) in order to get their data back.
How Does HolyCrypt Ransomware Infect a Device?
HolyCrypt Ransomware uses variable vectors of infection – anything from corrupted links and drive-by downloads to Trojans. However, as with most other ransomware threats out there, the most common vector of infection seems to be the 'spam e-mail attachment' method . Usually, the user receives a suspicious e-mail with a file attached whose name reads something along the lines of 'ReportXYZ.pdf.exe.', where infection occurs if the user is careless enough to download a suspicious file.
How to Prevent HolyCrypt Ransomware Attacks?
Usually, not opening suspicious correspondence reduces the risk of HolyCrypt Ransomware infection dramatically. Keeping an up-to-date version of a legitimate anti-malware program makes the infection even less likely.
What to Do in Case of a HolyCrypt Ransomware Attack?
IT security specialists recommend that once a HolyCrypt Ransomware infection becomes apparent, users should adhere to the following guidelines:
- Do not pay the criminals – although the ransom note is threatening and losing data might be devastating, complying with the cyber-criminals' demands is ill advised and not guaranteed to produce the desired outcome.
- Clean your device – rooting out a HolyCrypt Ransomware infection can be done easily with legitimate malware removal tools. Alternatively, it can be done manually in safe mode, but doing so is guaranteed to require a lot of time and effort, not to mention, high levels of IT proficiency, and may not always work due to the fact that HolyCrypt Ransomware tends to dump copies of itself all over the infected device's hard drive. Restore data via Shadow Volume Copies – unlike some of the more vicious and thorough examples of ransomware, HolyCrypt ransomware does not attack Shadow Volume Copies, which means that an IT specialist may be capable of recovering some of the files that were stored on the device. Unfortunately, success is not always guaranteed.
- Retain the encrypted data –there is no reliable way to decrypt files encrypted with HolyCrypt Ransomware. However, that doesn't necessarily mean that one won't be devised by IT specialists in the future. It is advisable that irreplaceable data that has been encrypted should be saved and preserved, rather than deleted. Since HolyCrypt Ransomware augments, but otherwise keeps the names of the files pretty much intact, users can pick and choose what to preserve in the hope that a decryption tool will be made at some point in the future.