Cyber_baba2@aol.com Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 29 |
| First Seen: | August 30, 2016 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The Cyber_baba2@aol.com Ransomware is a new adaptation of the Crysis Ransomware that is similar in behavior to the Mahasaraswati Ransomware. Both cryptomalware follow an India-based theme and are known to infect server systems primarily. The Cyber_baba2@aol.com Ransomware may be deployed to users via corrupted attachments to spam email Trojan droppers like Rovnix. The main executable of the Cyber_baba2@aol.com Ransomware is known to run from the Windows directory and might mask its process under svchost.exe signed by Microsoft Corp.
The Cyber_baba2@aol.com Ransomware is using an industry-grade encryption algorithm to lock the victims' data and leave them unable to read the corrupted data. The Cyber_baba2@aol.com Ransomware will scan the PC for a list of available drives and begin the encryptions process if it is not detected by your AV scanner. Security investigators note the the Cyber_baba2@aol.com Ransomware may lock the following file types:
.PNG, .PSD, .PSPIMAGE, .TGA, .THM, .TIF, .TIFF, .YUV, .AI, .EPS, .PS, .SVG, .INDD, .PCT, .PDF, .XLR, .XLS, .XLSX, .ACCDB, .DB, .DBF, .MDB, .PDB, .SQL, .APK, .APP, .BAT, .CGI, .COM, .EXE, .GADGET, .JAR, .PIF, .WSF, .DEM, .GAM, .NES, .ROM, .SAV, .DWG, .DXF, .GPX, .KML, .KMZ, .ASP, .ASPX, .CER, .CFM, .CSR, .CSS, .HTM, .HTML, .JS, .JSP, .PHP, .RSS, .XHTML, .DOC, .DOCX, .LOG, .MSG, .ODT, .PAGES, .RTF, .TEX, .TXT, .WPD, .WPS, .CSV, .DAT, .GED, .KEY, .KEYCHAIN, .PPS, .PPT, .PPTX, .INI, .PRF, .HQX, .MIM, .UUE, .7Z, .CBR, .DEB, .GZ, .PKG, .RAR, .RPM, .SITX, .TAR.GZ, .ZIP, .ZIPX, .BIN, .CUE, .DMG, .ISO, .MDF, .TOAST, .VCD, .SDF, .TAR, .TAX2014, .TAX2015, .VCF, .XML, .AIF, .IFF, .M3U, .M4A, .MID, .MP3, .MPA, .WAV, .WMA, .3G2, .3GP, .ASF, .AVI, .FLV, .M4V, .MOV, .MP4, .MPG, .RM, .SRT, .SWF, .VOB, .WMV, .3D, .3DM, .3DS, .MAX, .OBJ, R.BMP, .DDS, .GIF, .JPG,.CRX, .PLUGIN, .FNT, .FON, .OTF, .TTF, .CAB, .CPL, .CUR, .DESKTHEMEPACK, .DLL, .DMP, .DRV, .ICNS, .ICO, .LNK, .SYS, .CFG.
As stated above, the Cyber_baba2@aol.com Ransomware is similar to Mahasaraswati and will show a custom wallpaper on your screen when the encoding process is complete.The image used by the Cyber_baba2@aol.com Ransomware features a monk clothed in an orange robe and carrying a steel staff. On the right side of the monk is the following message:
'HELLO MY FRIEND
ALLYOUR DATA HAS BEEN ENCRYPTED
YOUR SERVER HAS A SECURITY PROBLEM
TO GET YOUR DATA BACK AND PROTECT
YOUR SYSTEMSYTEM WRTE TO TO
CYBER_BABA2@AOL.COM'
The wallpaper will be located in the My Documents library, and the text version of the ransom message will be available in How to decrypt your files.txt placed on the desktop. Security analysts advise against writing to Cyber_baba2@aol.com because you may be suggested to pay thousands of dollars for the release of a decryption tool and may not receive one after paying. We should add that the Cyber_baba2@aol.com Ransomware does not encode data on protected drives, and you should rely on backups and archives to restore the operations on your server. Keep in mind that you will need to clean sweep your machine with a trustworthy anti-malware suite to make sure the Cyber_baba2@aol.com Ransomware is deleted. Do not forget to change the passwords used to access the server network.
SpyHunter Detects & Remove Cyber_baba2@aol.com Ransomware
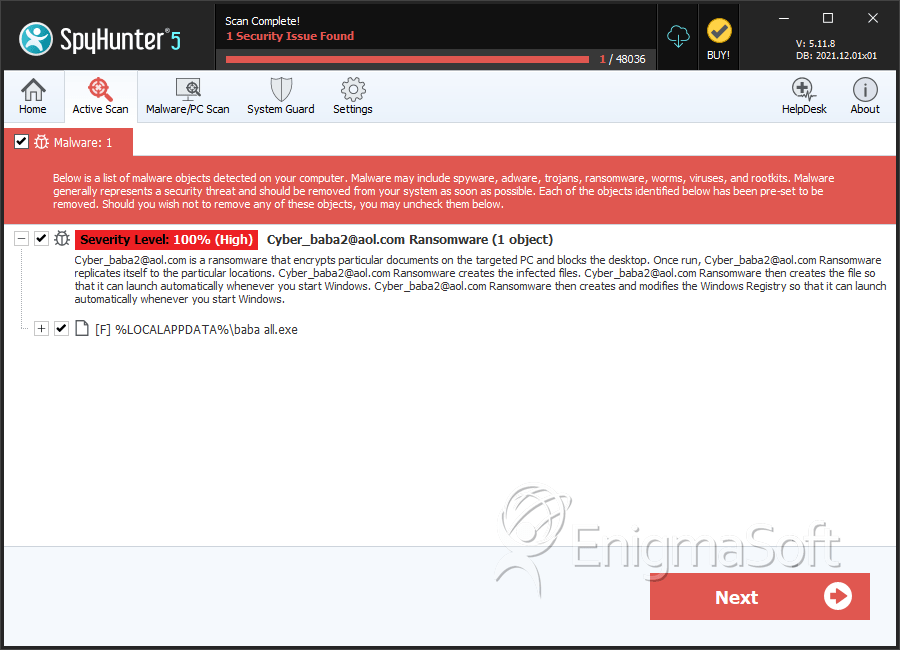
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | baba all.exe | 458c1cbd0ff849119214e739d8815f37 | 27 |
