Cryptobyte Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 8 |
| First Seen: | April 20, 2017 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The Cryptobyte Ransomware is a ransomware Trojan that has been distributed through spam email attachments since April 2017. The Cryptobyte Ransomware is a variant of CryptXXX and BTCWare, with some updated elements. These ransomware Trojans have been around since March 2016. The Cryptobyte Ransomware is designed to target computers running the Windows operating system (Windows 7 and later, both int heir 32-bit and 64-bit versions). The Cryptobyte Ransomware may be delivered through text documents that contain corrupted scripts, which download and install the Cryptobyte Ransomware on the victim's computer.
Table of Contents
How the Cryptobyte Ransomware Carries out Its Attack
The Cryptobyte Ransomware uses a combination of the AES and RSA encryptions to make the victim's files inaccessible completely. Once the Cryptobyte Ransomware encrypts the files, they become unreadable and will show up as blank icons. The Cryptobyte Ransomware will mark the affected files with the file extension '.[btc.com@protonmail.ch].cryptobyte' and '.[no.xm@protonmail.ch].cryptobyte' markers, depending on the exact version of the Cryptobyte Ransomware. The Cryptobyte Ransomware will encrypt a wide variety of file types, which may include the following:
.3gp, .7z, .apk, .avi, .bmp, .cdr, .cer, .chm, .conf, .css, .csv, .dat, .db, .dbf, .djvu, .dbx, .docm, ,doc, .epub, .docx .fb2, .flv, .gif, .gz, .iso .ibooks,.jpeg, .jpg, .key, .mdb .md2, .mdf, .mht, .mobi .mhtm, .mkv, .mov, .mp3, .mp4, .mpg .mpeg, .pict, .pdf, .pps, .pkg, .png, .ppt .pptx, .ppsx, .psd, .rar, .rtf, .scr, .swf, .sav, .tiff, .tif, .tbl, .torrent, .txt, .vsd, .wmv, .xls, .xlsx, .xps, .xml, .ckp, .zip, .java, .py, .asm, .c, .cpp, .cs, .js, .php, .dacpac, .rbw, .rb, .mrg, .dcx, .db3, .sql, .sqlite3, .sqlite, .sqlitedb, .psd, .psp, .pdb, .dxf, .dwg, .drw, .casb, .ccp, .cal, .cmx, .cr2.
The Cryptobyte Ransomware delivers its ransom note in an INF file named '#_HOW_TO_FIX.inf. This ransom note contains the following message:
'All your files have been encrypted
If you want to restore them, write us to the e-mail: no.xm@protonmail.ch
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
FREE DECRYPTION AS GUARANTEE
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information
end their total size must be less than 10Mb
Attention! Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
Your ID:
[RANDOM CHARACTERS]'
Dealing with the Cryptobyte Ransomware Infection
Unfortunately, it may not be possible to decrypt files that have been encrypted in the Cryptobyte Ransomware attack. Considering this, the best protection against the Cryptobyte Ransomware and similar attacks is to have file backups on offline devices or the cloud (not synchronized with the main computer to prevent the backups themselves from becoming encrypted). Malware experts do not advise computer users to pay the Cryptobyte Ransomware ransom. The con artists may not keep their promise to restore the affected files, often asking for more money, ignoring the ransom payment, or encrypting the files again after a short time. Furthermore, paying the Cryptobyte Ransomware ransom finances these people's activities, allowing them to carry out additional attacks against computer users. The Cryptobyte Ransomware attacks can be prevented with the help of a security program, which can intercept the Cryptobyte Ransomware infection before it encrypts the victim's files. It is also a necessary move to educate computer users in the correct handling of email attachments and how to recognize known email tactics since this is the primary way in which the Cryptobyte Ransomware and most ransomware Trojans are distributed. A combination of safe browsing and handling of email and a strong security program can help stop more ransomware attacks and, in the case of a successful infection, having file backups will nullify the effects of the attack and allow easy recovery completely.
SpyHunter Detects & Remove Cryptobyte Ransomware
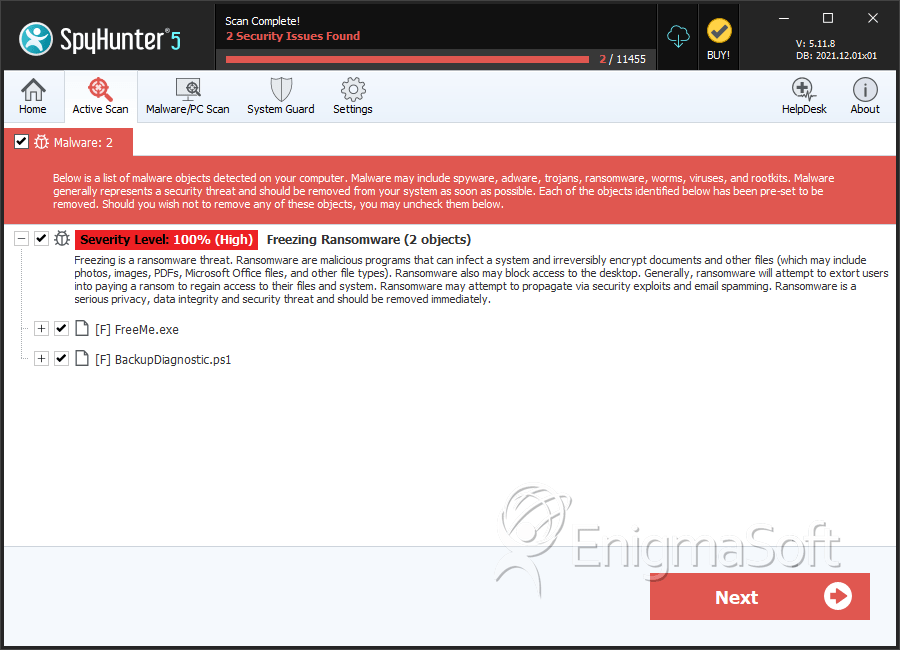
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | FreeMe.exe | e14ef0817916264acba4ae6fae24230e | 4 |
| 2. | BackupDiagnostic.ps1 | 312a72eced44c4231fc3ea7a1940a700 | 0 |
