DarkComet
DarkComet is a malware threat that has started to proliferate since the beginning of 2012. ESG security researchers have found that DarkComet is strongly associated with the conflict between political dissidents and the Syrian government. Basically, DarkComet is a full-fledged remote access Trojan (RAT), which allows a remote party to connect to the infected computer system and use it from afar. With full access to the victim's computer system, hackers can basically steal any information on the infected computer or use it for their own means. DarkComet uses a vulnerability in Skype, the popular online chat application, in order to spread. Whenever DarkComet's executable file runs, it connects to a server located in Syria from which DarkComet receives updates, instructions and the files DarkComet needs to take over the victim's computer system. ESG security analysts have associated this Syrian server's IP address to a range of IP addresses officially belonging to the Syrian government's agency for telecommunications. This raises suspicions connecting the Syrian government to the use of DarkComet to take out its oppositions' computer systems. One of the most characteristic features of the Arab Spring movement is the fact that they use online social networks and rely heavily on programs like Skype to communicate, it does not seem farfetched that the Syrian government would try to use malware to disrupt their opposition's activities. In fact, this is not something new; a branch of regime supporters known as the 'Syrian Electronic Army' has already been known to attempt to disrupt the opposition movement by attacking websites and Facebook pages associated with the Syrian opposition movement.
Table of Contents
An Overview of a DarkComet Attack
DarkComet is not exclusive to the Syrian conflict and is a remote access Trojan that is widely available. Using DarkComet, an intruder can use the infected computer's webcam to take pictures and video, use the infected computer's microphone to eavesdrop on the victim and also take over the victim's computer system in order to steal data. DarkComet also is able to track keystrokes on the infected computer and allow criminals to transfer files into and out of the infected computer. With this level of control, the damage a hacker can do using DarkComet is unlimited. Through Skype chat, hackers spread files using a Facebook icon which actually contain executable files designed to install DarkComet on the infected computer system.
SpyHunter Detects & Remove DarkComet
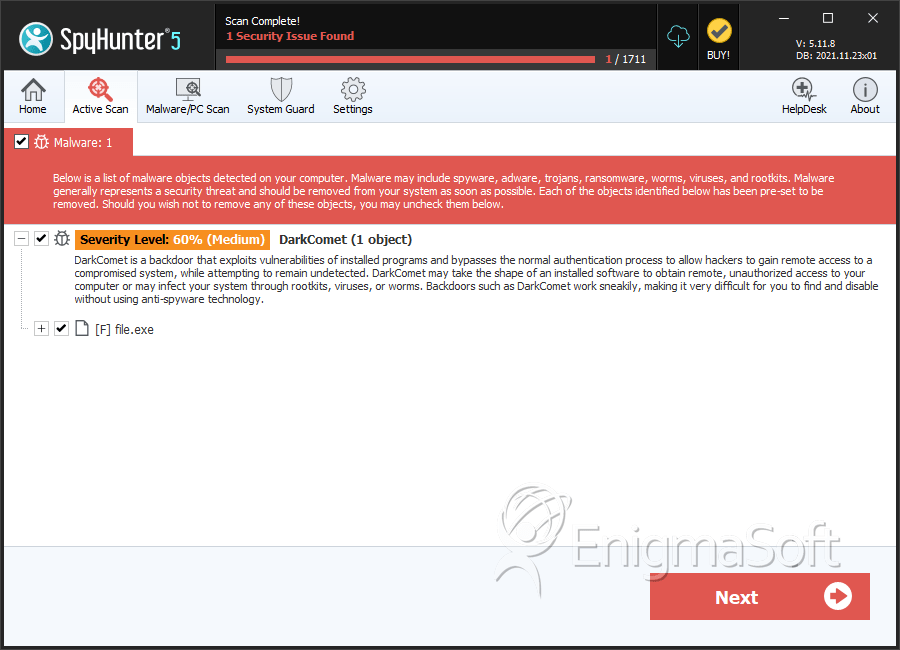
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | df99555ed03c85f24ee6ec5fa7f247f0 | 0 |
| 2. | file.exe | b3564ea90d834233262d346cefd6c646 | 0 |
| 3. | file.exe | a011d77bf6be4981223c6148e8834e65 | 0 |
| 4. | file.exe | 95c809facbc97a5afa87759dbcef9ed0 | 0 |
| 5. | file.exe | 14172555f98559c019695673d2ffe9eb | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.